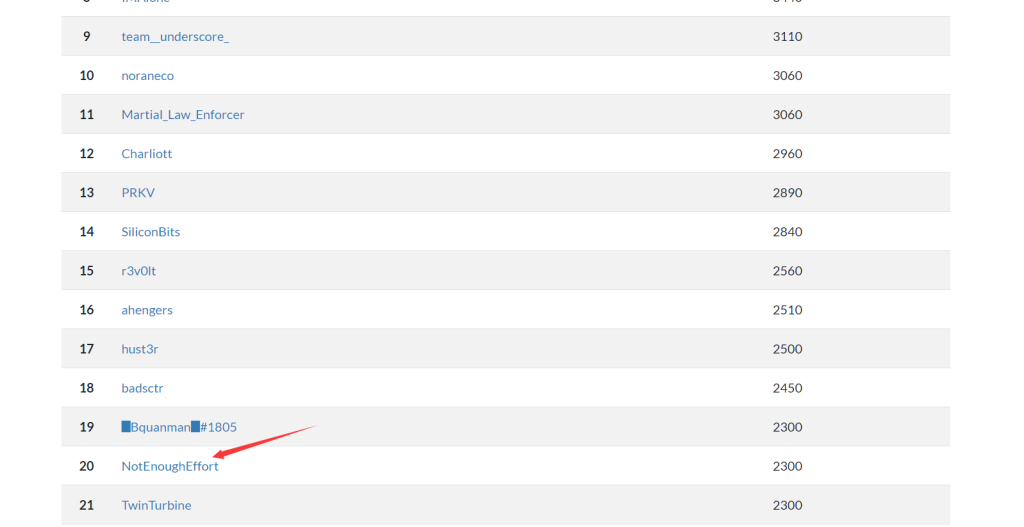
This time I play the game in the name of NotEnoughEffort,and we ended up in 20th place
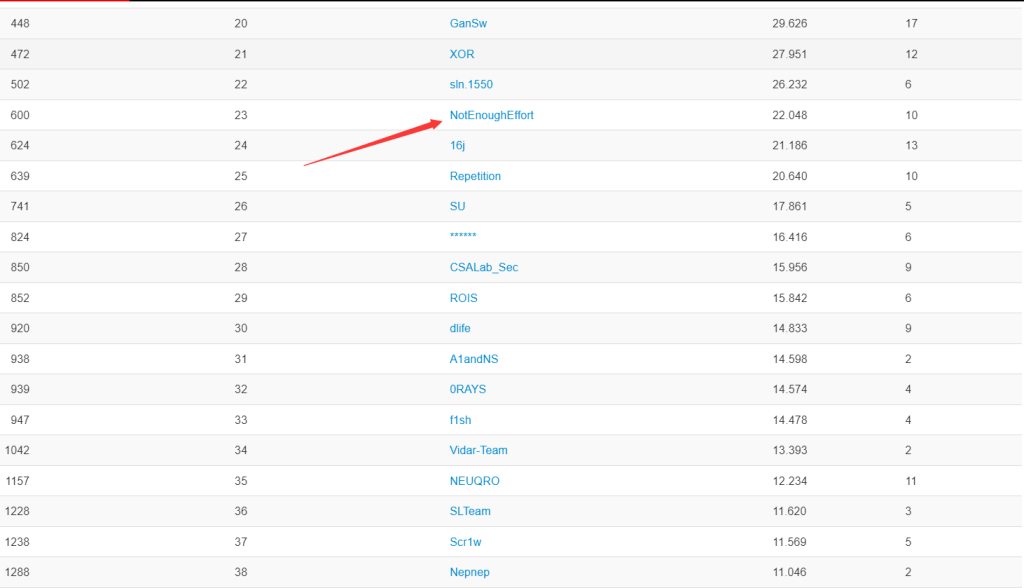
This game added more than ten points to us, which means we have now surpassed a group of well-known strong teams and ranked 23rd in the China region on CTFTime🤣🤣
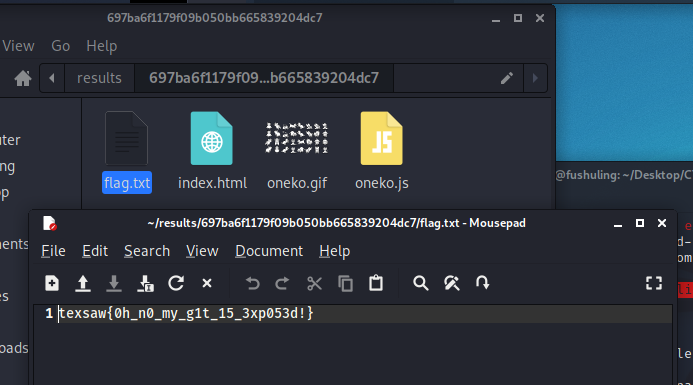
Forensics
Lazy Admin
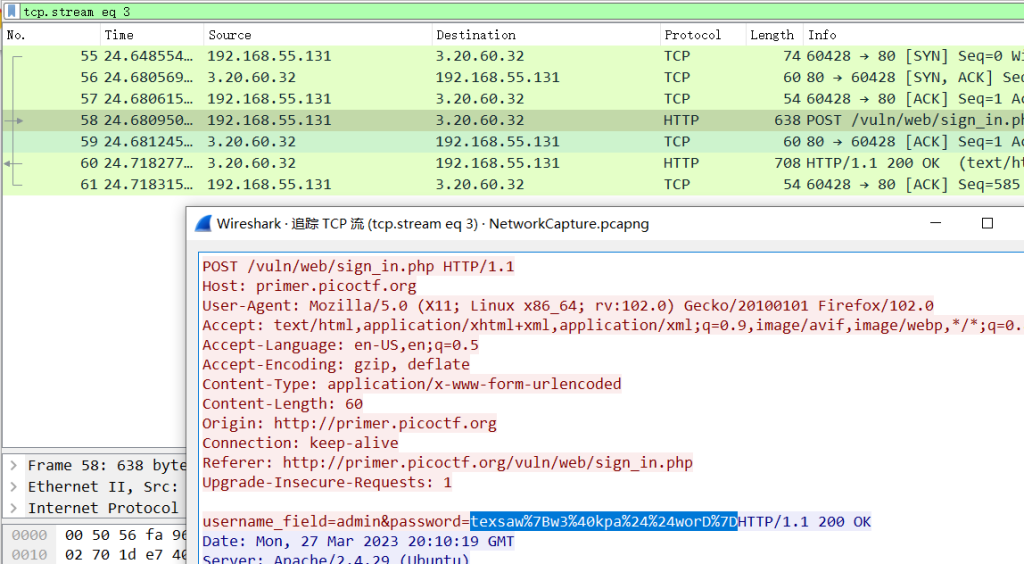
Decode the URL to obtain the answer:
texsaw{w3@kpa$$worD}Not Obvious
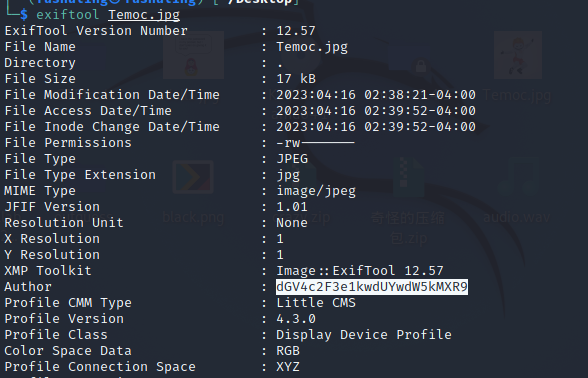
Base64 decoding results in flag
texsaw{Y0uF0und1t}Osmium
After downloading the attachment, the 010 Editor found that it was a compressed package. After changing it to. zip, it can indeed be decompressed. After decompressing, there is also a rock. lock and a txt file, so it is speculated to be a cyclic decompression. Simply scan the directory first, rename the. lock file to. zip file, and then extract the. lock file from the extracted folder and place it in the original directory and delete the previously renamed rock. zip file, After repeating 491 times, an error will be reported and it will be found that there is a rock. zip file that is not a compressed package. You can use the 010 Editor to obtain the flag
import os
import shutil
import time
def scan_file():
for f in os.listdir(): #Since this is the current path, it is necessary to place this code file in the same folder as the file you want to process
if f.endswith('.rock'):
return f
def unzip_it(f,i):
folder_name = f.split('.')[0]+str(i)
target_path = os.path.join('.',folder_name)
os.makedirs(target_path)
shutil.unpack_archive(f,target_path)
def delete(f):
os.remove(f)
if name == '__main__':
i = 1
while True:
zip_file = scan_file()
# print(zip_file)
if zip_file:
os.rename(zip_file,'rock.zip')
unzip_it('rock.zip',i)
delete('rock.zip')
os.rename('E:\\test\\rock'+str(i)+'\\rock.rock','E:\\test\\rock.rock')
i += 1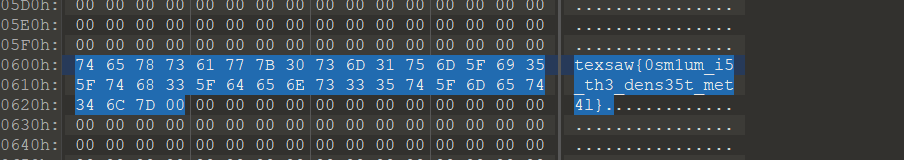
Ghost in the Clipboard
The ClipboardPayload in ActivitiesCache.db stores the base64 encoded clipboard data, which can be unpacked(AppData\Local\ConnectedDevicesPlatform\4f406c0d314b1399)
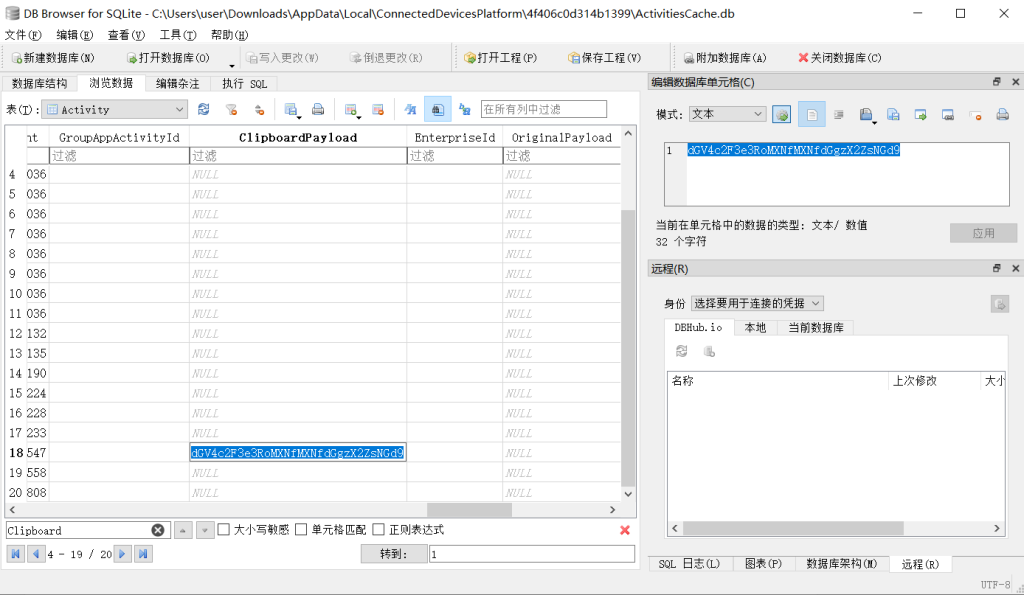
texsaw{th1s_1s_th3_fl4g}MISC
Get Docxed
You can use binwalk to separate a zip file and obviously, this c_ r_ a_ z_ y. Zip hides flag
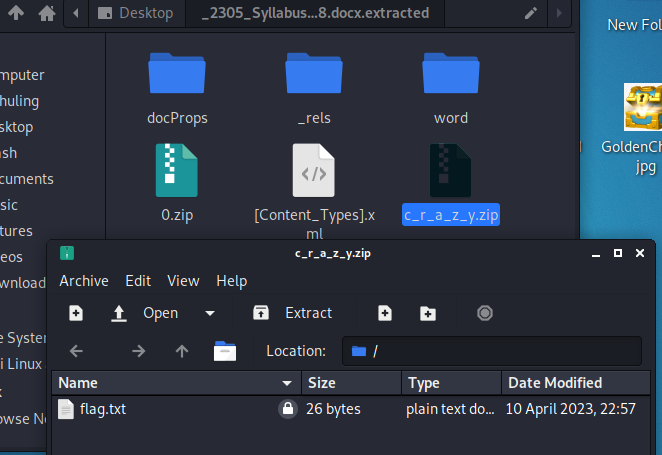
Then use rockyou. txt to explode and obtain the answer
Leaking Secrets?
Just view the modification records
Dial Tones
After DTMF recognition of wav, it is obtained that:469096804666202280545308428.
Next, you need to contact the background of the question because it was still in the era of using Nokia phones, and the numbers we obtained obviously wouldn’t be phone numbers, so we can only use T9 to write different words using the nine numbers on the keyboard.
For T9,https://www.dcode.fr/t9-cipher this one works,Choose the words with the most normal word order to form a sentence, and the final flag is texsaw{howyougonnaactlikethat}
Cryptography
A Prime Problem
Just use Fermat’s theorem decomposition and you will get the answer:
import gmpy2
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
import Crypto.Util.number as number
with open("public.pem", "rb") as f:
key = RSA.import_key(f.read())
public_key = key.publickey()
def fermat(n):
a = gmpy2.isqrt(n) + 1
b = a**2 - n
while not gmpy2.iroot(b, 2)[1]:
a += 1
b = a**2 - n
b = gmpy2.iroot(b, 2)[0]
return (a + b, a - b)
# p, q = fermat(public_key.n)
q = 4035344634524837717521915201305975516098722420219128355538063452416706649582040976771180219125686195204822338707859330665951615120601874544633270967788027074091717031306682541328304029835373501410605229741692482939694335870993275374022062842280710959945654503477963936519342817858077479358738644573785487521029281727169737762573882938206926732178158574479009658125467551018805835614097299871918962876012823726564585700892649184624360581540320684057939677927710690697605112273648424114803479675168145732275761455167827091548475299338153944131864072448859112796081669111927011416022032734279963320442672954117725635057
p = 4035344634524837717521915201305975516098722420219128355538063452416706649582040976771180219125686195204822338707859330665951615120601874544633270967788027074091717031306682541328304029835373501410605229741692482939694335870993275374022062842280710959945654503477963936519342817858077479358738644573785487521032731949949672190534185116624273887980672650136436463485817603675820435108916629224182933010010760147581441906729024860231015150938247223056724681089282171956429028890246653926215568565285817362035961064914955470989239448342478747578795441253265938399505855471220563759562310196608723984550303265351501013993
e = 7
# Calculate n and d, where n is the RSA modulus and d is the private key index
n = p * q
phi = (p - 1) * (q - 1)
d = pow(e, -1, phi) # Using the pow function to calculate the inverse of e
#Generate RSA key pairs
key_pair = RSA.construct((n, e, d, p, q))
# Using RSA to decrypt ciphertext
cipher_rsa = PKCS1_OAEP.new(key_pair)
with open("key_gen_flag.bin", "rb") as f:
cipher_text = f.read()
decrypted_text = cipher_rsa.decrypt(cipher_text)
print(decrypted_text)Web
The Path to Victory
You will move to http://18.216.238.24:1003/webpage/files/dir/index.html when you visit the webpage given by the title.You can change the url to http://18.216.238.24:1003/webpage/ and you will find the webpage file directory.Then you can find flag in session_keys.txt.
Console Scrabble
There is a change.js on the webpage, I ran all the functions in the source code one by one in the webpage debugging function and finally obtained the flag.
Swiftmaster
When you access the provided URL, you can find a download button. After pressing it, you can obtain an image, and then view the detailed properties to obtain the flag
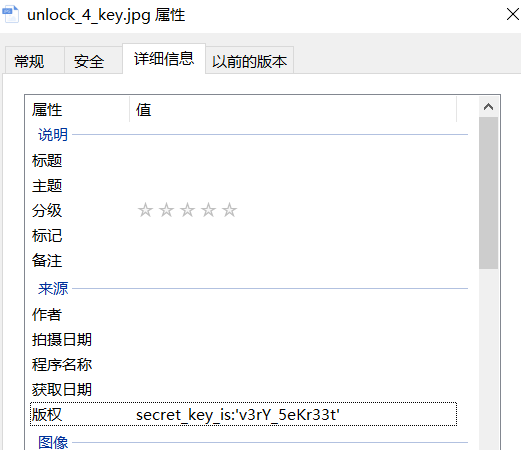
So th flag is texsaw{v3rY_5eKr33t}
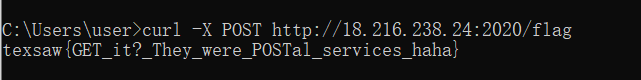
It’s a really strange challenge.When you get to http://18.216.238.24:2020/flag you will be redirected to another website.The way to solve it is just use POST:
curl -X POST http://18.216.238.24:2020/flag
MIT of The South
Visit the webpage http://18.216.238.24:1004/webpage/files/dir/robots.txt and you will see a prompt:
Robots!?
There are no robots here!
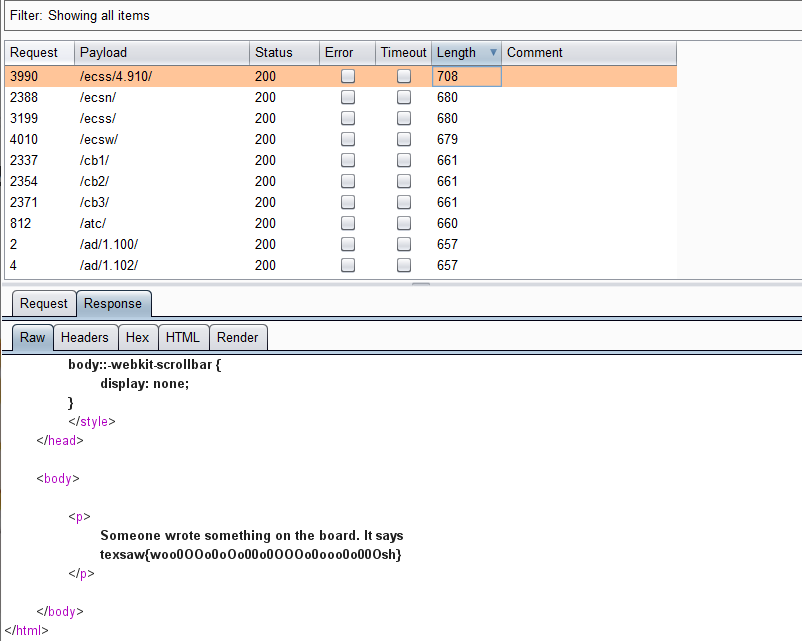
Only Temoc, and his army of tobors!!So get to http://18.216.238.24:1004/webpage/files/dir/tobors.txt and you will find that there is a large number of addresses stored here.Save them as a dictionary and use burpsuite for path blasting. Eventually, you will find flag in http://18.216.238.24:1004/webpage/files/dir/ecss/4.910/
Git er’ done
githacker –url http://18.216.238.24:1002/.git/ –output-folder ~/results